Are you prepared to face the growing threat of cybercrime in your software supply chain? As more organizations go digital, the threat of growing cybercrime rates has become more pressing than ever.
Regulatory bodies have responded to the growing threat by updating the National Institute of Standards and Technology’s (NIST’s) foundational cybersecurity supply chain risk management (C-SCRM) guidance. They have released an expanded version that covers new threats and vulnerabilities called the NIS2.
Over the past 5 years, 89% of companies reported experiencing an event related to supply chain risk. According to Gartner, by 2024, 45% of organizations worldwide will experience an attack on their software supply chain – a three-fold increase from 2021.
With cybercrime growing exponentially, it’s not a matter of if but when your organization will experience an attack on your software supply chain. So even organizations not required to comply with NIS2’s updated regulations benefit from implementing the advanced security practices it requires.
In this article, we explore what NIS2 is, what recent changes are being implemented, and provide a step-by-step guide for planning your compliance strategy.
Facing the Modern Threat Landscape: The Importance of Understanding the NIS2 Directive
Many European countries have experienced a surge in cyberattacks over the past several years, with attackers using more sophisticated methods to exploit vulnerabilities. For example, in 2021, the Irish healthcare system suffered a ransomware attack that led to the shutdown of its IT systems. Healthcare systems around the world dealt with similar attacks. In the same year, cyberattacks across Europe doubled. As recently as this year, a major hospital in Barcelona was hit with a cyberattack that caused significant disruptions to its operations.
Experts predict that by 2024, cyberattacks will cost industries worldwide up to $10.5 trillion, and the urgency to manage cyber threats has peaked in governing bodies around the globe. The European Parliament has responded to this threat by developing the NIS2 Directive, an extension of the former NIS Directive that aims to establish a common level of cybersecurity across the European Union.
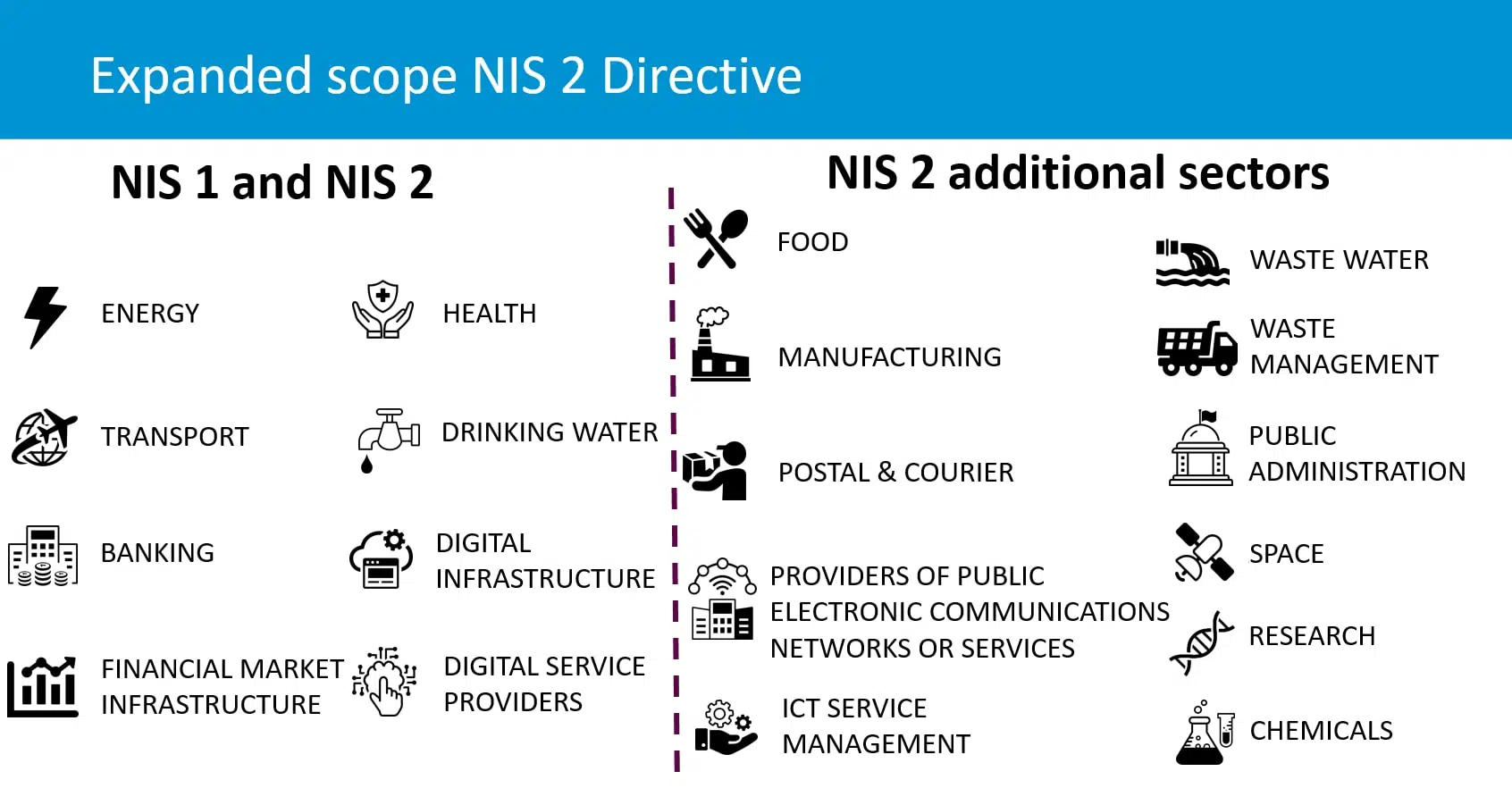
Effective January 16, 2023, the directive requires critical infrastructure operators to implement appropriate and proportionate measures to ensure the security of their systems. While policymakers believe that public interest in critical infrastructure provision justifies legal requirements to harmonize risk behavior across all providers, this harmonization comes at a cost. Harmonization requires operators to implement operational cybersecurity and provide documentation to prove compliance.
