The digital landscape has evolved rapidly, with the financial sector increasingly reliant on information and communication technology (ICT). However, this digital evolution brings with it significant vulnerabilities. Recognizing this, the European Union (EU) boldly introduced the Digital Operational Resilience Act (DORA) on November 28, 2022.
Targeted at fortifying the financial ecosystem against ICT disruptions, DORA becomes binding for financial entities and critical third-party service providers (CTPS) throughout the EU from January 17, 2024.
Why is DORA such a pressing need? In 2023, the global average data breach cost is $4.45 million, a 15% increase over three years. DORA mandates comprehensive measures like risk assessments, resilience testing, prompt incident response, and robust third-party risk management.
This post will navigate you through the intricate web of DORA, delineating its significance, applicability, and steps to ensure compliance. As the enforcement deadline looms, understanding DORA isn’t just a regulatory mandate; it’s a business imperative.
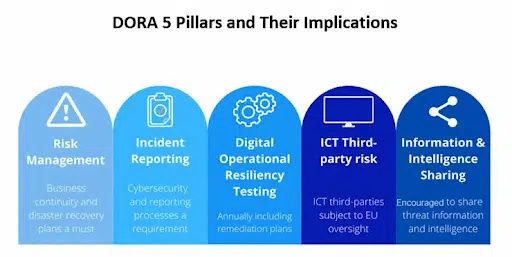
What are the 5 pillars of DORA?
In its quest to ensure cyber resilience, DORA stands firmly on its five foundational pillars. These are not mere compliance checkmarks, but critical imperatives to ensure a resilient financial sector in the face of ICT disruptions.
The five pillars of DORA are:
1. ICT Risk Management and Governance
It’s not just about managing ICT risks but embedding them into the governance structures. Institutions and CTPS are expected to set up a comprehensive framework that identifies and addresses risks; and ensures consistent oversight and effectiveness of these processes.
2. ICT-related Incident Reporting
Transparency is crucial when incidents occur. Both financial institutions and CTPS are obligated to report significant ICT-related disturbances promptly. This mandate ensures authorities are apprised of the incident’s details, its repercussions, and remedial actions undertaken.
3. Digital Operational Resilience Testing
Complacency can be an organization’s undoing. To combat this, periodic resilience testing is vital. Through these tests, vulnerabilities are unearthed, providing institutions and CTPS with a clear roadmap to bolster their ICT defenses.
4. ICT Third-party Risk Management
Financial entities can’t function in isolation; they lean heavily on third-party services. Recognizing the potential pitfalls, DORA emphasizes the necessity of thorough risk assessments with these entities and establishing clear contractual obligations, delineating responsibilities.
5. Information Sharing
Collaborative learning can be the silver lining in the aftermath of an incident. Institutions and CTPS are urged to share details about ICT mishaps amongst themselves and with relevant authorities, fostering a collective defense strategy and boosting sector-wide resilience.
In essence, these pillars are DORA’s blueprint for ensuring that the financial ecosystem, despite adversities, remains robust, agile, and unyielding to ICT threats.
How will DORA impact targeted organizations?
DORA isn’t just a piece of legislation; it is a catalyst for transformation in the digital operational resilience of the financial sector. But what does it truly mean for the various entities within its purview?
Financial Institutions
- Comprehensive Resilience Overhaul: From assessing risks to reporting incidents, from testing resilience to managing third-party risks, financial entities will have to take a more structured and proactive approach.
- Cultural Shift: A paradigm change from reactive troubleshooting to proactive risk management and resilience will be a hallmark.
- Greater Transparency: Institutions will be under the radar, necessitating transparent operations and clear documentation for regulatory compliance.
Critical Third-Party Service Providers (CTPS)
- Parallel Compliance Path: While CTPSs provide essential ICT-related services, their compliance path will be similar to financial institutions. This demands setting up infrastructure and processes to comply with DORA’s mandates.
- Enhanced Collaboration: Beyond mere service provision, CTPSs will enter a new era of collaborative reporting and information sharing, strengthening the symbiotic relationship with financial institutions.
Other Organizations
- Extended Responsibility: While not squarely fitting as financial institutions or CTPSs, some organizations, due to their ICT services’ nature, may come under DORA’s umbrella. This emphasizes the regulation’s reach, ensuring no weak link remains in the resilience chain.
7 Compliance Challenges DORA Creates
The Digital Operational Resilience Act’s introduction marks a turning point in the financial sector’s digital operational resilience. However, as with any significant regulatory shift, DORA presents compliance challenges for targeted organizations:
1. Expansive Scope
DORA’s application is not limited to just a handful of entities. Its encompassing range, covering diverse financial institutions and CTPSs, can make delineating its precise applicability a complex task. The breadth of ICT-related risks it addresses adds another layer to this challenge.
