The surge of ransomware attacks in recent years shows no sign of slowing down. Even with international authorities cooperating and closing in to shut down some high-profile ransomware gangs recently, new threat actors emerge frequently and replace them. Evolutions in tactics or modifications to malicious files continue to result in damaging outcomes when companies become ransomware victims.
Widespread familiarity with ransomware attacks risks engendering a sense of complacency. But with a 2022 report showing that ransomware rose 13 percent over the last 12 months, there is a real need for more awareness about the types of attacks carried out against companies. This blog post will run through 8 types of ransomware attacks, including their impact, what they involve, and some infamous examples of their use to target organizations.
What is ransomware?
Ransomware is a type of malicious software that blocks access to systems or files using encryption and doesn’t return access until the victim pays a ransom. Threat actors that install ransomware on a system typically demand payment via cryptocurrency. Ostensibly, making the ransom payment means you get a decryption key that unlocks your files or systems, but these decryptors don’t always work.
Ransomware attacks are often complex multi-phase operations. Rather than simply dropping a malicious ransomware strain on a machine, there are many previous steps, including different payloads, command and control, lateral movement, and privilege escalation. The goal is to compromise many IT assets before finally launching the ransomware file and locking down multiple assets at once.
Many modern adversaries recognize that companies likely have backup strategies for their important systems and data. In attempting to increase the pressure to pay up, ransomware gangs now often exfiltrate data from systems before locking them down. With these double-extortion ransomware attacks, threat actors try to extort payments both for returning access to blocked systems and for victims to avoid having their stolen sensitive data assets published in forums or sold on the dark net.
A key distinction to be made: Crypto vs. Locker
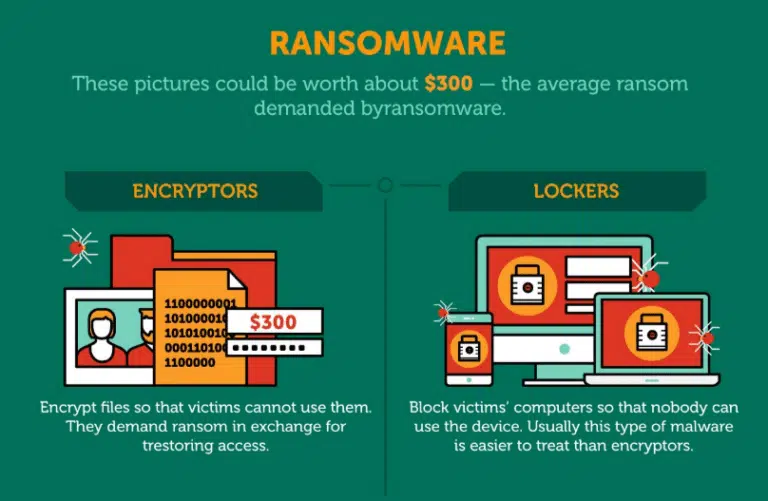
Before moving on to analyze some different kinds of ransomware attacks, it’s important to distinguish between two types of ransomware strains:
- Crypto ransomware strains focus on blocking access to essential files by encrypting them — you can still access basic computer functions.
- Locker ransomware strains completely lock users out of infected devices so that the only thing they can do is view a window that displays instructions for paying the ransom.
8 types of ransomware attacks
1. WannaCry
WannaCry attracted global media attention in 2017 when it rapidly spread to over 230,000 computers and impacted a number of high-profile organizations, including England’s National Health Service, car manufacturer Honda, and FedEx. This ransomware strain exploited devices running unpatched versions of Windows operating systems.
WannaCry’s ability to spread so rapidly came from its exploitation of the SMB communication protocol, which enabled it to propagate via a worm to other computers on a network and random computers on the Internet. Both US and UK governments blamed North Korean state actors for spreading WannaCry. In a compelling example of its impact, the NHS in England had to turn away patients because so many medical devices running unpatched Windows versions were compromised.
2. CryptoLocker
CryptoLocker kicked off the ransomware epidemic of the last decade back in 2013. This ransomware strain typically infected computers through a malicious email attachment, which installed a trojan on the system. The malicious file is also spread through a botnet.
