Despite years of security awareness training, close to half of businesses say their employees wouldn’t know what to do if they received a phishing email. According to a US government-backed study, one of the main reasons for the lack of impact of cyber security training is “waning engagement and growing indifference.”
Why are traditional security awareness training programs not efficient, and what can organizations do to change the tide?
Phishing Simulations Can Leave a Bad Taste for Employees
Crafting effective phishing awareness training takes sensitivity so that employees don’t feel tricked or put under the spotlight, and to ensure the content itself doesn’t cause offense. A recent example of phishing gone wrong happened at UC Santa Cruz, where Information Security personnel sent a phishing simulation that claimed a case of the deadly Ebola virus had been found on campus. Stakeholders at the university called the simulation “irresponsible and in poor taste.”
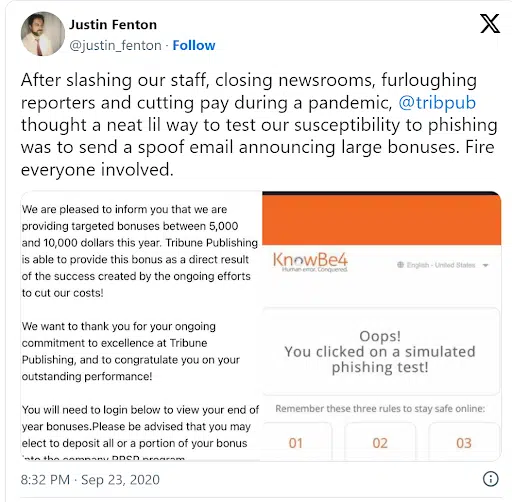
Security teams also need to consider the context when they send phishing simulations, as Tribune Publishing Co. found when an employee made their phishing faux pas public. An email was sent to employees that pretended to offer bonuses of between $5,000 and $10,000 as a result of cost-cutting initiatives. A risky training exercise at any time, but far worse as this had been sent amid the challenges of the coronavirus pandemic, furloughs, and many company layoffs.
Creating a Positive Buzz Around Security Awareness Training
While these examples show that the content itself needs to be created with care, it’s not just content to consider. Many security awareness training programs today are putting an oversized focus on content, and expecting an increase in content to equate to an increase in engagement.
The mistake is clear: security leaders see that the number of phishing attacks is rising, so they respond by implementing more training, more classes, and more content. This is like seeing that a project has exceeded its budget, and just channeling more money towards the team rather than understanding why the original funding wasn’t enough. The money isn’t the answer, and it usually won’t fix the problem. Similarly, it doesn’t matter how much content you put in front of employees — what matters is whether they are engaged and paying attention.
And at the moment, the studies show that they are not. Close to one-fifth (19.8%) of employees fall for phishing scams, even if they have gone through comprehensive training.
To combat the engagement gap, organizations need to turn away from adding more and more content and think about how and where that content is delivered. To maximize engagement and learning, security awareness training must be:
1. In the flow of work
One of the reasons that employees are not engaged with security awareness training is that it is seen as a hindrance to completing the growing number of tasks on their to-do lists. In traditional training environments, employees who are seen to be high-risk are often sent to security awareness training and need to register for and complete a course that takes time out of their working day. Most employees don’t pay attention to the course, and simply let it run in the background while they complete other more time-sensitive tasks.
Instead, security awareness training should happen at the time when they are most likely to engage and learn — which is the moment of need. As soon as an employee clicks on a link, the training should be triggered, helping them to immediately recognize their mistake and implement behavioral change. After all, if the correction is not made at the moment, then the impact is lost.
2. Respectful of their time
The next problem is that security awareness courses are usually far too long. Security teams need to recognize that security is not a core part of everyone else’s job, and so to ensure buy-in, training needs to be as precise as possible while being as short as possible, too.
At CybeReady, we recommend nuggets of micro-learning content, between 30 and 45 seconds on average, delivered in the moment of need, and as part of the regular flow of work. Employees spend up to five hours each day in their email inboxes — so this is where the learning should be delivered, immediately after a simulation has slipped past their defenses. Using a data-driven approach, personalization and adaptive learning experiences can make the training more effective for different risk groups, so that employees feel you are using their time wisely with training that is truly making a difference.
3. Taught with positivity
As well as being wary about the content itself, (Note to self — no false promises of bonus payments, or scaring your user base with fake outbreaks of deadly diseases!) think about the culture that you’re creating around the idea of security awareness training. Do employees feel that they are trying to be “caught” or “singled out” as rule breakers? This is likely to add to the negativity around security awareness rather than foster engagement. Language is key here – implement phishing simulations and learning opportunities rather than phishing “tests”.
When tests become training, and when it is delivered in the moment (and therefore is more effective), and when simulations are continuous throughout the year to create a variety of opportunities depending on the risk landscape, employees will get used to security awareness reminders as part of their regular workflow. Even when they make a mistake, without being sent to lengthy courses which steal hours from their day as a “punishment”, employees can feel positive about the learning experience.
Interested in shifting from a content-based strategy to one that focuses on delivery and engagement? Speak to an expert about our autonomous cyber security learning platform.













