Since the Morris worm propagated on the Internet in 1988 and exploited weaknesses in email and network services, vulnerabilities have posed problems for security teams. Often inundated with thousands of vulnerabilities in their complex technology stacks, security staff and CISOs struggle to prioritize and remediate these weaknesses. A recent analysis found an average of 31,000 security vulnerabilities present in each organization.
Of course, it’s not practical to fix everything, but companies often take that approach. An effective vulnerability management program brings order to managing vulnerabilities in a digitally transformed world. This article provides eight actionable tips for mastering your vulnerability management program.
What is a vulnerability management program, and why is it important?
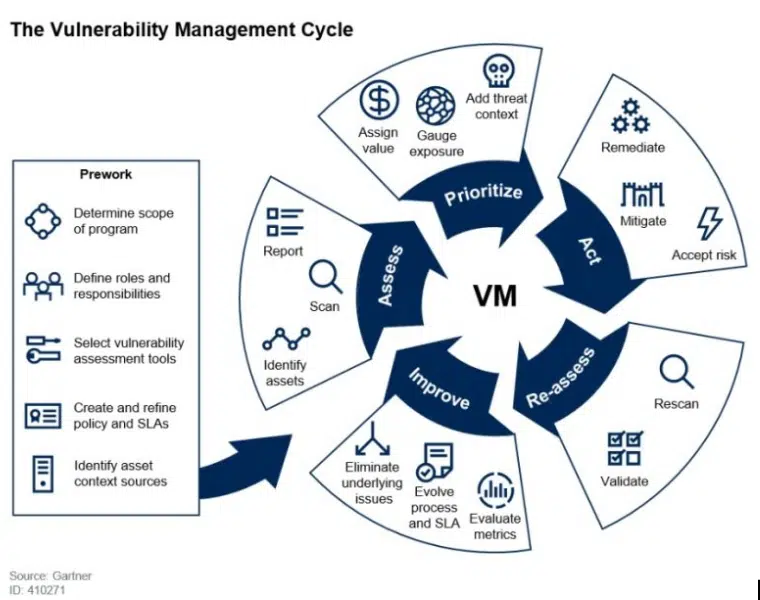
A vulnerability management program puts a strategic framework in place to continually assess for vulnerabilities, evaluate them, and act upon them to reduce cyber risk within an organization. Aside from vulnerability scans and tools, the program should focus on integration and alignment between various systems, processes, regulatory compliance requirements, and stakeholders to reflect that vulnerability management must be an enterprise-wide priority.
Hackers are adept at finding and exploiting vulnerable systems. Putting a program in place strengthens your cybersecurity posture and brings structure to what is commonly a scattergun process that leaves high-risk vulnerabilities unpatched for too long.
Threat vs. vulnerability
The relationship between threats, vulnerabilities, and risk is important to understand. A threat is a malicious process or event that can impact a business resource. A vulnerability is a weakness in hardware, software, or settings, that exposes an asset to a threat. Cybersecurity risk, therefore, lies at the intersection between threats, vulnerabilities, and your assets.
The attraction of vulnerabilities from a risk management standpoint is that you can both identify and correct them. Most organizations accomplish this risk reduction with a dedicated vulnerability management program.
Vulnerability management vs. patch management
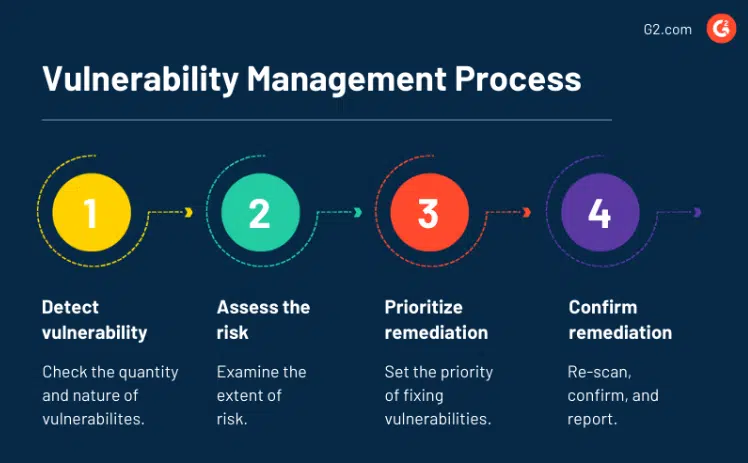
Vulnerability management refers to the entire process of detecting, prioritizing, acting, and reporting on vulnerabilities. Patch management takes center stage in the “acting” phase of vulnerability management when you apply updates to software and systems that fix security vulnerabilities.
What teams should be involved in the program development?
Vulnerability management programs should emphasize collaboration between those responsible for security and those working on technical tasks like software development. This collaboration helps integrate remediation as part of routine technical work.
Other business users should also have input to the program, for example, by highlighting the impact on their work or on the company’s operations when certain apps or systems are taken offline to fix.
