The question on every InfoSec professional’s mind today is, “How can you protect your organization’s assets against the inevitability of data breaches while maintaining business continuity and minimizing risk?” To do this, you need a shield against cyber attacks that protects your organization externally and internally. That shield is a robust Information Security Management System (ISMS) that provides airtight policies and procedures to keep your company’s data safe from hackers, leaks, and other digital threats.
The threats are real, and each day, more news breaks of significant breaches affecting companies as diverse as MGM, MOVEit, PharMerica, and Twitter (X). It’s why 51% of organizations boost their security spending after experiencing a breach. They’re putting money into ISMS elements like better incident response plans, training employees on security, and getting advanced tools for spotting and dealing with threats.
However, an ISMS is a machine with many moving parts, especially in larger companies. For your organizational information security to reach a desired level of consistent excellence, you need to rely on an international standard for ISMS management: ISO 27001. Compliance with ISO 27001 is a surefire way to set up your ISMS according to current best practices for safeguarding information and cybersecurity assets.
Here’s everything you need to know about implementing ISO 27001 and passing a compliance audit.
ISO 27001 is a worldwide set of guidelines for Information Security Management Systems (ISMS) created by the International Electrotechnical Commission (IEC) and the International Organization for Standardization (ISO). This standard provides an organizational framework for the protection of information assets, ensuring confidentiality, integrity, and availability of data.
ISO 27001 assists organizations in becoming conscious of risks, encouraging them to actively find and tackle vulnerabilities. The standard advocates a comprehensive approach to information security, encompassing the assessment of personnel, policies, and technological systems. This approach ensures that all aspects of information security are thoroughly evaluated and strengthened.
Implementing an ISMS under ISO 27001 is instrumental in managing risks, enhancing cyber resilience, and achieving operational excellence.
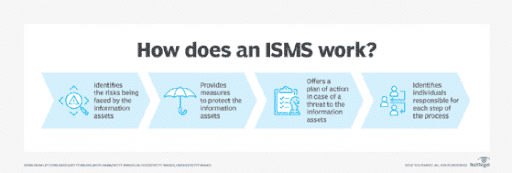
An ISO 27001 audit is a thorough examination to verify whether an organization’s ISMS complies with the standard. It involves assessing the effectiveness of security measures and policies in place. The audit is crucial in helping organizations identify areas for improvement, comply with international standards, and build trust with stakeholders and customers by showing a commitment to information security.
Compliance with the ISO 27001 standard is necessary for many data-intensive organizations, particularly in finance, healthcare, public services, and IT sectors where large-scale customer data handling is common. Driven by regulatory, contractual, or trust-building needs, compliance ensures robust data security.
Additionally, ISO 27001 compliance is advantageous for any organization seeking stringent information security management—from startups establishing secure practices to multinational corporations managing security across different regions.
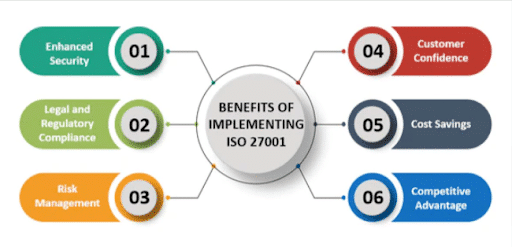
Adhering to the ISO 27001 standard for an ISMS brings multiple advantages:
The ISO 27001 standard outlines a comprehensive process for establishing and improving an ISMS, divided into 14 general phases:
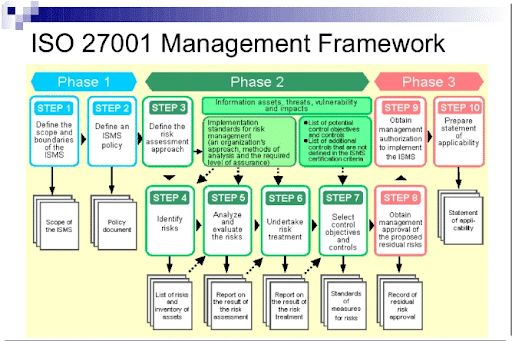
Achieving ISO 27001 compliance involves a comprehensive, structured approach over these ten steps:
Gain a thorough knowledge of the standard and its requirements.
Assess your current security against ISO 27001 standards to identify improvement areas.
Clarify the coverage of your ISMS within your organization.
Create a framework to guide the establishment and improvement of your ISMS.
Identify and evaluate potential security risks.
Apply the necessary measures from Annex A to address identified risks.
Ensure staff are informed about their role in the ISMS and can actively contribute to security by conducting cybersecurity awareness training.
Regularly check and update your ISMS to ensure its effectiveness.
Verify that your ISMS meets ISO 27001 standards and your security requirements.
Complete a certification audit by an accredited body to validate your ISMS’s effectiveness.
To pass an ISO 27001 audit and attain certification, an organization’s ISMS must incorporate:
For a more detailed exploration, the official ISO 27001 documentation and resources like CybeReady’s ISO 27001 checklist can provide guidance through the process.
Cybersecurity awareness training is essential to ISO 27001 compliance and is specifically addressed in two clauses:
This training is not just a formal requirement; it plays a vital part in reducing the security risks associated with human errors, a common factor in many security incidents. Cybersecurity awareness training significantly fortifies an organization’s ISMS by educating employees on security principles, specific threats, and their responsibilities.
