If there’s one thing that hackers love to exploit, it’s weaknesses and flaws in a web application. Fortunately, we have the Open Web Application Security Project (OWASP) to provide resources that help organizations and individuals identify and mitigate security risks in web applications and APIs.
Keeping APIs secure is critical because they are the backbone of modern-day applications. However, 74% of global organizations have reported at least 3 API-related data breaches within the last two years. This shows how urgent it is for InfoSec teams to stay abreast of the latest vulnerabilities to maintain API security.
OWASP recently released its annual list of the top ten API security risks. Let’s look closer to see what’s changed in API security in 2023.
Understanding API Security
An Application Programming Interface (API) enables seamless connectivity between modern applications. APIs are bridges for data flow across multiple systems. As the most widely used communication method among modern systems, APIs have become prime targets for attackers seeking to exploit weaknesses and compromise connected systems, especially in SaaS applications.
API security has gained increased attention in recent years as the focus shifts towards securing and managing associated risks. Previously, developers prioritized functionality over security, resulting in deployed APIs with significant security flaws, such as Broken Authentication, allowing attackers to bypass controls and access sensitive data.
With average data breach costs increasing daily, architects have no other option but to prioritize security in API design to mitigate risks effectively.
What changed in the OWASP Top 10 2023?
The OWASP Top 10 API Security Risks 2023 details changes to address the evolving API threat landscape. The update includes newly introduced risk areas and updates to existing ones, highlighting vulnerabilities for InfoSec teams to mitigate.
Newly Introduced Risk Areas
- API6 Unrestricted Access to Sensitive Business Flows
- API7 Server-Side Request Forgery (SSRF)
- API10 Unsafe Consumption of APIs
Updated Risk Areas
- API2 Broken Authentication
- API3 Broken Object Property Level Authorization
- API4 Unrestricted Resource Consumption

OWASP Top 10 2023: Newly Introduced Risk Areas Breakdown
1. API6 Unrestricted Access to Sensitive Business Flows
This risk describes APIs that unwittingly expose critical business flows, leaving them susceptible to potentially disastrous consequences. Businesses can incur tremendous losses and reputational damage if these vulnerabilities are exploited within a sensitive business flow.
For example, consider a case where a business exposes an API with the ability to purchase products. During a new product launch where these products are in high demand, attackers can use this API to programmatically call the API to acquire all the products from the website—and later sell the stock for a much higher value.
To defend against such attacks, simple yet effective mitigation controls must be in place without compromising the API’s business functionality:
- Device Fingerprinting: Restricting certain devices or client types, such as headless clients, can make automated attacks harder for attackers.
- Human Detection: Enabling captcha or advanced biometric solutions to identify genuine human interactions and stop using automated scripts.
- Non-human Patterns: Analyzing and detecting Non-human patterns within the business flow to ensure that programmatic access is restricted.
- Malicious IP Blocking: Tor Exit nodes and known VPN IP addresses can be blocked to minimize anonymous access.
- Use IP Whitelisting: IP whitelisting can be enabled if certain APIs are connected directly to businesses and/or consumed by specific developers.
2. API7 Server-Side Request Forgery (SSRF)
SSRF is a vulnerability that allows attackers to force the server to make requests that are not intended. The main issue in this attack is the lack of validation for URLs.
Here are some simple tips to avoid SSRF attacks:
- Validate and sanitize all client-based inputs.
- Never send RAW responses to the clients.
- Disable HTTP redirections.
- Use allow lists whenever possible for:
- URL schemes and ports
- Accepted media types for a specific functionality
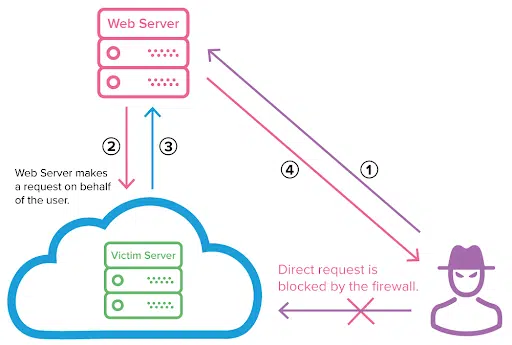
3. API10 Unsafe Consumption of APIs
This risk is similar to a supply-chain attack where the attacker compromises third parties to reach the intended targets. In this case, the attackers go after third-party APIs that other APIs directly consume for business purposes and data sharing.