8 Tips to master your vulnerability management program
1. Discover and map out your assets
Complexity defines today’s attack surfaces. Applications are no longer monolithic codebases developed in-house—modern apps rely heavily on third-party components, often from potentially vulnerable open-source projects. Sensitive data exposure can occur from internet-facing assets not having adequate security measures, such as encryption or access control. Managing vulnerabilities is much more challenging when you don’t have a full asset inventory that maps out your assets. Look for solutions to help automate the discovery of devices, ports, and applications. Comprehensive discovery should root out any shadow IT assets that haven’t been sanctioned by your IT team but are in use at your organization.
2. Define asset criticality rankings (ACR)
If vulnerability management is ultimately an exercise in reducing cyber risks, it makes sense to take a risk-based approach. Inundating security teams with mountains of vulnerability data doesn’t indicate what they should fix first. A risk-based approach uses asset criticality, vulnerability severity, and other factors to guide remediation efforts.
Asset criticality rankings (ACR) assign a score to assets based on their importance to your company. This ACR score uses criteria such as business impact, connectivity, functions, and asset location to determine the criticality of an asset. In any risk-based approach, potential vulnerabilities in more critical assets should be dealt with first.
3. Undertake scans regularly
Introducing a vulnerability into your IT ecosystem takes just a few clicks. Consider the widespread use of containers; small packages of reusable code that contain everything needed to run a specific microservice or software process across any environment. One study found that 75% of containers have “high” or “critical” patchable vulnerabilities, and all it takes is a few keystrokes from a developer to introduce one to your environment.
Regular scanning versus ad hoc scanning improves your vulnerability management program. Timely, accurate, and relevant data arms you with the information needed to deal with weaknesses. Industry best practices often recommend at least quarterly scans. However, if there are frequent changes to code or infrastructure, you’ll probably need to scan for vulnerabilities more often.
4. Train your staff with a cybersecurity awareness program
Don’t downplay the impact of strong cybersecurity awareness in improving your vulnerability management program. After all, staff with poor cybersecurity knowledge are more likely to introduce vulnerabilities into your environment through misconfigurations or by adding risky open-source libraries and frameworks to applications.
Some cornerstones of effective cybersecurity training include continuous training, content that adapts to different roles, and training all of your workforce. Try to move on from seeing cybersecurity training as a box to tick—its role is far more critical than that.
5. Make plans for unpatchable vulnerabilities
Taking action on vulnerabilities is not necessarily all about patching. There will be times when you’ll detect vulnerabilities for which there is no option to patch. These cases often arise in legacy software systems that the original vendor no longer supports. Sometimes it’s just not feasible to patch a vulnerability due to zero downtime tolerability in the affected system (e.g., industrial control systems).
Mastering your vulnerability management program should include a plan for handling unpatchable vulnerabilities. Another option is to segment assets with unpatchable vulnerabilities away from the rest of the network so that you can better control the traffic that accesses those assets.
6. Define, measure, and review program metrics
It’s hard to strengthen vulnerability management without defining, measuring, and reviewing useful parameters indicating what’s working and where to improve.
Some useful candidates include:
- Device coverage
- Mean time to detection
- Frequency of scans
- Mean time to remediation
- Percentage of vulnerabilities closed
Collecting and reviewing this data gives you better insight into areas of vulnerability management that you should tweak. If you are one of the many businesses that take 250 days to remediate high-risk vulnerabilities, aim to get that down to around 30 days.
7. Incorporate automation
Vulnerability management is essential, but it’s also full of tedious and repetitive tasks. Furthermore, those tasked with patching get inundated with data about vulnerabilities that won’t realistically get exploited. The result is vulnerability fatigue, where IT teams become overburdened with information that they struggle to act on.
Incorporating automation into vulnerability management can help overcome these difficulties and free up staff to focus on actionable, risk-based information. Automating vulnerability prioritization, remediation workflows, and even patch management are all options worth considering.
8. Develop and implement a mitigation plan for critical and high alerts
A dedicated mitigation plan can help you respond faster to critical and high-risk vulnerability alerts. Automating workflows ensures that you streamline the handover of mitigation and waste less time. But you also need to have a plan for what actions to take.
If a security patch is available, apply it as soon as feasible. Since accepting these severe risks is not an option, a lack of any available patches should be accounted for with other mitigation measures. Lastly, verifying that mitigation has worked, whether through a re-scan or some other form of validation, is important.
Stay on top of vulnerabilities with cybersecurity awareness training
While these best practices are sure to improve your vulnerability management program, cybersecurity education also provides a useful foundation for combating threats and avoiding vulnerabilities. But with so many tasks competing for IT and security teams’ attention, cybersecurity training is often seen as a burden rather than an asset. The result is sub-optimal training intervals and content that bores rather than engages.
CybeReady transforms cybersecurity training with a fully automated security awareness program. The platform uses an interactive security newsletter which gets delivered automatically at optimal intervals to reinforce learning and promote a security-first culture.