2. Intricate Requirements
Beyond its sheer breadth, DORA’s intricate mandates necessitate detailed understanding and strategic planning. The nuanced requirements and their profound implications make both comprehension and execution complex.
3. Financial Implications
Robust compliance is rarely cost-neutral. Beyond the conceptual challenges, there’s a palpable financial strain as institutions pivot towards bolstering ICT systems and restructuring processes to align with DORA.
4. Cultural Transition
Operational resilience isn’t just about systems; it’s about mindsets. Encouraging an organizational culture shift, from conventional operations to a resilience-focused approach, is a monumental challenge.
5. Resource Constraints
Not every institution or CTPS is resource-rich. For many, especially smaller entities, tangible challenges like budget limitations, skill deficits, or staffing shortages can impede full-scale DORA implementation.
6. Collaborative Hurdles
DORA’s mandates often necessitate a cooperative approach, especially with third parties. However, eliciting consistent cooperation, especially from entities outside DORA’s jurisdiction, can be arduous.
7. Ever-evolving Regulatory Landscape
The financial sector is no stranger to regulatory evolutions. Keeping pace with this dynamic landscape while ensuring continuous DORA compliance is a persistent challenge.
Despite these challenges, embracing the shift to DORA compliance will pave the way for a more resilient, secure, and dependable financial ecosystem in the EU.
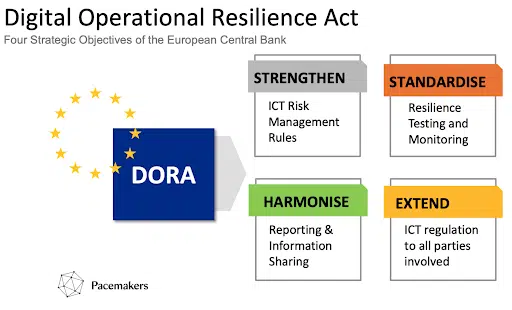
How should organizations prepare for DORA compliance?
Preparing for DORA compliance is no small feat. To effectively navigate this, organizations must:
- Dive into DORA’s mandates – Understanding DORA is foundational. Familiarize yourself with its key provisions by studying the legislation and official guidelines. Check out our in-depth article on preparing for DORA compliance for comprehensive insights.
- Evaluate your ICT risk – Ascertain your current position with ICT-related risks to discern areas needing heightened attention.
- Construct a concise compliance roadmap – Formulate a clear plan that seamlessly integrates DORA’s requirements into your operations.
- Embed and review – Execute your strategy and periodically assess alignment, making necessary tweaks.
- Engage in transparent communication – Promptly report ICT-related incidents and actively share information, bolstering the financial ecosystem’s collective resilience.
Lastly, for effective employee cybersecurity awareness training and to further your compliance endeavors, CybeReady’s solutions stand as an invaluable ally.
We’re providing a free DORA Compliance Checklist [XLS download] to streamline your journey!
How can CybeReady help organizations with DORA compliance?
Navigating the intricate realm of DORA compliance demands a well-informed strategy and efficient tools. As discussed, institutions face challenges that stretch from understanding the vast landscape of DORA to implementing a resilient ICT framework. Amidst these, CybeReady emerges as an indispensable companion for organizations.
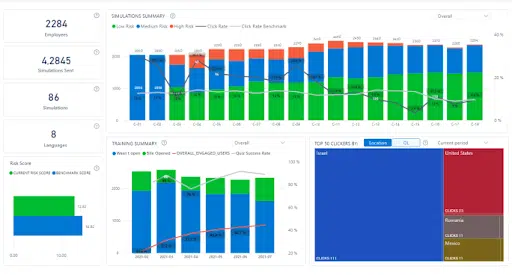
CybeReady’s security awareness training is adeptly designed to address core compliance concerns. The platform covers a broad spectrum of needs to help your staff learn capabilities in facilitating prompt incident responses, managing third-party risks, and enhancing overall employee security awareness.
Additionally, our compliance tool AuditReady helps your organization thoroughly prepare for cybersecurity audits and instantly generates compliance reports, so you are always ready to prove you’ve achieved DORA’s mandated training requirements.
A CybeReady-trained workforce equips institutions with the means to bolster their resilience against ICT-related incidents while ensuring alignment with DORA’s stringent guidelines. For a hands-on experience of how CybeReady can seamlessly integrate into your compliance journey, we encourage you to try a demo of our platform today.













