These days, installer files are rapidly going the way of floppy disks and dial-up modems. Organizations increasingly rely on cloud-based SaaS solutions for their critical business functions, won over by their scalability, ease of implementation, and lower costs. SaaS offloads many maintenance tasks from the user to the provider, but organizations still have to take charge of their own SaaS cybersecurity.
SaaS shifts the potential attack surface from the organization’s network and servers to the various third-party providers who have been granted privileged access to the organization’s data. Unfortunately, cybercriminals have wasted no time making the pivot—at least 55% of organizations have dealt with a SaaS-related security incident over the past two years.
SaaS security comes with unique challenges. To take advantage of SaaS solutions safely and protect your organization from cyberattacks, it’s essential to understand the basic principles of SaaS security and follow a comprehensive, step-by-step plan to put sufficient defenses in place.
What is SaaS security, exactly?
SaaS security refers to the practices an organization uses to protect the data and accounts that can be accessed through cloud-based third-party providers. Responsibility for SaaS security is shared between the provider and the client organization.
By design, SaaS solutions are accessible remotely from various locations and devices. This allows for great flexibility and agility, but it also presents a broad attack surface for cybercriminals.
For a big-picture view of what SaaS security encompasses for both the provider and the client, we can break it down into a six-layer model:
Cloud
If high-level cloud credentials are compromised, attackers have the keys to the kingdom. Multi-factor authentication is essential for robust cloud Identity Access Management.
Network
SaaS providers can prevent unauthorized access by restricting traffic from untrustworthy sources and secure the network’s data by using encryption.
Server
Providers can also strengthen security by patching server software, closing ports, and shutting off unnecessary services.
User Access
User credentials are one of the most significant points of vulnerability. Users will choose simple passwords over strong ones, fall victim to phishing attacks, and abandon improperly secured accounts when they leave the organization. Identifying and securing vulnerable accounts is critical.
Application
The SaaS application should be frequently tested, patched, and updated to close up potential exploits and vulnerabilities.
Data
Encryption can protect the data even if higher-level security layers are compromised.
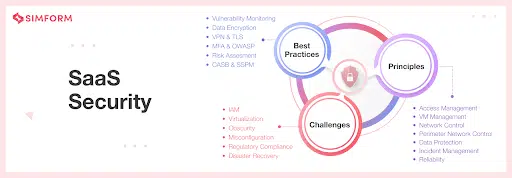
What are the 7 principles of SaaS security?
The best way to come up with a SaaS security strategy that covers all bases is to follow the seven fundamental principles, which can inform best practices across every layer:
| SaaS Security Principle # | Name | Description |
| 1 | Access Management | User permissions should be based on the requirements of their role within the organization. |
| 2 | Virtual Machine Management | Virtual Machines should be patched and updated frequently. |
| 3 | Network Control | Traffic should be filtered at a high level of granularity. If possible, set up a firewall using virtual private networks. |
| 4 | Perimeter Network Control | Firewall rules should be based on up-to-date threat assessments. Intrusion detection and prevention software should be utilized. |
| 5 | Data Protection | Sensitive data should be encrypted and regularly audited. |
| 6 | Incident Management | Employ a system for capturing, tracking, and monitoring security incidents. Set up alerts to notify your IT team of potential attacks in progress. |
| 7 | Reliability | Your provider should have a robust content delivery network that minimizes downtime, and a disaster recovery plan that ensures quick turnaround when outages occur. |
What are the benefits of SaaS security?
SaaS solutions allow anyone within your organization to access the data and services they need, wherever they are. This has the side effect of putting your critical systems within reach of attackers, so SaaS security is essential for preventing breaches, protecting your data, and reducing the likelihood of costly incidents and downtime.
A data breach can be devastating for an organization, causing harm to its reputation, driving customers away, and incurring costly legal penalties. A well-constructed SaaS Security plan will help strengthen trust in your organization and keep you compliant with regulatory obligations.
What are the challenges of SaaS security?
The average company uses up to 130 different SaaS solutions, which means that a substantial challenge is the sheer size of the attack surface. Each of these will have its own level of privileged data access, a third-party provider responsible for server-side security, and any number of user accounts that may or may not be secure—or set up with appropriate access levels.
SaaS solutions frequently offer third-party integrations, opening up yet more potential vulnerabilities that may be affected by factors outside your immediate control. The fact that multiple parties share the responsibility for SaaS security can lead to oversights that create gaps in your defenses.
Regulatory compliance can also be challenging when working with multiple SaaS vendors located in regions with different laws and industry standards.
7 Steps to Get Started with SaaS Security
1. Create a Security Map
Step one is getting a clear overview of which apps you’re using, which teams are using them, what data they have access to, and what your security requirements are for each. Your map should include each SaaS app’s function, vendor location, third-party integrations, and any relevant access controls or security features.
2. Clarify Your Responsibilities
Identify the stakeholders and users for each app and specify which security elements they’re responsible for to prevent security gaps from arising due to a lack of clarity or accountability. Security is a joint effort between the vendor, your organization (and various IT or cybersecurity units within it), and the individual users.
3. Adopt a Zero Trust Security Model
Many organizations are shifting to a Zero Trust security model that limits access based on user roles and tasks. Data rights are not based on implicit trust, but on strictly defined needs. Users are required to always authenticate themselves before taking any action. A successfully implemented Zero Trust model will minimize the risk that a single compromised user account can grant an attacker access to all your data.
4. Monitor Constantly and Engage in Frequent Security Assessments
Constant monitoring of your entire inventory of SaaS applications can be challenging, but it’s one of the most effective ways to detect threats in the early stages—before it’s too late to prevent them. Check-in with your vendors frequently to discuss the current security posture, learn about the latest threats, and identify vulnerable areas where additional monitoring or tighter access controls may be needed.
5. Provide Cybersecurity Awareness Training
Your employees are your first line of defense against cyber threats. Training them to recognize phishing attacks, follow best practices for cybersecurity, and identify potential threats is one of the most critical parts of any security plan. Training platforms like CybeReady can educate your team with engaging, ongoing training modules that effectively deliver crucial information for keeping your organization safe.
6. Utilize Real-Time Threat Detection and Prevention
Cybersecurity solutions that use AI and behavior analysis to detect emerging threats can save the day when attackers manage to breach your best defenses. These solutions can provide the 24/7 monitoring you need while analyzing network traffic and access requests to provide advance warnings of possible attacks.
7. Create an Incident Response Plan
Despite your best efforts, it’s always possible for a breach to occur, and when that happens, you want to have a plan for what comes next. Your incident response plan should outline the actions you need to take in the event of a data breach, with a clear delineation of responsibilities for each stakeholder.
SaaS Security is a Team Effort
Keeping your data safe in a SaaS environment requires a knowledgeable and proactive approach not just from the vendor and your cybersecurity team, but from every end user who accesses sensitive information and functionality from the cloud. Continual education is a cost-effective way to ensure everyone in your organization does their part to protect critical data.
CybeReady’s employee training platform provides engaging, accessible training modules with a proven track record of decreasing risky user behavior and creating a company culture of cybersecurity readiness.
Request a demo today and see for yourself how CybeReady can get your workforce on board with SaaS security best practices.