Your APIs may be vulnerable to this risk if:
- The APIs interact with other third-party APIs over an unencrypted channel.
- The APIs blindly follow redirects.
- They do not implement timeouts with third-party APIs or services.
- They do not implement proper validation or sanitation of the data received from other APIs.
Preventing and mitigating these risks can be done by following good cyber hygiene guidelines such as:
- Assessing API security posture when evaluating third-party service providers.
- Ensuring that all API interactions happen over a secure channel such as HTTPS.
- Maintain a whitelist for well-known locations for redirections and deny any unexpected redirections.
- Always validate and sanitize all data received from third-party APIs.
OWASP Top 10 2023: Updated Risk Areas Breakdown
1. API2 Broken Authentication
There have been minor updates to API2 from 2019 to 2023, where this risk was renamed from “Broken User Authentication” to “Broken Authentication.” This reflects the shift in the risk not only to user authentications but also to other authentications such as API keys and OAuth tokens.
It is important to note that the prevention mechanisms mentioned by OWASP are still the same between these two versions since the basic principles apply to most authentication mechanisms.
Prevention mechanisms to mitigate this risk include:
- Do not reinvent the wheel; always use standards.
- Require re-authentication for sensitive operations.
- Implement multi-factor authentication.
- Implement account lockout mechanisms to prevent brute force.
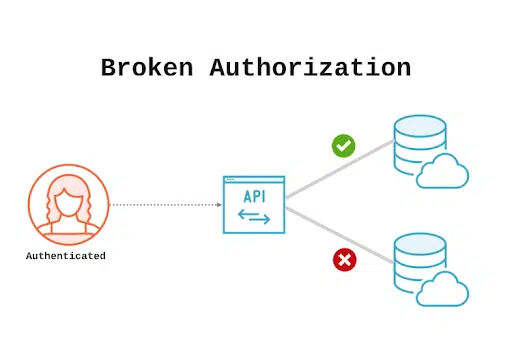
2. API3 Broken Object Property Level Authorization
This risk was previously known as “Excessive Data Exposure”. It has been renamed “Broken Object Property Level Authorization” to account for the broadened scope, including unauthorized modification or deletion of data via APIs. This change reflects the risk of exposing data and controlling access to the data at an object level.
Try these methods to prevent this risk:
- When designing your API, implement proper access controls, ensuring that users can only view and interact with the resources they are authorized to access.
- Avoid using generic methods such as to_json() and to_string(). Instead, pick specific object properties that you specifically want to return.
3. API4 Unrestricted Resource Consumption
This risk was previously known as “Lack of Resources and Rate Limiting” since it only focused on rate limiting. It is now called “Unrestricted Resource Consumption” since it includes other resource consumption issues, like excessive memory usage, CPU consumption, and network bandwidth.
To mitigate this risk:
- Use containers and serverless computing to handle and monitor key resources like CPU and memory smartly.
- Define and enforce a maximum size for all incoming parameters and payload data.
- Implement adequate rate limiting for APIs.

OWASP Top 10 2023: Implications for Organizations in 2023 and Beyond
Failing to keep up with new API security trends and methods can be a make-or-break situation for your organization. It’s not just about staying up-to-date; it’s about securing clients, avoiding data breaches that could cost millions, and preventing reputation damage that’s hard to recover from.
These changes in the OWASP API risks clearly show a shift in the security paradigm and how these risks evolve, what they mean to a business, and their impact. When adjusting how you develop and build things to match these new risks, think of it as changing the company culture.
It’s critical to ensure that everyone in the organization sees the importance of cybersecurity. Employee cybersecurity awareness platforms like Cybeready can make this shift smoother, helping you create a company culture where cybersecurity is a top priority. With your staff becoming a strong first line of defense, your organization will be more secure from cyber threats.
Embracing Your Organization’s Cybersecurity
As we move along in our journey through cyberspace, the world we used to know is rapidly changing, and so is the API threat landscape. OWASP’s annual Top Ten API Security Risk list is an invaluable tool for cybersecurity professionals to stay current and make the necessary changes to protect their organization’s web applications.
Equipping your organization with the necessary skills and information about cybersecurity and cyber threats goes a long way toward stopping data breaches, phishing attacks, and other cyber attacks. CybeReady’s programs offer engaging, customizable training that’s proven effective, creating a workforce ready to take on any new threats.
Contact CybeReady to book a demo and discover how our programs will bolster your organization’s cybersecurity.