CryptoLocker connected to command and control servers and used this connection to encrypt local files with asymmetric encryption. There were 500,000 victims of CryptoLocker, and the group responsible for this attack earned around $3 million in ransom payments.
3. BadRabbit
BadRabbit was a ransomware strain that used social engineering techniques to dupe victims into installing it. Masquerading as a Flash update, the malicious file requests Admin privileges from users and then drops other elements on systems. Inbuilt search features enable the malicious payload to find other vulnerable systems on the same network and exploit them.
BadRabbit hit nations including Ukraine, Russia, Turkey, and Japan. The most notable impacts were at Odessa airport, where flights were delayed due to infected systems, and at the Russian news agency Interfax.
 4. Locky
4. Locky
Locky ransomware was first discovered in 2016 when organizations began seeing ransom notes after unsuspecting users opened malicious email attachments. The Excel attachments appeared to be invoiced and requested macro approval to run. When a user is permitted to run macros, a trojan downloads and encrypted all files while watching certain extensions.
One notable example of Locky’s impact was that it sent Methodist Hospital in Kentucky into an internal state of emergency. In a similar incident, Hollywood Presbyterian Medical Center paid out $17,000 to the threat actors in return for the decryption key for sensitive patient data.
5. Ryuk
The Ryuk ransomware family was a particularly nasty type of ransomware attack and among the first strains to actively delete shadow copies of files on affected endpoints and remote backups on shared servers. Typically, initial access involved tricking users into installing a malware known as Trickbot, which established backdoor access into systems.
With their backdoor access, threat actors lurked for weeks or months to learn more about the network before distributing Ryuk ransomware files to multiple systems. Ryuk then encrypts all the important files on a given system. The group behind typical Ryuk attacks was known for its ruthlessness in targeting sectors like healthcare and public services. High-profile victims included Tribune Publishing, Universal Health Services (UHS), and The Imperial County government website in California.
6. Petya
Petya ransomware emerged in 2017 during a targeted campaign instigated by Russian threat actors against various organizations in Ukraine. The encryption focus of Petya was on entire systems running Windows so that infected systems couldn’t boot up.
Initial versions of Petya were delivered as email attachments, but a variant emerged in 2017 that propagated through the same vulnerability in Windows operating systems as WannaCry did. This new variant was named NotPetya. Victims included Ukrainian ministries, Danish shipping company Maersk, and multinational law firm DLA Piper. Maersk saw severe disruptions to services from this ransomware family, leading to an estimated $300 million in lost revenue.
7. GoldenEye
Golden Eye is a type of ransomware attack that relies heavily on exploiting users with low levels of cybersecurity awareness. Delivered as a phishing email with two attachments, a PDF instructs targets to open the accompanying Excel sheet. The Excel file leads users to permit macros, which sets the ball in motion for installing Golden Eye ransomware on the user’s system.
Golden Eye not only encrypts individual files; it also encrypts the Master File Table (MFT) and renders the machine unable to boot. GoldenEye is a recombination of Petya and another ransomware strain known as Mischa.
8. Jigsaw
Jigsaw ransomware appeared in 2016 when victims were met with unique ransom notes telling them that not only were their files encrypted, but those files would be gradually deleted if the ransom remained unpaid.
The initial intrusion for Jigsaw came in either spam emails or adware (malicious advertisements on websites). This ransomware attack did not laterally move to other devices. It also contained code weaknesses that meant it was relatively easy to recover from without needing to pay the ransom. But the unique tactic of encrypting files and threatening to delete them served as a warning for what sort of damages future, better-designed strains of ransomware could do.
Avoid being a victim of ransomware with cyber awareness training
Now that you understand how some common ransomware attacks work and their consequences, you’re better informed about the high risks that this form of cybercrime poses to your business.
Effective cybersecurity awareness training makes a huge difference in mitigating the threat of ransomware attacks. User actions, such as opening malicious email attachments, are often the triggering points that set ransomware attacks in motion.
But it’s difficult to run a program that employees engage with enough to transform your security culture. That’s where CybeReady comes in with a complete, fully-managed training program that’s easy to deploy, leverages automation, and focuses on maximizing awareness through engagement.
Request a demo today to improve cybersecurity awareness and reduce ransomware risks.














