Is your information on the dark web? Chances are it’s likely one of the 24.6 billion username and password sets making their way around the dark web marketplace.
To manage and protect electronic or digital identities from theft, organizations include identity and access management (IAM) solutions in their cybersecurity stacks. With IAM, security teams can control user access to company resources and assets by role, permitted or unpermitted actions, and on a need-to-know basis.
Learn about the importance of identity and access control and the common authentication methods. Then, see our picks for the top 8 identity and access control management solutions in 2023.
Why identity and access control is important?
Identity and access control is critical for identifying, authorizing, and authenticating individuals. It secures access to company resources, including people, data, devices, systems, and software. Likewise, it protects against identity theft, data breaches, and illegal access to sensitive information.
With identity and access control in your cybersecurity strategy, your organization ensures:
- Enhanced data security
- Streamlined access privileges as security policies change
- Compliance with federal and industry regulations
- Lower risk of human error
- Centralized access management for more effective resource access
- Greater protection of confidential and sensitive data
- Access point management across browsers and devices
User authentication methods
To limit employee and customer access to an organization’s resources, information, and data, consider one of these four common approaches to user authentication.
Two-factor authentication
Two-factor authentication (2FA), or multifactor authentication (MFA), requires users to provide a password and at least one additional authentication tactic to prove their identity. For example, users might also provide a one-time password sent by email or text to make it more difficult for attackers to gain access.
Single sign-on
Single sign-on (SSO) enables users to employ a single user ID and password set through an identity provider to access multiple applications or websites. It minimizes the human risk of manually managing multiple credentials and reduces IT resources to reset passwords. Nonetheless, users must closely safeguard their credentials from theft.
Certificate-based authentication
Certificate-based authentication enables users to access data and resources securely through a digital certificate and public key cryptography. Because the digital certificate is saved on a user’s device or computer, they can sign into a browser, network, or system automatically. This method eliminates vulnerabilities that are prone to credential theft gained from phishing.
Secure password policy
A secure password policy is fundamental to authentication because passwords are the easiest target for cybercriminals. By creating a secure password policy, you restrict password reuse or incremental passwords; require complex, non-context-specific passwords; and enforce password changes at regular intervals. A password generator or password manager tool can reinforce your password policy.
Top 8 Access Control Management Solutions for 2023
With so many identity and access control management tools in the market, keep the following eight solutions at the top of your list.
1. Okta
The Okta platform offers a customizable and scalable cloud-based solution to secure workforce and customer identity access to your applications. Okta takes an identity-first approach to a zero-trust strategy, prioritizing role-based, context-specific user access to resources. You can define access policies and roles at granular levels and get real-time security and resource utilization reports.
Although experienced developers will find it easy to set up, some integrations might require additional development or technical support to complete. Also, some users have reported experiencing lockouts after changing devices.
Pricing: Okta offers a free trial for workforce identity and customer identity. Monthly pricing starts at $2/user and varies by product. Enterprise user pricing is also available.

2. IBM Security Verify
IBM Security Verify is built on a deep AI layer that provides context and intelligence to security decisions for consumers and workforce IAM. It protects users and apps in the cloud and on-premises. The core features include SSO, authentication, adaptive access, consent management, lifecycle management, and identity analytics.
More complex use cases and integrations can be challenging to configure the desired design and implementation. Also, smaller companies might find it harder on their budgets and not as user-friendly as they need.
Pricing: IBM Security Verify offers a 90-day free trial. Pay-per-use pricing is based on the number of features an organization needs. For example, monthly pricing for 5,000 SSO users starts at $1.71/user.
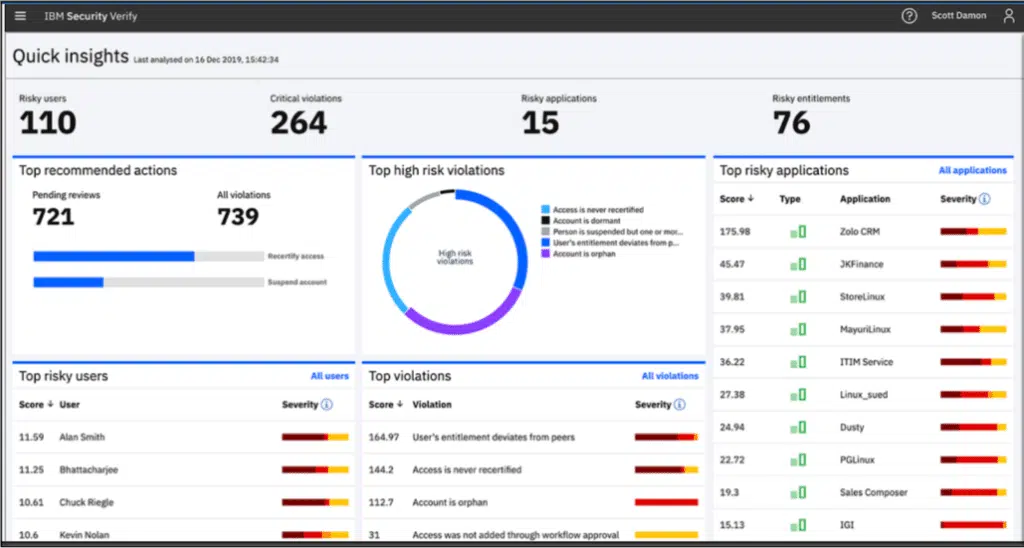
3. CybeReady
Although CybeReady isn’t a traditional IAM solution, its cybersecurity awareness training platform is a foundational layer of any cybersecurity protection stack. Based on data science, the platform delivers training in small bites in your employees’ workflow to change their behavior, decrease high-risk groups, and increase resilience scores.
