As students and faculty alike take off for their summer vacations and enjoy a respite from rigorous academics, there’s another group who enjoys summer vacation perhaps even more: cybercriminals. What draws these hackers to launch attacks against higher education institutions, and what kinds of damage do these attacks inflict? Most importantly, what can be done to stop them?
Attack at Their Weakest: The Appeal of Vacation Breaks
Attackers are experienced in targeting victims when they are at their weakest. For higher educational institutions (HEIs), that’s during extended vacation breaks such as summer, because staff are focused on exams and getting ready to leave for vacation. Once they’re on vacation, it could take far longer than usual until they realize the institution has been attacked.
Unfortunately, it’s due to a few misperceptions these institutions have concerning cybersecurity.
First, HEIs falsely believe that if students and faculty are away for the summer, there is less activity to monitor. But security doesn’t go on vacation when data is in the cloud. Even during summer vacation, students may access their email or data to communicate with friends or complete assignments during a summer session.
Second, there’s a strong disconnect between IT and university leadership. For most university professors, presidents, and boards of trustees, cybersecurity isn’t on their radar. CIOs aren’t always part of university leadership; when they are, they may struggle to elevate cybersecurity issues to the executive agenda.
In many cases, it takes a serious security break to get HEIs to prioritize cybersecurity.
Easy Targets—Especially When School’s Out
It’s critical for university and IT leaders to bridge this gap because attacks on HEIs aren’t decreasing any time soon. According to CheckPoint’s latest research, global cyberattacks have increased in Q1 of this year by 7%, hitting education the hardest, with 2507 attacks per week (an increase of 15% compared to that same period in 2022).
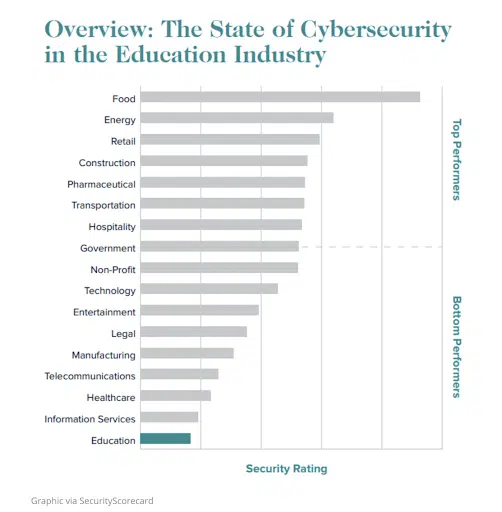
Why? This focus can be attributed to several factors, the primary one being the wealth of data HEIs have at their fingertips. Not only do online applications and enrollment forms offer students’ sensitive personal information and financial data, but HEIs have important data about their faculty, staff, and alums for decades after graduation. Medical research institutions may also have access to highly sensitive healthcare data.
Top universities also have larger attack surfaces. Hundreds of domains and subdomains represent entry points attackers can use to exploit an HEI’s system, network, or applications. Unmaintained sites, or domains that are not in use but continue to be connected to the internet, increase this risk even further.
The massive shift to online learning after COVID also entices attackers with new entry points that are easier to access due to reduced cybersecurity budgets. At the same time that 75% of students in the U.S. were enrolled in at least one online program during COVID, budgets for cybersecurity shrank. This fact is especially noteworthy since the most common result of HEI cyber attacks is a data breach—the most expensive attack to recover from, costing $4.6 million a year globally.
The cybersecurity measures generally employed by HEIs are, to put it lightly, lacking. Unlike the financial, software, and consumer-facing industries, universities have been notoriously slower to strengthen their cybersecurity posture. Their decentralized environments, with many different heads of departments, offices, and administrators, exacerbate this challenge further.
Significant Damage Means Longer Recovery Time
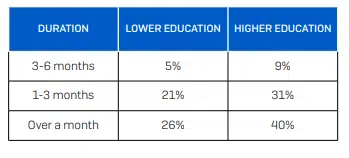
Not only are HEIs attacked more often, but higher education takes longer than any other sector to recover from these attacks, according to a recent report from Sophos, a global leader in cybersecurity. Over 40% of colleges and universities took over a month to recover from attacks, longer than both the national average of 20% and the recovery time from lower education (K-12).
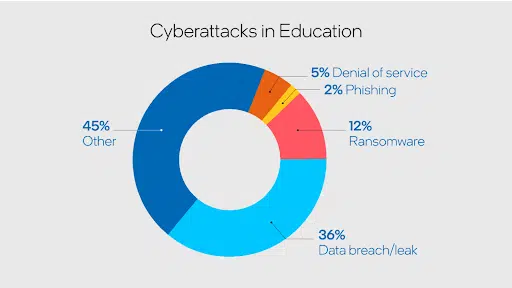
And HEIs suffer the whole gamut of cyber attacks. Phishing attacks have increased on average by 50% in 2022, with education as the most targeted industry. Phishing attacks aim to target victims with emails to gain access to PII. New technological tools such as ChatGPT and other AI make executing these attacks easier. According to Mike Ray, the International Disciplinary Center’s CIO, HEIs “aren’t making enough of an investment in terms of finance, personnel, and technologies to fight phishing attempts.”
Last year cybercriminals shifted from ransomware and phishing attacks to malware, a type of software that gains access to a university system and network. Ransomware takes malware a step further by locking access to files and demanding money to unlock them. In 2021, ransomware was the preferred method of attack for HEIs, targeting over 65% of universities. The vast majority of those surveyed by Sophos claimed that these types of attacks had affected its operations.
Distributed Denial of Service attacks (DDoS) on HEIs that flood a network or service from multiple computer systems with information so that they cannot be used rose by a staggering 102% in Q2 of 2021.
The Best Defense Is Prioritizing Cyber Defense
Still, the future offers hope. There are steps HEIs can take to improve their security posture and defend themselves against attacks during the summer vacation period.
Implementing strong passwords is one of the basics of practicing good cyber hygiene. Both students and staff should understand the danger of sharing passwords, change their passwords regularly and know how to create or generate strong passwords with a combination of symbols, letters, and numbers.
Using Multi-Factor Authentication (MFA) helps defend against cybercriminals seeking to gain entry to a network that only requires a username and password, allowing them further access into your network.
Ensuring that the HEI has reliable backups (and a backup plan) is critical in case of a data breach or natural disaster that destroys backups. Remember that attackers intentionally seek to destroy backups, so they should be separated from the network so they’re out of the hands of anyone with malicious intent.
Ongoing cybersecurity awareness education for staff and students is possibly the most critical element. If humans are the weakest link, it means they are also an organization’s greatest source of strength. Basic cyber hygiene must be discussed and practiced, along with preventing the most common human errors, such as using unsecured public WiFi or opening emails that could contain malware.
Knowledge Is Power in Cybersecurity
Ultimately, HEIs cannot afford to be reactive when it comes to cybersecurity. It is crucial to prioritize defense, get IT and university leadership on the same page, and ideally invest in robust measures that mitigate risks and ensure their digital well-being. But at the same time, small changes like MFA and backup plans compound to make a difference in the overall strength of the organization’s security posture.
With proper education and training, employees, IT security teams, and university leadership can work together to make the vacation period a more secure environment in higher education—and a less attractive target for cybercriminals.













