Imagine the sinking feeling when an unsuspecting employee, believing they’re opening a routine email, inadvertently clicks on a phishing link. Instantly, they’ve given malicious actors potential access to your company’s most confidential data. Such seemingly minor oversights can have monumental consequences to an organization’s finances, customers, and reputation.
With 43% of employees admitting they’ve made a mistake that compromised cybersecurity, what can be done? The answer is simple: a well-structured Security Awareness Training Policy can be the protective shield that ensures employees recognize these threats and are also equipped to respond effectively.
In this post, we’ll look closely at what makes up an effective security awareness training policy, providing actionable insights on crafting a strategy tailored to address current and emerging cyber threats. By the end, you’ll have a deeper understanding of how to build a policy that anchors your organization’s cybersecurity efforts and creates a culture that helps prevent cyber attacks.
Why You Need a Security Awareness Training Policy Now
A security awareness training policy is a comprehensive document that guides employees in identifying and reacting appropriately to cybersecurity threats. The primary objective of this policy is to cultivate an informed, responsive workforce that can adeptly navigate the potential risks prevalent in today’s digital environment. Through continual education on recognizing and averting security breaches, it seeks to minimize vulnerabilities by fostering a proactive culture of awareness and safety.
The necessity for such a policy is highlighted by the increasing sophistication of cyber threats that target unsuspecting employees. The recent MGM Grand cyberattack, which shut down MGM Resorts International properties throughout the US, was accomplished with a social engineering scheme. An unsuspecting employee was found on LinkedIn and compromised by the Scattered Spider ransomware group in a ten-minute phone call to the Help Desk.
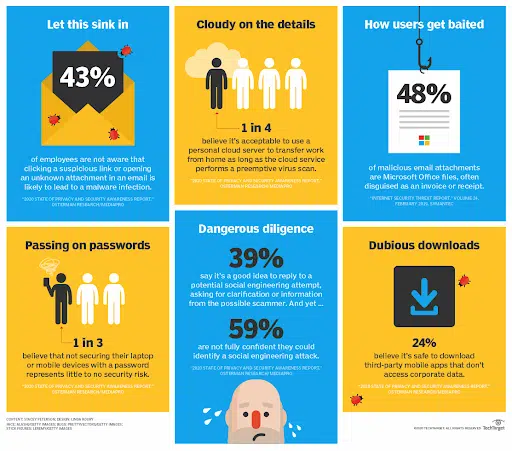
This attack proves that companies can significantly reduce the risk of financial and data losses, and foster a more secure operational environment, by arming individuals with the knowledge to detect and prevent cyberattacks. Implementing a security awareness training policy goes beyond just education; it empowers employees to defend against cyber threats, safeguarding organizational assets and reputation.
The 6 Essential Sections of a Security Awareness Training Policy
To create a strong and effective security awareness training policy, it’s vital to have a clear plan that covers all necessary areas. Here are six essential sections every policy needs to meet today’s cybersecurity demands, and actionable tips to do it right:
1. Policy Statement
A policy statement is the cornerstone of your security awareness training policy, encapsulating the objectives, scope, and directives clearly and concisely. This statement forms the backbone, offering a guideline for employees to adhere to and understand the organizational stance on cybersecurity.
Crafting a detailed yet concise policy statement is paramount. It delineates the organizational stance on cybersecurity and sets the tone for the ensuing policies, laying a foundation for a secure work environment.
Tips to Develop a Policy Statement:
- Clearly outline the objectives and scope of the policy.
- Incorporate the organizational values and principles relating to cybersecurity.
- Ensure clarity to enhance understanding and adherence among all employees.
2. Roles and Responsibilities
Identifying the pivotal stakeholders and explicitly defining their roles and responsibilities within the policy is a critical step. This helps in creating accountability and a coordinated approach to handling cybersecurity threats.
Tips to Define Roles and Responsibilities:
- Start by pinpointing the various departments and individuals who will play a significant role in the policy’s implementation and maintenance.
- Delineate clear roles and responsibilities to each identified stakeholder, creating a coordinated defense against potential cyber threats.
- Consider illustrating this with practical case studies to enhance understanding and application.
3. Training and Awareness Programs
Developing an array of training programs that align with industry standards and specific offerings from security awareness training platforms like CyberReady is vital in nurturing a cyber-savvy workforce.

Tips for Training and Awareness Programs:
- Begin by conducting a thorough analysis to identify the training needs pertinent to your organization.
