Humans are essentially social animals that foster positive emotional well-being through meaningful interpersonal connections. However, this helpful trait can be easily abused through scams perpetrated by social engineering. It’s a con game that’s been going on since the early days of humanity—but today, with social interactions transcending physical boundaries online, the menace of social engineering fraud is dramatically amplified.
Thanks to the Internet’s broad reach, social engineering attacks can go viral with minimal effort.
Though primarily targeted at individuals, these attacks can also harm their friends, workplace colleagues, and employers. IBM estimates that in 2023, data breaches initiated by social engineering averaged over $4.5 million in costs to organizations.
Fortunately, cybersecurity team members and IT managers can take actionable steps to prevent the risks of social engineering attacks from becoming catastrophic. Let’s remove the evil veil around social engineering and discover five strategies for tackling it in your organization.
What is social engineering, and why do you need to care in 2024?
Social engineering is a deliberate, malicious tactic to deceive people into performing specific actions that compromise their security. These tactics rely on manipulating a person’s social behavior through various techniques. Malefactors initiate social engineering attacks to exploit a person’s social standing, such as financial and personally identifiable information, or gain sensitive data related to their professional authority, like usernames, passwords, and workplace secrets.
Social engineers exploit different aspects of human psychology, such as emotions, cognitive biases, and motivations, to draw victims into their traps. They employ persuasive and coercive means to evoke a response from targeted individuals.
For centuries, ‘con artists’ have wielded the craft of social engineering to manipulate and deceive. However, it wasn’t until the dawn of computers and the Internet that this ancient art form gained significant notoriety, quickly becoming a linchpin of cybersecurity threats.
As we step into the AI-driven era of 2024, the stakes have risen dramatically. Thanks to AI’s sophisticated ability to replicate individuals based on widely recognized attributes like their face and voice, social engineering has become an even more formidable threat.
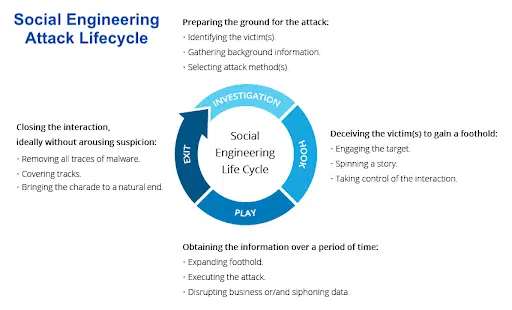
What are the types of social engineering attacks?
Social engineering attacks can be broadly classified based on the attacker’s chosen method to ensnare a victim. The top five most often encountered are:
Phishing
Phishing, the most common social engineering attack, involves attackers crafting and sending deceptive messages. By impersonating trustworthy entities like banks, they solicit sensitive information, such as credit card details. These fraudulent messages are disseminated through emails, SMS, or voice calls, leading to distinctions among phishing types: email phishing, smishing (SMS phishing), and vishing (voice phishing).
Pretexting
Pretexting attacks rely on elaborate stories crafted by attackers to deceive their victims. In these scenarios, the attacker assumes the identity of someone with authority or a credible reason to inquire, making their requests for sensitive information seem legitimate. This method is more intricate than phishing, demanding a detailed setup where the social engineer aims to convince the victim of their authenticity, thereby coercing them into divulging confidential details.
Whaling
A whaling attack is a very targeted form of phishing aimed at people with authority, such as CEOs or wealthy individuals. Whaling attacks always personally address targeted individuals, often using their title, position, and phone number, which are easily obtained through web scraping from websites, social media, or the press.
Baiting
Baiting attacks entice victims with the lure of irresistible offers (the ‘bait’). These schemes are framed around the promise of luxurious gifts or substantial financial returns, compelling the recipient to take action.
The persuasive messaging urges victims to undertake specific actions—like filling out an online form with personal details or clicking on a link—under the guise of claiming these offers. However, these steps are traps designed to harvest sensitive information to commit fraud or to distribute malicious software.
Quid Pro Quo
In this social engineering attack, a malefactor offers the victim something in exchange for information or access, such as fake technical support or insider information. For example, the attacker might call the victim and pretend to be from their IT department. The attacker might then offer to help the victim fix a computer problem, but to do so, they will need the victim’s username and password. Once the attacker has the desired information, they can perform malicious actions.