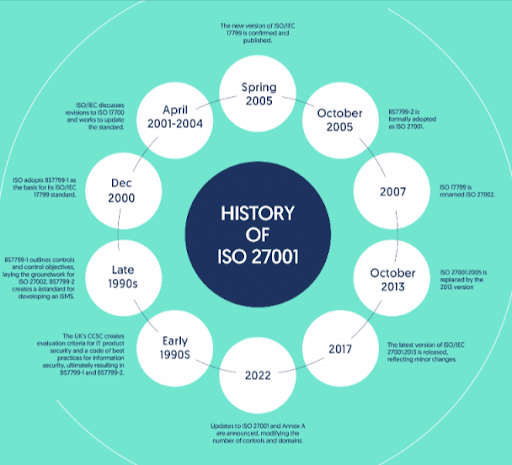
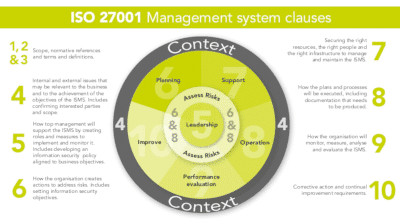
The current version of ISO 27001 is officially known as ISO/IEC 27001:2022. The international standard was jointly published by the ISO and the IEC in 2005, and later updated in 2013 and 2022. The standard is structured into several clauses, each focusing on different ISMS requirements. Annex A of ISO/IEC 27001:2022 details 93 specific controls organized into four themes.
Controls in ISO 27001 are specific measures or actions implemented to manage and mitigate risks to an organization’s information security. They are a critical part of an Information Security Management System (ISMS), and are designed to prevent security breaches, ensure data protection, and maintain the organization’s overall information security.
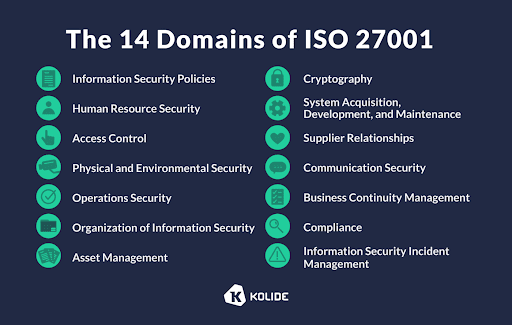
ISO 27001 controls provide a comprehensive framework for safeguarding information assets against security threats across critical areas, including access control, cryptography, physical security, and incident management. Each control in the framework guides organizations in recognizing threats, minimizing risk exposure, and implementing appropriate response measures.
However, not every organization needs to apply all of the controls. Their applicability depends on the outcomes of a thorough risk assessment. ISO 27002 complements ISO 27001 by offering guidance on the practical implementation of these controls, tailored to each organization’s unique needs and risks.
When organizations select and apply ISO 27001 controls relevant to their operations, they can achieve a robust system for handling cyber threats. The benefits of adopting ISO 27001 controls include:
Significantly reduces the risk of data loss from cyber incidents.
Meets various data protection standards required by governments and industries.
Minimizes damage from cyberattacks, aiding in a quicker return to normal operations.
Demonstrates a commitment to strong cybersecurity practices, improving reputation among customers and partners.
The ISO 27001 standard was significantly updated in October 2022, marking its first major revision since 2013. This update reflects the evolving landscape of online fraud and cybercrime, enhancing the standard’s ability to address contemporary threats.
Changes include a restructuring of clauses and the Annex A controls. Notably, the Internal Audit and Management Review clauses were subdivided, and a new clause, Planning for Changes, was introduced.
Additionally, the Annex A controls saw a significant overhaul, including the reorganization of the original 114 controls into fewer categories (reduced to four themes from the original fourteen domains) and the introduction of eleven new controls, resulting in a new total of 93 controls.
When assessing your organization’s risk factors, these new ISO 27001 Annex A controls offer practical steps for protection:
Collect and analyze security threat data to create actionable intelligence.
The success of this control hinges on the ability of your staff to identify and react to threats appropriately. Security training platforms like CybeReady are essential for educating staff on their roles in effectively implementing this and other ISO 27001 controls.
Implement secure practices for using and managing cloud services, emphasizing strong policies and user training due to the remote nature of cloud data.
Ensure robust ICT systems to maintain operations during cyber disruptions, focusing on planning, hardware, and training.
Protect areas with sensitive data and hardware from physical breaches, considering measures like surveillance and security patrols.
Define and regularly review security configurations of technological assets to prevent unauthorized alterations.
Develop data retention policies and practices for safe data deletion when no longer needed.
Use data masking techniques like encryption to protect sensitive data, particularly in the development or testing phases.
Monitor and minimize data leakage risks across various channels and devices.
Continuously monitor networks and systems for unusual activities and respond promptly to potential security breaches.
Restrict access to external websites to reduce malware risks and unsafe user behaviors.
Implement secure coding practices, maintain secure development environments, and thoroughly document changes.
ISO 27001 is recognized globally for its effectiveness in establishing robust Information Security Management Systems, enabling organizations to manage sensitive information, prevent breaches, adhere to regulations, and earn trust from customers and stakeholders. Achieving compliance with this standard is significantly enhanced by comprehensive cybersecurity awareness training.
CybeReady’s training programs and AuditReady compliance tool are designed to equip your workforce for this challenge, ensuring they are prepared to face both evolving cyber threats and a rigorous ISO 27001 audit. Engaging, effective, and customizable, CybeReady’s training programs enable your team to meet the mandates of ISO 27001 and create a human firewall within your ISMS.
To discover how CybeReady can support your ISO 27001 compliance efforts and bolster your cybersecurity posture, book a free demo today.





Copyright © 2025 – CybeReady
We will reach out to you shortly.
In the meantime, please check out our complimentary CISO Tool Kit
Wir werden uns in Kürze bei Ihnen melden.
Schauen Sie sich bitte in der Zwischenzeit das kostenlose CybeReady CISO Tool Kit an.
We will reach out to you shortly.
In the meantime, please check out our complimentary CISO Tool Kit, or visit Our Blog
We will reach out to you shortly.
In the meantime, please check out our complimentary CISO Tool Kit, or visit Our Blog