A menace lurks in the shadows of the digital world, growing more insidious by the day. This threat is phishing—a cleverly disguised trap that aims to hook individuals, reel them in, and compromise their sensitive information. These attacks exploit our curiosity, trust, and, at times, our momentary lapses in judgment.
The alarming truth is that phishing attacks are increasing in frequency, with an astonishing 70% surge in the last year—and they are also evolving into more sophisticated forms.
The need for heightened cybersecurity awareness and effective training has never been greater. No organization is immune to the threat of a phishing attack. It’s not a matter of if, but when—unless proactive measures are taken to fortify defenses.
A Phishing Story: No Longer a Tall Tale
Phishing has come a long way from the amateurish emails of the mid-90s, transcending the infamous foreign prince scams that once preyed on the unsuspecting. Today’s phishing scams are a sophisticated and ever-evolving menace in the cyber landscape, continually adapting to trick even the most vigilant individuals.
The essence of phishing lies in its ability to mimic legitimate communication. This method of social engineering targets unsuspecting victims by posing as trustworthy entities or even their own employers or team members. They aim to extract sensitive information such as login credentials, financial data, or personal identification details.
This threat has grown in step with the rise of social media networks, which provide bad actors with a wealth of data to craft highly personalized and convincing scams. The majority of phishing targets are now located through social media. With access to details like employment history, location, and even personal interests, phishers can tailor their messages with alarming precision.
The financial incentives for cybercriminals focusing on phishing are substantial. The profitability of these attacks lies in their potential to unlock access to financial accounts or harvest personal data that can be sold on the dark web. This economic factor is a powerful catalyst, driving scammers to refine and diversify their deceptive methodologies relentlessly.
As cybersecurity teams get better at defending and avoiding these attacks, scammers move in tandem to rework their techniques. “Cyber criminals constantly evolve their methods, so individuals need to be on alert,” says Emily Mossburg, global cyber leader at Deloitte. “Phishers prey on human error.”
Phishing’s New Frontiers
Regrettably, modern technology has made the task of scammers easier. The widespread use of digital communication tools, from emails to instant messaging apps, has expanded the reach and complexity of phishing attacks, including targeted methods like spear-phishing and whaling that focus on specific individuals or high-level executives.
Robots Gone Phishing: The AI Problem
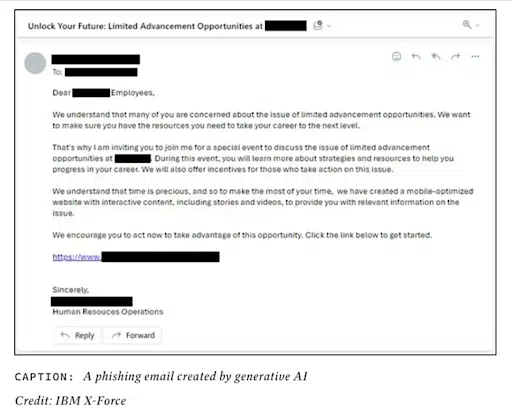
The emergence of generative AI technology allows scammers to automate the creation of phishing content, producing large volumes of persuasive fake emails or messages that can adapt to different contexts and targets. Generative AI’s proficiency in generating error-free, natural-sounding text is critical to writing authentic phishing communications that don’t tip off the target.
LLMs like ChatGPT can mimic writing styles, personalize messages based on gathered data, and even create convincing fake websites or digital content. “I have nearly a decade of social engineering experience, crafted hundreds of phishing emails, and I even found the AI-generated phishing emails to be fairly persuasive,” says Stephanie Carruthers, IBM’s chief people hacker.
Spoofed and Duped
Advanced phishing operations also employ website spoofing techniques to exploit users’ digital trust. This strategy dupes users into believing they are interfacing with an authentic, reputable site, typically through phishing emails that redirect them to these deceptive web pages.
Scammers execute their designs with high precision, carefully mirroring the website layout, graphics, and URL structures of well-known brands. The facade is so convincing that users are misled into submitting their sensitive information.