The NIS2 Directive also requires entities subject to it to comply with legal obligations by October 18, 2024. Furthermore, organizations will be judged not only by whether they are affected by a cyberattack but also by the nature of their response and preparedness for the attack. Therefore, it is essential for organizations to understand what NIS2 is, why it has been developed, and how it impacts them. By enhancing the scope of included entities and introducing new cybersecurity risk management requirements, the NIS2 Directive plays a critical role in managing the rapidly-evolving cyber-threat landscape.
Navigating NIS2: Who Falls Under the Scope of the New Directive?
If you operate a business or organization in Europe, you may wonder whether the NIS2 Directive applies to you. The answer depends on various factors, including the sector in which you operate, your company size, and your organization’s importance to society.
The NIS2 Directive applies to private or public entities considered essential. According to the directive, determining whether an entity is essential or important depends on the sector in which it operates and the organization’s size.
Generally, only medium and large organizations are in the scope of NIS2, primarily large companies with more than 250 employees and medium-sized companies with 50–250 employees. Companies with less than 50 employees or an annual turnover of less than 10 million EUR are excluded unless they are deemed of critical importance to society.
But regardless of size, complying with NIS2 is crucial. The directive significantly enhances the scope of cybersecurity risk management requirements that entities must adhere to as a minimum standard. It also prepares the ground for inspections that may take place before or after significant incidents occur. Failure to comply with NIS2 could lead to substantial penalties and damage your reputation.
Whether your organization falls within the scope of NIS2 or not, it’s important to stay informed about the directive’s requirements and the potential impact on your operations. Taking a proactive approach to cybersecurity risk management can help protect your business and maintain the trust of your customers and stakeholders.

10 Key Steps for Establishing NIS2 Compliance
Whether you are a small business or a large enterprise, ensuring compliance with NIS2 requirements is not only essential from a legal perspective but can also help ensure the security of your digital infrastructure. The following steps can help you comply with the NIS2 requirements while ensuring your digital security remains robust:
1. Establish a Strong Cybersecurity Governance Framework
The first step in creating a comprehensive cybersecurity strategy is establishing a strong governance framework. This involves identifying and documenting the roles and responsibilities of key stakeholders, including the board of directors, senior management, and IT personnel. It is important to define clear lines of authority and communication channels to ensure that all stakeholders know their responsibilities and are aligned with the organization’s overall cybersecurity objectives.
