You’re settling into your day, ready to tackle the fresh stack of emails awaiting your attention.
One email leaps out at you among the mix of routine updates and office chatter. “URGENT! We’ve detected suspicious activity on your bank account. Click here to verify your account now.”
A sense of dread creeps in, and your heart beats a little faster, but wait… let’s hit the pause button here. This could be a classic case of a phishing email.
We’ve all been there. This is a cyber boogeyman that’s more common than you might think. Phishing emails can pose real threats, such as risking your hard-earned savings, confidential data, or even digital identity.
But here’s the good news: once you know what to look for, these phishing scams don’t stand a chance.
In this edition, we will navigate the murky waters of phishing emails together. We’ll get to know what they are, how you can spot them like a pro, and how you can protect your precious information from getting into the wrong hands.
Ready to turn the tide on these cyber threats?
Let’s dive right in.
What Are Phishing Emails?
Phishing emails are fake emails sent by cybercriminals who aim to trick you into revealing sensitive information, such as passwords, credit card numbers, or Social Security numbers.
The term “phishing” is a play on the word “fishing,” reflecting the criminals’ strategy of “baiting” individuals into falling for their scams.
Phishing emails are typically designed to appear as if they come from a reputable organization or person, such as a bank, a social networking site, a payment platform, or even a colleague or friend.
They often employ tactics to induce a sense of urgency or fear, pressuring you to take action quickly without scrutinizing the email’s legitimacy.
The Purpose Behind Phishing Emails
Phishing emails are sent out with specific, nefarious intentions. Let’s break down five core reasons behind these deceptive messages:
- Stealing Personal Information: The main goal is to trick you into revealing your sensitive data, paving the way for identity theft or financial fraud.
- Spreading Malware: These emails often contain harmful links or attachments. Once clicked or downloaded, they can infect your device, giving cybercriminals a backdoor into your system.
- Gaining Unauthorized Access: Phishing emails can be the key for hackers to access and control your personal or corporate accounts, leading to a further spread of scams or data breaches.
- Corporate Espionage: To gain a competitive edge, cybercriminals use phishing emails to infiltrate a company’s network, aiming to steal valuable corporate data.
- To Extort Money: Sometimes, these emails could be laced with ransomware. Once your device is infected, the hacker could lock your files, demanding a ransom to release them.
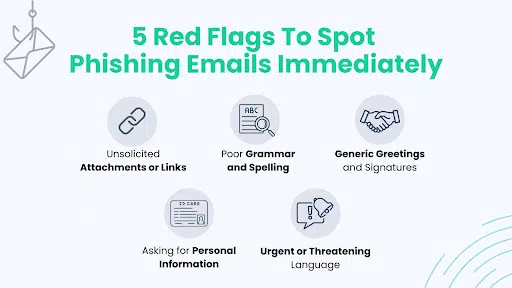
5 Red Flags To Spot Phishing Emails Immediately
- Unsolicited Attachments or Links: If you don’t recognize the sender, or if the email wasn’t something you were expecting, be extremely wary of any attachments or links. Phishing emails often contain links or attachments that, when clicked or opened, can install malware on your device or take you to a fraudulent website designed to steal your information.
- Poor Grammar and Spelling: It might be a phishing attempt if you notice many spelling or grammar errors in an email. Legitimate organizations usually have a team of copy editors that will not allow a mass email full of grammar errors to go out.
- Generic Greetings and Signatures: Phishing emails often use generic greetings like “Dear User” or “Dear Customer.” If you have an account with the business, they probably know your name and would use it in their emails. Similarly, the signature may lack details about the sender or the company.
- Asking for Personal Information: Legitimate businesses will never ask for personal information, like your password, bank account details, or Social Security number, via email. If you’re being asked to provide this information, it’s likely a phishing attempt.
- Urgent or Threatening Language: Phishing attempts often rely on scare tactics to trick people into taking action. They might say that your account will be closed, you’ll be fined, or you’ve been the victim of a crime. Legitimate businesses will usually provide a way to contact them if you’re facing an issue.
Examples Of Phishing Emails
- Account Verification: “Your PayPal account will be suspended within 24 hours due to suspicious activity. Click here to verify your account.”
- Prize Winning: “Congratulations! You’ve won an iPhone 13 in our lucky draw. Click here to claim your prize.”
- Password Reset: “We have received a request to change your Google password. If you did not make this request, click here to secure your account.”
- Friend in Distress: “Hey, I’m stuck overseas and lost my wallet. Can you wire me some money?”
- Job Offer: “Your application was accepted! Download the attached file for full job details and contract.”
- Software Upgrade: “Your Microsoft Office subscription has expired. Click here to renew.”
All these examples feature common elements of phishing emails – they mimic trusted entities, create a sense of urgency or fear, and prompt you to click a link or download an attachment. If you receive emails like these, be cautious and don’t interact with them before verifying their legitimacy.
How To Protect Yourself From Phishing Emails
While it may not be possible to stop all phishing emails from reaching your inbox, there are several steps you can take to minimize their impact:
- Never Click On Suspicious Links: If you’re unsure about a link, avoid clicking it.
- Use Spam Filters: Keep spam filtering on for your email. It’ll catch many tricky phishing emails and dump them in your spam box.
- Keep Software Updated: Keep your devices and antivirus software up-to-date. The latest versions often have stronger defenses against phishing and other threats.
- Enable Two-Factor Authentication (2FA): 2FA is like a second lock on your account. Even if hackers get your password, they’d need your second factor (like your phone) to get in.
- Knowledge Is Power: Stay in the know about new phishing scams. Share the knowledge with your team or friends so that they can spot the signs too.
- Don’t Feed The Phish: Received a suspicious email? Don’t reply. It tells the sender your email address is active and can lead to more spam.
- Use A Firewall: A firewall is like your device’s personal shield. They give you an extra layer of protection against nasty online threats.
- Report Phishing Attempts: Got a phishing email? Don’t forget to report it to your email provider, the company being impersonated, and relevant authorities. Your report could save someone else from falling for the scam.
You’re No Longer An Easy Target. You’re A Phishing-Fighting Champ!
Navigating cyber threats can feel overwhelming, but remember, knowledge is your secret weapon. Remember, phishing isn’t just some internet bug—it’s a serious cyber risk that can wreak havoc in your real life if left unchecked.
Now you know what to look out for, you’re well-equipped to defend yourself. Don’t let these cyber scams get the best of you.
Staying safe online isn’t a one-time thing – it’s all about those good daily habits. Keep these tips in mind, and before you know it, spotting a phishing email will be as natural as spotting a tomato in a fruit salad.
As you go about your day, surfing the web and responding to emails, just remember to stay sharp and trust your instincts. If something feels off, it probably is.
And remember, we’re here to help at CybeReady. We offer practical solutions to help you and your team stay safe online. So, why not drop us a line? We’d love to chat about how we can help you keep your online world secure.