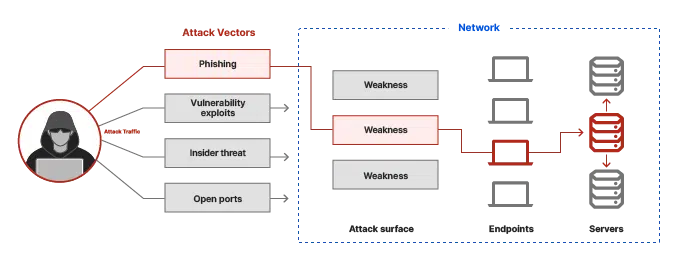
There are more entry points than ever through which today’s threat actors infiltrate organizations’ IT environments and gain unauthorized access. The expanding cyber attack surface is a byproduct of several factors, including multi-cloud adoption, hybrid workforces, increased IoT devices, and a software supply chain that increasingly depends on external, open-source code.
All these factors make it harder for organizations of all sizes in every industry to get the visibility needed to oversee their cyber attack surface, track their assets, and close off paths into their data and systems. To highlight one example, phishing attacks now cost businesses $14.8 million per year versus just $3.8 million back in 2015.
Aside from phishing, organizations must contend with malware, misconfigurations, unpatched vulnerabilities, supply chain risks, and credential compromises among the plethora of attack vectors that exploit any weaknesses or vulnerabilities in their attack surface.
Reducing the cyber attack surface is essential in discovering security gaps and closing them off before opportunistic threat actors find a way through them. Still, it requires thinking more broadly about the range of potential security exposures. Dealing with this challenge might sound daunting, but the simplified protection and reduced cyber risks are worth it. Here are eight actions to reduce your cyber attack surface immediately.
What is an Attack Surface?
An attack surface for any system or IT environment is the sum total of possible entry points that hackers can exploit to get inside. Another way to think of an attack surface is that it’s the external-facing elements of a system or environment that hackers can try to infiltrate, or, as NIST defines it, “the set of points on the boundary.”
Consider some examples of these boundary points that are commonplace in the attack surfaces of modern organizations:
- VPN accounts—used by remote employees to connect to business assets. These accounts are susceptible to takeover from stolen credentials, phishing emails targeting users with low cyber awareness, and other threats.
- Company websites—aside from being the digital face of a company, websites are potential sources of access to sensitive information or fraudulent transactions from expired SSL certificates and missing encryption. There is also the risk of domain hijacking.
- SaaS applications—different business units use a range of SaaS applications, many of them beyond the purview of IT teams who can’t track misconfigurations and other risks.
- Web applications—web apps often provide important customer/client-facing functionality for companies, but they are also at risk of compromise from outdated/vulnerable components.
- GitHub repositories—businesses often store proprietary code and other sensitive information in private GitHub repositories, which may be hacked.
- Cloud infrastructure—cloud infrastructure comes with misconfiguration risks and other potential security issues that leave data and systems exposed.
- Ports—businesses may leave open ports that run risky services vulnerable to exploits or unpatched. Hackers can scan for open ports with a range of widely available tools.
What is an Attack Vector?
An attack vector is any method or path that an unauthorized user exploits to enter a system and access the desired resources to achieve their goals. Attack vectors facilitate data exfiltration, ransomware installation, and other forms of cyber attack.
Examples of attack vectors include:
- Installing malware on a user’s device.
- Using social engineering techniques to gain access.
- Logging in to accounts with compromised credentials.
- Targeting systems that run unpatched vulnerabilities.
Why is a Large Attack Surface a Security Risk?
Larger attack surfaces give malicious actors more targets to aim for in their efforts to compromise your systems. Just one vulnerability or weak point can suffice for unauthorized access. And the larger the attack surface, the more potential points of security failure.
It’s not only the expanding nature of attack surfaces that adds security risks; it’s also that they are constantly shifting and getting harder to track. DevOps teams can spin up new infrastructure in seconds, creating new assets to monitor potential security weaknesses. As they test out and run new campaigns, marketing teams add new subdomains to organizations’ website portfolios.