- Develop training programs that encompass various aspects of cybersecurity, including but not limited to:
- Phishing Simulation Training – Engage employees with simulated phishing scenarios to hone their skills in identifying and avoiding phishing attempts.
- Secure Coding Training – For organizations involved in software development, training employees in secure coding practices is a must.
- Data Protection and Privacy Courses – Equip your team with the knowledge to safeguard sensitive information effectively.
- Employee Online Safety – Create a culture where employees adhere to safe online practices even outside the workspace.
- Incident Response – Teach employees how to respond to a cyberattack following the organizational plan.
- Regular Updates on the Latest Threats and Security Protocols – Stay abreast with the evolving threat landscape by continually updating your training modules.
- Continual Education and Updates – Reinforce the need for continuous security education to adapt to the ever-changing cyber threat landscape, potentially illustrating the effectiveness with case studies or testimonials.
4. Incident Response Plan
In the event of a security breach, having a robust incident response plan is imperative. This plan should outline proactive and reactive steps to mitigate the damage and prevent future occurrences.
Tips to Create a Response Plan:
- Detail a structured approach that outlines the necessary steps to be taken immediately following a security breach.
- Develop training sessions that equip employees with the skills to follow the response plan effectively, thereby minimizing potential damages.
5. Compliance and Legal Considerations
Compliance with industry standards and regulations is not just a best practice but a legal necessity. Understanding the legal ramifications of non-compliance can steer organizations clear of potential pitfalls. Ensure that this section contains the key regulations that apply to your industry.
Tips on Compliance and Legal:
- Detail the need for complying with industry standards, illustrating the importance through real-life case studies or examples.
- Highlight the potential legal consequences due to non-compliance, substantiating the discussion with real-life examples.
- To enhance your organization’s compliance efforts, consider incorporating a tool like CyberReady’s AuditReady to streamline compliance management and safeguard against potential legal complications.
6. Monitoring and Review
Maintaining your security awareness policy’s efficacy over time requires regular monitoring and reviews and setting up processes that allow periodic reviews and updates to stay relevant and effective.
Tips on Monitoring and Review Processes
- Implement mechanisms and metrics to continually monitor the effectiveness of the policy, making necessary adjustments based on the observations.
- Establish a routine of periodic reviews and updates to ensure the policy stays current with the evolving cybersecurity landscape.
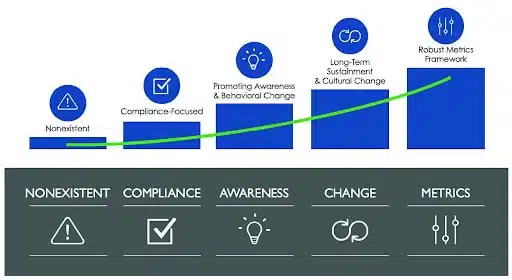
How to Implement a Successful Security Awareness Training Policy
Steps to Take
Starting the process of setting up a solid Security Awareness Training Policy requires both planning and insight. First, focus closely on your organization’s specific needs and weak spots. Create clear, actionable goals and integrate them smoothly with current rules to create a strong defense against cyber threats.
Promote open communication channels that share essential information and ensure a culture of respect and teamwork. Most importantly, cultivate a mindset of ongoing improvement where the policy changes and develops alongside the fast-paced world of cybersecurity, ensuring lasting success.
Potential Challenges and Solutions
Moving through the implementation phase might bring up a few obstacles, from resistance to change to gaps in technical knowledge and syncing with current systems. Turn this resistance into teamwork by encouraging a culture that welcomes feedback and ideas from everyone in the organization.
Tackle gaps in understanding with training programs that suit all skill levels, creating a learning environment that evolves together. Keep in line with existing processes by maintaining a routine of regular checks and needed adjustments, creating a unified and flexible approach to cybersecurity.
With these tips in mind, companies can smoothly navigate the complexities of policy implementation, building a solid defense against the ever-changing challenges of the digital age.
Enhance Your Security Awareness Training Policy with CybeReady
A robust security awareness training policy is mandatory in today’s business environment. By thoughtfully crafting a policy with these vital sections, organizations can build a strong perimeter against cyber threats, creating a safe and cyber-resilient operational environment.
Putting this theory into practice is made easy with CybeReady’s employee cyber awareness training. Designed to meet the changing needs of today’s businesses, our programs serve as a backbone, supporting your organizational goals and securing your digital boundaries. With the latest industry knowledge and expertise, it’s a central element in your security awareness training policy.
Contact CybeReady for a demo and start building a secure, empowered, and alert organization that’s prepared to face future cyber challenges.