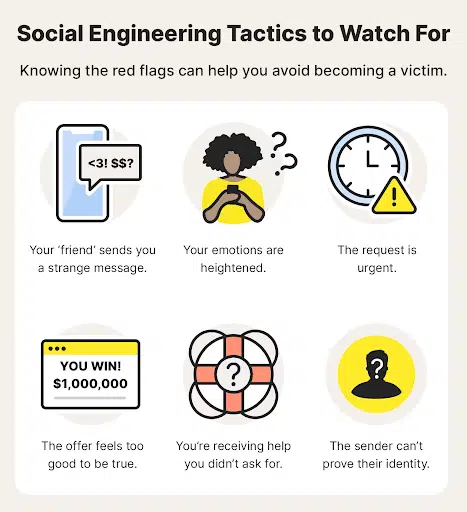
What are the warning signs of social engineering?
Social engineering is a widespread threat, but there are several warning signs to watch out for:
- Sense of Urgency – Social engineers often create a sense of urgency to pressure targets into acting quickly. Phishing emails might claim your account will be closed unless you verify your information immediately.
- Unrealistic Offers – Beware of emails or text messages that promise something too good to be true, like winning a lottery you never entered.
- Suspicious Communication – Social engineers might lack communication skills. Emails or text messages with typos, generic greetings, or impersonal language could be red flags.
- Spoofed Domains – Attackers may try to trick you by using website addresses that closely resemble legitimate ones, leading to fake websites. Be cautious of minor misspellings in URLs.
Five Essential Steps to Protect Yourself From Social Engineering
Here are five key steps to help your organization create a resilient framework against social engineering attacks:
1. Implement Clear Policies and Protocols
Develop comprehensive cybersecurity policies and protocols for dealing with social engineering tactics. These policies should cover:
- Protocols for detecting and responding to attacks
- Responsibility and accountability for employees, cybersecurity, and IT teams
- Determine the applicability of these policies within and outside the organization, such as for partners and vendors.
- Create a user-friendly system for employees to report suspicious activity. Train them to recognize red flags and empower them to submit incident reports with relevant evidence.
2. Conduct Cybersecurity Awareness Training
Institute a security awareness training program to help employees recognize and respond to social engineering attacks. Ensure your training program is regularly updated with real-world examples and best practices to keep employees vigilant.
CybeReady offers employee training designed to change employee behavior towards cyber attacks and increase employee resilience through effective, engaging social engineering simulations and education on the current threat landscape.
3. Strengthen Your Tech Defenses
Since social engineering attacks rely on common communication channels like email, SMS, and phone calls, your organization needs to build a series of security layers around these channels, such as:
- Use spam filters to filter emails and messages that seem like phishing attempts or contain spoofed URLs.
- Incorporate continuous security monitoring of network traffic, file activity, and endpoints for suspicious signs. This might include a sudden surge in outbound emails after a suspicious login, attempts to install malware or unauthorized access attempts.
- Deploy multi-factor authentication (MFA) to safeguard access to computers with sensitive data.
- Perform frequent updates on communication software to find and close any loopholes that social engineers might try to exploit.
4. Conduct Regular Simulated Social Engineering Attacks
Simulated social engineering attacks offer a way to assess employees’ awareness, susceptibility, and response to these tactics. Organizations should conduct these drills by inducing an element of surprise, which will help to expose areas for improvement and reinforce employee training. They should also be conducted as part of regular security awareness training.
5. Refine Response Procedures
Following a social engineering incident, analyze what happened and update your response protocols to address any weaknesses. This continuous improvement ensures your team learns from each event and adapts your organizational defenses.
Protect Your Organization from Social Engineering with CybeReady
Social engineering attacks are pervasive and can come at you from a variety of sinister angles. A successful attack can be devastating, with consequences that include data theft, lost customers, a tarnished reputation, and financial losses.
The best way to protect your business is with CybeReady’s innovative training platform. Going beyond basic security awareness programs, CybeReady’s unique blend of automation, data-driven campaigns, and personalized training equips your employees to handle real-world threats. It’s also easy for IT to deploy, minimizing strain on your resources.
Don’t wait for a social engineering attack to create an organizational crisis. Schedule a CybeReady demo to discover how creating employee readiness will safeguard your business.