Types of Attack Surfaces
| Type of Attack Surface | Description |
| Physical | All the physical endpoint devices that rogue actors can get physical access to and attempt to exploit (e.g.,., USB ports, employee laptops, workstations, servers) |
| Digital | The external-facing assets that are accessible with an Internet connection and may be compromised (e.g.,. cloud infrastructure, ports, websites) |
| Social Engineering | The total number of employees, end users, contractors, and business partners with access to business assets. Any person can be targeted with social engineering techniques that use psychological manipulation to trick them into taking specific actions that allow threat actors inside your IT environment. |
| IoT | The Internet of Things (IoT) attack surface includes all the IoT devices (smart appliances, sensors, actuators, etc.), applications, and communication channels used within an IoT ecosystem, which may contain weaknesses or vulnerabilities. |
8 Immediate Actions to Reduce the Cyber Attack Surface
1. Create an attack surface management plan
The first step towards reducing your cyber attack surface is developing an attack surface management plan. This plan should entail how to discover and inventory all the known and unknown assets that make up the attack surface of your environment.
You can’t monitor and mitigate risks without a comprehensive overview of all assets. Ideally, discovery efforts should include the use of automation to speed things up. Make sure to include in the plan efforts to monitor the attack surface for security weaknesses, prioritize, and mitigate.
2. Implement zero trust
Zero trust security principles can dramatically reduce your digital and social engineering attack surface. Zero trust eliminates the idea of putting inherent trust in a user or device trying to access a business resource. Continuous authentication and authorization based on the risk profile of access requests make unauthorized users far less likely to get inside your environment using social engineering or stolen/compromised credentials.
3. Remove complexity
A defining feature of large attack surfaces is their complexity. Comprehensive asset discovery efforts will often uncover dozens of assets that aren’t even in use, but they remain running and exploitable as potential paths into your network. To remove complexity and further shrink your attack surface, be ruthless in disconnecting or de-provisioning assets that nobody uses, such as:
- redundant legacy software
- cloud instances with no workloads
- user accounts for ex-employees or with no valid owners (orphaned accounts)
- subdomains no longer in use
4. Monitor vulnerabilities 24/7
Threat actors don’t stick to a 9-5 schedule when probing target networks and infrastructure for potential weaknesses. Using both technological solutions and people, it’s imperative to continuously monitor for weaknesses and vulnerabilities in your attack surface. Misconfigurations and other risky changes can happen anytime—mitigating them before they are discovered is crucial to keeping your attack surface manageable.
5. Create strong user access protocols
For many organizations, the journey towards zero trust isn’t exactly a short one. Still, it’s possible to shrink the attack surface by strengthening user identity and access protocols. At a minimum, ensure that any users get only the minimum permissions and resources needed to complete their daily work. Opt for a strong multifactor authentication (MFA) implementation that uses public key cryptography as one of the authentication options (e.g.,. FIDO2, WebAuthn).
6. Use strong encryption policies
Where sensitive data sources are stored or in transit in your IT environment, there is always a need to encrypt that information. Without encryption in place, you open up any number of paths for threat actors to try and access your prized information assets. Encryption makes the data unreadable, even if it’s intercepted or accessed.
7. Protect your backups
Many businesses back up their data assets for security, disaster recovery, or business continuity purposes. Frequently, these backups get stored in cloud storage buckets, but an all-too-common occurrence is for cloud storage buckets to be left unprotected. An incident in 2022 saw security services group Securitas expose over 1 million files in an S3 bucket left open and likely used as a backup source for employee data. Make sure you treat backups with caution and ensure they are at least password protected or, better still, have MFA configured.
8. Train your employees
Training employees in cyber best practices and making them aware of the telltale signs of social engineering attacks is a transformative way to reduce your attack surface. While most organizations have some cybersecurity training programs in place, the training materials are often ineffective and can sometimes annoy employees. Making training more engaging, adaptive, and tailored towards the language of different business units will likely empower them with longer-lasting security knowledge and contextual awareness of best practices.
Cyber Awareness Training Can Help You Manage Your Attack Surface
A common trend running through the greater security challenges of today’s expanding cyber attack surfaces is how human fallibility opens up security gaps across a broader set of points than ever. It might not be possible to reduce the risk of human error completely. Still, the truth is that the vast majority of mistakes stem from basic errors that an effective cyber awareness training program can mitigate.
CybeReady provides a complete security awareness solution that fully automates training while making it fun and engaging for employees. The platform requires minimum IT intervention so that your employees can quickly become cyber-aware and help collectively shrink your attack surface. Request a demo here.