2. Implement Regular Employee Awareness Training
Employees are often the weakest link in an organization’s cybersecurity defenses. While cybercriminals know this, educating your employees and creating a culture of security can transform them into your strongest defense. Therefore, it is crucial to provide regular cybersecurity awareness training to all employees on the latest threats and best practices for safeguarding the organization’s digital assets. This training should cover password management, phishing scams, and the importance of reporting suspicious activities immediately.
CybeReady makes it easy to implement digestible, timely, and engaging training at regular intervals to ensure your entire team appreciates the importance of cybersecurity and can recognize and report threats as soon as they appear.
3. Establish a Comprehensive Incident Response Plan
No matter how robust your cybersecurity defenses are, it is still possible for a cyberattack to occur. Therefore, it is essential to have a comprehensive incident response plan in place to enable a rapid counteraction of any incidents, particularly as managing cyber threats is a significant part of how NIS2 compliance is evaluated. This plan should include clear guidelines for detecting and reporting incidents and a step-by-step process for containing and mitigating the damage.
4. Conduct Regular Risk Assessments
Regular risk assessments are critical for identifying potential vulnerabilities in your digital infrastructure. These assessments should be conducted regularly to identify any new threats or weaknesses in your security defenses and to assess the overall security of your supply chain. The results of these assessments should inform your cybersecurity strategy and identify areas that require additional resources or attention.
5. Establish Supply Chain Security

In addition to regularly assessing the risk of their supply chain, organizations should ensure that their supply chain partners also comply with NIS2 requirements daily to reduce the risk of third-party cyberattacks. This involves implementing security measures into the supply chain, such as vendor risk assessments and audits, contractual agreements that specify security requirements, and ongoing monitoring and communication with suppliers. By ensuring that suppliers also comply with the updated NIS2 requirements, organizations can reduce their overall risk and ensure the security of their digital infrastructure.
6. Regularly Update and Patch Your Infrastructure and Applications
One of the most common ways cybercriminals gain access to an organization’s digital assets is through unpatched vulnerabilities in infrastructure and applications. Therefore, it is crucial to regularly update and patch your digital infrastructure and applications to ensure that all known vulnerabilities are addressed.
7. Use the Right Threat Identification Tools
To comply with NIS2 requirements, you will need to use the correct tools to identify potential threats to your digital infrastructure. Various threat-hunting tools available, such as intrusion detection systems, threat intelligence platforms, and security information and event management (SIEM) systems. Using these tools can help you detect and respond to potential threats before they cause any damage.
8. Implement Monitoring and Threat Intelligence
While using the right threat identification tools is essential, monitoring threat feeds to stay up-to-date with the latest cyber threats is just as important. Threat intelligence feeds are great sources of real-time intelligence that provide information about potential cyberattacks, vulnerabilities, and malicious activities. Monitoring these feeds can help you proactively prevent cyberattacks and ensure your digital infrastructure remains secure.
9. Implement Robust Network and Endpoint Security
Network and endpoint security are critical components of any comprehensive cybersecurity strategy. This involves implementing robust firewalls, intrusion detection systems, and antivirus software to protect against external and internal threats and address potential attack vectors. Additionally, endpoint security measures such as data encryption and access controls can significantly reduce the risk of unauthorized access to sensitive data.
10. Conduct Regular Security Audits
Finally, it is essential to conduct regular security audits to ensure that your cybersecurity strategy is effective and aligned with your organization’s overall objectives. These audits should be conducted by an independent third party and include a comprehensive review of your cybersecurity governance framework, risk assessments, incident response plan, and security controls.
Battling Modern Security Threats with Education
Protecting your business against cyberattacks is critical, especially with the surge in sophisticated attacks. The new NIS2 Directive extends the NIS Directive to address the modern and evolving threat landscape. Complying with its requirements, whether your organization is obligated to or not, is crucial to maintain a robust security landscape.
Having your entire organization on board and aware of new security regulations can help add an extra level of security by spreading the responsibility for its digital safety to all its members. Additionally, by having employees across the board on the lookout for potential threats and vulnerabilities, you can address security flaws before they lead to cyberattacks.
At CybeReady, we’ve developed a platform that provides engaging, educational, and regularly-updated employee programs for you, keeping your employees up to speed on the latest strategies used by attackers and preventing your organization from falling victim to scams. Schedule a demo today to see how CybeReady can foster a security-first culture in your organization.













