While technology and the Internet innovate and change, one thing remains constant—logging in. Of course, there’s more than one way to log in to an application or system, and no matter which authentication and authorization methods you use, a digital identity will be at the core of it.
‘Digital identity’ has become a broad and almost enigmatic concept. A digital identity can be anything that authenticates human and machine users to give them access to systems and data, including usernames, SSH keys, and passwords.
The existence of digital identities isn’t what puts them at risk—it’s management, usage, and governance failings that make identity a complex and critical attack vector. And wherever digital identities go, hackers follow.
The Current State of Identity Security
Identity security is a series of processes and protocols that enable organizations to secure digital assets, and the credentials and accounts used to access them. Without a comprehensive identity security strategy, hackers can gain unauthorized access by compromising a valid digital identity and moving laterally across your infrastructure.
The work-from-home and bring-your-own-device (BYOD) boom has further amplified the risks, leading to siloed identity and access management (IAM) infrastructures that fail to give cybersecurity teams the context, visibility, and protection necessary for digital identities. Another critical flaw is that organizations exclusively focus on protecting human identities even though machine identities now outnumber human identities by 45 to 1.
The worst part? No one is immune.
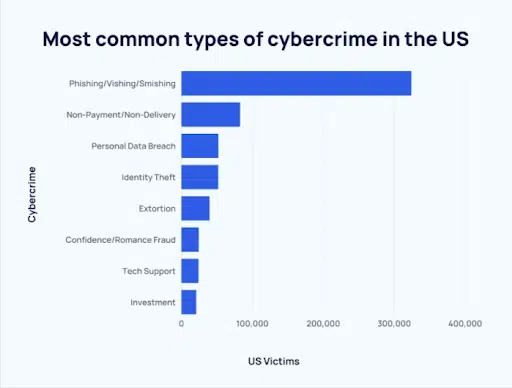
Casino and hotel giant MGM recently hit the headlines after facing a catastrophic data breach caused by none other than a good old-fashioned social engineering attack. A ransomware group successfully vished (phished via phone call) an employee after sourcing their information on LinkedIn, then used the acquired credentials to enter MGM’s system.
The result was a devastating breach of MGM customers’ names, Social Security numbers, and driver’s licenses—a sobering reminder of what a simple identity can do.
AI: The Identity Security secret weapon?
Ultimately, identity management is all about giving the right users (human and machine) the right level of access at the right time. 96% of organizations feel they could have prevented a breach if they had focused on the proper security measures, yet 65% have not implemented basic identity security measures like multi-factor authentication (MFA) and Single Sign On (SSO).
When your organization has hundreds or thousands of identities, the only way forward is automation. 52% of workforce identities have access to an organization’s most critical systems and sensitive data all the time due to a lack of visibility and control—a disaster waiting to happen.
Advanced IAM solutions use AI and machine learning (ML) to automate as many aspects of identity security as possible. AI and ML automatically provision and de-provision identities as and when users need them, and modern IAM solutions continuously monitor assets for suspicious activities, detect threats, and auto-remediate them. Automated identity security will skyrocket productivity if correctly executed because there will be no access management hold-ups or incident response downtime.
Why are identities in so much peril in the first place? Well, the Internet’s centralized control structure means that a relatively small number of companies house vast amounts of data. There’s no way to verify your identity without assistance from a third party, most likely a private company.
In contrast, a decentralized structure like the blockchain secures identities cryptographically so they cannot be deleted or tampered with. This feature makes data harder to breach, meaning you have total ownership over digital identities without needing third parties.
Where does the human factor come in?
Unfortunately, humans are the weakest link in even the most comprehensive and fortified cybersecurity strategies. Need proof?
90% of cybersecurity breaches are identity-related, and hackers often target employees via social engineering strategies to get their hands on identities. For example, the state of phishing attacks is already dire, with 3.4 billion malicious emails sent every day. While new technology like AI will advance identity security, it will also hinder it. 37% of organizations are concerned that generative AI will make phishing attacks more undetectable.
What about solutions, you might be asking while nervously changing your passwords?
Cyber awareness training, like phishing simulations, helps your employees understand the basics and complexities of identity security and supports them in implementing a broader IAM policy. Identity security best practices are only as effective as their implementation. Without buy-in and action from your employees, you can’t guarantee a culture of security.
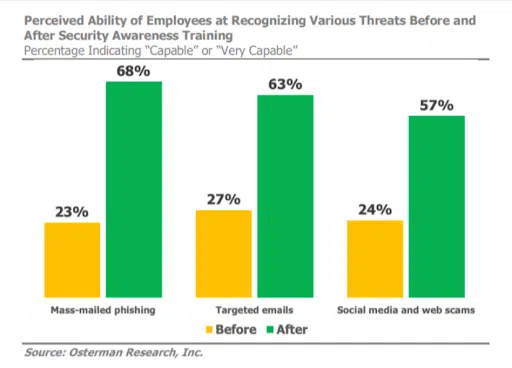
Your People Are Your Future
Employee cyber awareness training will further demonstrate its value as the world moves towards a more risk-averse state.
For example, cyber insurance companies are setting stricter guidelines in stone for companies to qualify for policies, and they’ve tightened policy terms and conditions to reduce losses from the enormous number of attacks. Who can blame them when an attack happens every 39 seconds on average?
Insurers are the ones holding the cards. Organizations can’t afford coverage, but they can’t afford not to have it. Some identity security protocols like MFA are mandatory, and qualifying for cover means demonstrating that your business takes a proactive approach to security.
Regulatory and compliance frameworks like the European Union’s General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA) have similarly stringent expectations, and institutions like the SEC require transparent risk management assessments that include participation from every employee.
Build a Culture of Identity Security
Employing the latest AI, ML, and IAM tools is only part of the solution. Cybersecurity awareness is an all-hands-on-deck job. Everyone in an organization must contribute to building a culture of identity security, which is critical for understanding it and meeting compliance and insurance regulations.
If you’re ready to help your business fortify its identity security strategy and protect against data breaches, contact CybeReady for easy-to-deploy, proven effective, and highly engaging employee cybersecurity awareness training.













