Do you have employees with access to sensitive systems they no longer need? Are there team members in your organization who, following a department change, find themselves locked out of essential tools critical for their new roles? For many businesses, the answer to these questions is yes. Maintaining precise control over who has access to what within a dynamic work environment is a widespread challenge for IT teams that causes organizational inefficiencies—but it’s also a security issue.
A recent cybersecurity study indicates that 80% of cyber attacks leverage identity-based techniques. When employees retain unnecessary access to sensitive systems or are inadvertently locked out of crucial tools, it creates vulnerabilities that attackers are all too ready to exploit.
A well-implemented User Access Review (UAR) strategy, combined with cybersecurity awareness training, offers a solution to these challenges.
What is a user access review, and why is it important?
User access review is a critical control mechanism within any organization that aligns access privileges to the precise needs dictated by users’ roles and responsibilities. UAR involves thoroughly evaluating permissions across all systems, applications, and data repositories to ensure everyone in your organization has the right keys to the right doors—nothing more, nothing less.
The significance of UAR extends beyond regulatory adherence, although it indeed plays a role in complying with various standards. At its core, user access review is a fundamental security practice instrumental in preempting unauthorized access and mitigating the risks of data breaches and insider threats.
The Benefits of User Access Review
There are several benefits provided by UAR that safeguard sensitive information and ensure efficient operations:
- It helps pinpoint and correct misaligned access permissions, significantly shrinking opportunities for attackers and enhancing your organization’s overall security posture.
- By limiting access to sensitive data to personnel requiring it for their work, UAR lessens the risks posed by intentional insider misconduct and unintentional data leaks.
- The detailed logs produced by regular UARs are invaluable for audit trails and forensic analysis in the event of a security incident.
- User access review provides a flexible framework to manage access rights during organizational changes like employee departures, role changes, and new hires.
When is a user access review required?
User access reviews are essential checkpoints for managing system and data access across various scenarios and for meeting compliance with multiple standards. Here’s when and why they become necessary:
- Regulatory Compliance Demands – UARs are required under regulations like GDPR, HIPAA, SOX, PCI DSS, and ISO 27001, which all demand stringent access controls to protect sensitive data.
- Changes in Employee Status – Life at work—and access—changes with promotions, transfers, or exits. When it does, UARs help realign and adjust access rights accordingly.
- Introduction of New Systems or Technologies – Rolling out new tech or updating the old? That’s your cue for a UAR. Conducting a detailed review helps assign appropriate access levels and prevents the carryover of obsolete permissions.
- Following a Security Incident – After a breach or security incident, a user access review can assess and remediate any weaknesses in access controls that may have been exploited.
- Periodic Security Assessments – Even in the absence of the above triggers, periodic UARs are a best practice for continuously improving your organization’s security posture.
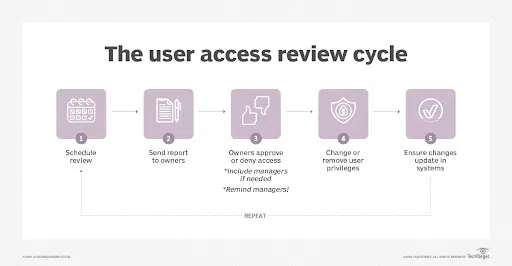
8 Steps for a Thorough User Access Review
1. Define the Scope
Start by identifying which applications and resources need to be included in the review. Highlight high-risk areas that require immediate attention. The goal is to outline precisely what will be audited to maintain focus and efficiency throughout the UAR process.
2. Revoke Unnecessary Access
Audit the access levels of former employees, service providers, and third-party vendors. Keep an updated log of all access privileges that have been terminated. It’s crucial for the security of your systems to fully revoke access from individuals no longer associated with the organization.
Consider using an automated de-provisioning process that revokes access rights the moment an employee’s contract ends or a vendor’s project concludes.
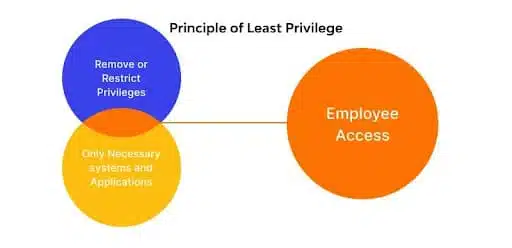
3. Enforce Segregated Duties (SOD) and Least Privilege
Apply the concept of Segregated Duties (SOD) by allocating specific tasks and responsibilities among various team members or departments to mitigate risks of fraud and errors. Employ the Principle of Least Privilege by granting users only the minimum access level needed to fulfill their job roles. Regularly reassess and modify these access levels to accurately match current job requirements.
4. Have a Zero-Trust Approach for Privileged Accounts
Begin the user access review process with a Zero Trust approach for privileged accounts. Conduct regular evaluations and monitoring of accounts with elevated privileges. Utilizing automation to manage these accounts promotes security and consistency. Implement expiration dates for privileged access and perform periodic assessments to verify the ongoing necessity of these accounts.
For example, this could mean scheduling quarterly reviews to reassess the access needs of project managers overseeing sensitive developments, ensuring their access rights expire with the project’s completion. This step ensures access rights are granted based on current needs, minimizing potential security risks.
5. Maintain Alignment with Security Policies
Keep an eye on any changes to user access rights and be ready to investigate any action that doesn’t align with your security policies. Employ advanced tools with secure and comprehensive monitoring capabilities to keep track of system logs and user activities.
6. Leverage Regularly Scheduled Reviews
Create a regular timetable for your User Access Reviews, selecting a frequency—quarterly, semi-annually, or annually—that aligns with your organization’s specific security and operational requirements. Committing to this timetable is important for ongoing security vigilance and reducing potential risks.
A financial institution handling sensitive customer data might opt for quarterly reviews to align with the fast-paced changes in regulatory requirements and threat landscapes. On the other hand, a smaller tech startup with a stable workforce might find semi-annual reviews sufficient to manage its access controls effectively.
7. Review User Permissions and Access
Take a close look at each user’s permissions and access levels. The aim is to ensure that what they can reach within your system matches what they actually need for their day-to-day responsibilities. Any excess or unnecessary access should be immediately adjusted or revoked.

8. Utilizing a User Access Review Checklist
A User Access Review Checklist is designed to guide you through the UAR process systematically—guaranteeing that no critical steps are missed and that all aspects of user access and permissions are reviewed. This checklist also doubles as documentation for audit purposes.
To use it, simply download the checklist and follow each item step-by-step, marking off tasks as they are completed.
Security Awareness Training and User Access Review
Security awareness training and user access reviews are critical components in fortifying your organization’s defense against cyber threats. While UAR verifies that individuals have access only to the resources necessary for their roles, security awareness training educates employees on using them safely and responsibly.
CybeReady’s fully automated cybersecurity awareness platform streamlines the employee training process, liberating IT teams from the heavy lifting typically associated with such programs. It revolutionizes cybersecurity training by directly delivering engaging content, including quizzes and security newsletters, to employees’ inboxes. Employing dynamic phishing simulations to adapt training based on employee responses, the platform creates a security culture that ensures constant vigilance.
Schedule a demo with CybeReady today and discover how educating your team with our tools can elevate your defense against cyber threats, keeping your operations secure and compliant.