A Concerning Escalation
Integrating these advanced methods signifies a concerning escalation in the phishing landscape. Collectively, they represent a significant leap in the capability of cybercriminals to execute successful phishing attacks. As these techniques become more refined and widespread, equally advanced and proactive cybersecurity measures are required to combat them.
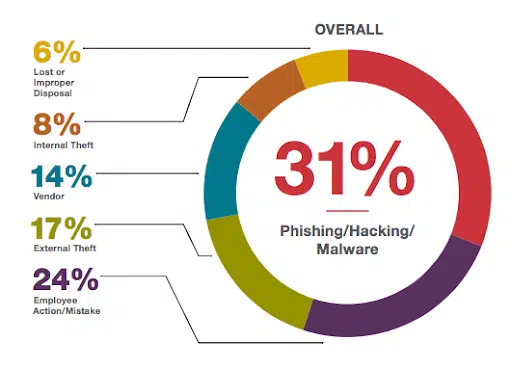
Recent data paints a concerning picture of the phishing threat. Each day, a staggering 135 million phishing emails flood the inboxes of unsuspecting individuals, while one large organization in Europe observed a troubling trend as attempted phishing attacks increased by 19% over just one year.
To Err is Human—and Expected
At its core, phishing is designed to manipulate human psychology and trust. This focus on the human element—our propensity for error and trust—makes phishing a particularly insidious and effective form of cyber attack. People underestimate their likelihood of being targeted, which leads to a false sense of security. Sophisticated scams exploit this complacency, using psychological tactics to manipulate and deceive.
The response to different phishing tactics differs by age group. Younger adults are more influenced by emails that create a sense of scarcity, while older adults are more swayed by emails that invoke a sense of reciprocity. However, the most convincing technique across all age groups involves authority, particularly in emails concerning legal matters.
The Silver Lining is Awareness
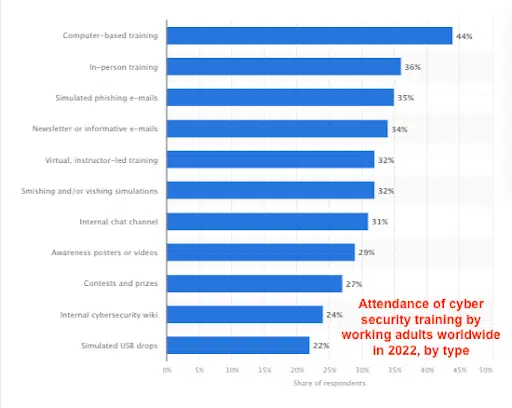
The silver lining in the fight against phishing is that the human element can be mitigated. Organizations can significantly diminish their risk through a well-orchestrated strategy centered on cybersecurity awareness and training. These programs empower employees with the best practices and skills to recognize and counter phishing attempts. Statistics show that organizations with robust cybersecurity training have 70% fewer successful phishing attempts.
Forward-thinking companies like CybeReady lead the charge by offering interactive, scenario-based training that mirrors real-life situations. This method proves far more effective than traditional, compliance-focused training, as it actively engages employees, making them participants rather than passive recipients of information.
The results speak for themselves. CybeReady’s corporate cybersecurity training platform has been proven to drive significant changes in employee behavior, resulting in an impressive 82% reduction in high-risk employee groups and bolstering employee resilience scores by fivefold.
The inseparable link between cybersecurity awareness and the prevention of phishing attacks is crystal clear. Empowering individuals with awareness, and equipping them with the skills to identify and combat these threats, will tip the scales in our favor as we continue to combat phishing.
Prepare for Tomorrow, Today
Looking ahead, the fight against phishing will only intensify. The advent of new technologies opens new avenues for deception. This evolving threat landscape warrants a proactive and adaptive approach to cybersecurity training that stays ahead of the curve and prepares individuals—not just for the threats of today, but for the unknown challenges of tomorrow.
Try a free demo of CybeReady today.