Employees immediately identify risks regardless of job, level, or location and determine the best course of action to manage them. By giving them an active role in security, you empower them to take greater responsibility in safeguarding your organization’s information and assets, minimizing the human risk factor behind most cyberattacks.
Pricing: CybeReady offers a free trial. Contact the company for a demo and pricing information.
4. ForgeRock
The AI-driven ForgeRock Identity Platform is a complete IAM solution that scales to protect identities across the enterprise—including applications, customers, devices, workflows, and workforce. Available on-premises, in the cloud, and hybrid, the platform offers a seamless flow between digital channels and enforces OpenAPI security. ForgeRock is API-based, making it easy to install, configure, and integrate.
On the downside, its user management interface doesn’t allow for user segregation. It doesn’t provide advanced consent management capabilities to secure customer information properly. And it may require additional third-party tools to view and manage events and audit logs.
Pricing: ForgeRock offers a free trial. For pricing information, contact the sales team.
a
5. JumpCloud
JumpCloud offers identity, access, and device management on a single cloud directory platform. You can manage user identities and access to any resource and operating system in the enterprise. With its zero-trust security framework, you can stay on top of compliance requirements.
Despite having well-documented APIs and a powerful web GUI, the platform may require more technical expertise to install. It can also be difficult to upload custom applications into the management system, which can be challenging when offering custom applications to users.
Pricing: JumpCloud offers a free version for 10 users. For more users, it offers pay-for-what-you-need scalable pricing, with annual pricing starting at $24/user and monthly pricing starting at $3/user.
6. Microsoft Azure Active Directory
Microsoft’s IAM solution Azure Active Directory enables enterprises to manage identities and application access in the cloud or on-premises. It easily integrates with various tools and supports PowerShell scripts for easier maintenance, automation, and fine-tuning.
Azure Active Directory might not be ideal for small-to-medium businesses as it can require more IT resources and expertise to set up and implement. Also, for non-Microsoft users, it can come with a steep learning curve.
Pricing: Azure Active Directory comes with a free trial. Monthly pricing plans range from free to premium versions, starting at $6/user.
7. OneLogin
The OneLogin Trusted Experience Platform secures and centralizes workforce identity, customer identity, applications, and devices in one place. It offers a user-friendly and seamless experience for employees, customers, and partners. The platform includes a catalog of over 6,000 integrated applications, enabling SSO and user provisioning across the enterprise. It also secures access in real time using AI-powered capabilities.
While its APIs make it easier to provision data, some constraints might result in canceled operations or provisioning activities not working correctly. Some might find onboarding new users and adding new app connectors less than ideal.
Pricing: OneLogin offers an assessment and a 30-day trial. Monthly pricing starts at $2/user for workforce a-la-carte options and $4/user for package bundles.
8. Ping Identity
Ping Identity’s PingOne Cloud Platform orchestrates seamless and secure identity detection, verification, and authentication between users and assets. Its identity orchestration framework enables quick design of automated workflows that integrate identity vendors with no-code, drag-and-drop visual flows. It features strong identity management and SSO, with customization for specific use cases. As business processes and user requirements change, it enables rapid deployment, testing, and iterative fine-tuning.
While PingOne automates workflows, it doesn’t support all workflows and can be difficult to customize because of proprietary code. Also, some of the platform’s cloud-based products can present challenges for non-cloud security policies.
Pricing: Ping Identity offers a free trial. Monthly workforce pricing starts at $3/user, and annual customer pricing starts at $20,000.
Secure user and identity access with cybersecurity awareness training
Make identity and access control management a fundamental part of your cybersecurity strategy. Choose a complete solution that supports the methods you require to identify, authenticate, and authorize your workforce and clients to use your resources.
Reinforce your identity and access control management solution with cybersecurity awareness training. Regular, timely training creates a cybersecurity culture in your organization that values security, prevents phishing, and protects private and sensitive information.
Keep your employees’ and clients’ information off the dark web. Safeguard your clients, employees, and resources with cybersecurity awareness training from CybeReady. Take our 90-second virtual tour.