With cyberattacks on websites and web apps proliferating like never before, savvy developers and website admins employ a Content Security Policy (CSP) to help prevent code injections and Cross-Site Scripting (XSS) attacks that exploit vulnerabilities in a web application’s code. But sometimes the safety of a standard CSP is not enough. Just like riding a motorbike, it’s safer to wear a Helmet.
A recent study showed that XSS attacks now account for half of the high-risk findings in web apps. These attacks execute malicious code on a website or steal sensitive information. Scripts, stylesheets, and graphics are just a few examples of information that can be exploited as sources to access a web page to accomplish this.
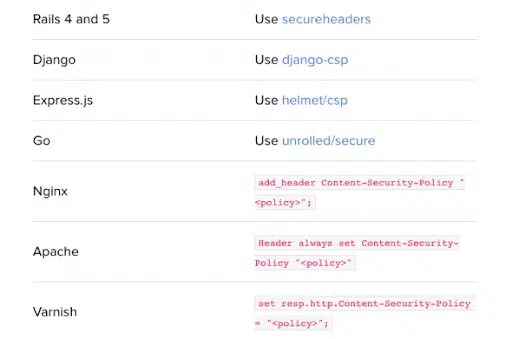
Fortunately, the CSP header can be modified to enable or deny a particular category of externally produced information. Web designers can create a policy that limits the kinds of content permitted to be loaded onto their pages by employing a CSP, which lowers the possibility of destructive assaults.
To prevent these attacks and protect websites and apps, any web application that manages sensitive data, such as user passwords or payment information, must have a CSP or equivalent vulnerability management program. Web applications can be further protected by prohibiting the loading and use of inappropriate content on a page. Web developers can employ a CSP to guarantee that online programs are secure for users while also lowering the possibility of security vulnerabilities.
A more secure option than a standard CSP is a Helmet Content Security Policy [aka helmet.contentSecurityPolicy() ], which is a powerful option to secure HTTP headers. This post will explore the Helmet CSP, why you should use it, and how to set it up.
What Is Helmet.js?
A helpful Node.js package called Helmet.js enables you to secure HTTP headers returned by your Express apps, a Node.js application that uses the Express framework to manage HTTP requests and responses. This package lets you construct middleware functions and routes to conduct numerous activities like handling errors, validating data, and parsing request bodies.
Express is a Node.js framework that makes it simple to build dependable and scalable online apps and APIs thanks to its extensive features and tools.
Although an integral feature of the HTTP protocol, HTTP headers are typically invisible to end users. The headers provide important metadata about the HTTP request or response, allowing the client (browser) and the server to convey more data in a transaction.
Helmet.js offers several middleware capabilities that can be used to set security-related headers in HTTP responses, including X-XSS-Protection, Strict-Transport-Security, Strict-Transport-Security, and Content Security Policy (CSP).
With Helmet, developers can enhance the security of their web applications by preventing various attacks, including code injection, click-jacking, and Cross-Site Scripting (XSS).
Developers can design HTTP headers that lessen the possibility of security flaws in their web applications by utilizing Helmet’s middleware services.
The Content Security Policy (CSP), one of Helmet’s core features, aids in preventing XSS and other attacks by defining which sources are permitted to load resources on a web page. Scripts, stylesheets, and pictures are a few examples of the types of external content that can be accepted or blocked by changing the CSP header.
What is a Helmet Content Security Policy?
OK, yes, we know that Node.js isn’t a British motorcycle, but just as you should wear a helmet with your Norton Commando, you should be using Helmet.js to protect your Node.js from a potential cyber assault. The well-known Node.js package Helmet.js can secure your Internet apps by monitoring, managing, and controlling their HTTP headers.
A Content Security Policy (CSP), which is one of the core features of Helmet.js, can assist in preventing Cross-Site Scripting (XSS) and other attacks by defining which sources can load resources onto your web page. Scripts, stylesheets, and pictures are a few examples of the types of external content that can be accepted or blocked by changing their CSP headers.
Developers can dramatically lower the likelihood of security issues on your online apps and increase their resistance to harmful assaults by utilizing Helmet’s CSP capabilities.
Why Should You Secure HTTP Headers with Helmet.js?
Helmet.js HTTP header security is crucial for the following reasons:
First, code injection, click-jacking, and Cross-Site Scripting are just a few of the web application assaults that Helmet.js can prevent.
To help stop these attacks, Helmet offers middleware functions that can set HTTP headers like X-XSS-Protection, Strict-Transport-Security (HSTS), and X-Content-Type-Options.
Second, using Helmet.js to secure HTTP headers can help increase your online applications’ security. Developers can aid in preventing unauthorized access to sensitive data, such as financial data and user Personal Identifiable Information (PII), by securely defining HTTP headers.
Third, Helmet.js also contributes to the acceleration of web applications by optimizing HTTP headers. Developers can speed up page load times and user experience by reducing the number of server queries their sites deploy by using HTTP headers like cache-control and ETag.
Fourth, by safeguarding HTTP headers, Helmet.js can assist online applications in adhering to a variety of security standards and laws, such as the Payment Card Industry Data Security Standard (PCI DSS). Any application that manages sensitive data, such as credit card information, must adhere to these specifications.
Lastly, to increase the security, efficacy, and compliance of online services, HTTP header security using Helmet.js is required. Developers can aid in averting attacks, strengthening the security posture of their applications, and adhering to important security standards and laws by using Helmet’s middleware technologies to provide appropriate HTTP headers.
How to Set Up a Helmet Content Security Policy
Setting up a Content Security Policy (CSP) using Helmet is a key step in securing your web application. Here are the steps to set up a Helmet Content Security Policy:
- Install the Helmet package using npm or yarn, two popular package managers used by JavaScript and Node.js developers. They facilitate the usage of a project’s dependencies, which is anything on which a project depends or a piece of code that is necessary for it to function correctly.
bash
npm install helmet
or
bash
yarn add helmet
- Import the helmet package into your Node.js application:
javascript
const helmet = require(‘helmet’);
- Use the helmet.contentSecurityPolicy() middleware function to set up the CSP policy:
javascript
app.use(helmet.contentSecurityPolicy({
directives: {
defaultSrc: [“‘self'”],
scriptSrc: [“‘self'”, “‘unsafe-inline'”, ‘example.com’],
styleSrc: [“‘self'”, “‘unsafe-inline'”],
imgSrc: [“‘self'”, ‘example.com’],
connectSrc: [“‘self'”],
fontSrc: [“‘self'”],
objectSrc: [“‘none'”],
mediaSrc: [“‘self'”]
}
}));
In the above example, we set up the following directives:
- defaultSrc: sets the default source for all types of resources to ‘self’.
- scriptSrc: sets the allowed sources for JavaScript code to ‘self’, ‘unsafe-inline’ (allows inline script), and ‘example.com’.
- styleSrc: sets the allowed sources for CSS styles to ‘self’ and ‘unsafe-inline’ (allows inline style).
- imgSrc: sets the allowed sources for images to ‘self’ and ‘example.com’.
- connectSrc: sets the allowed sources for network connections to ‘self’.
- fontSrc: sets the allowed sources for fonts to ‘self’.
- objectSrc: sets the allowed sources for objects (such as Flash and Java applets) to ‘none’ (disallows any object).
- mediaSrc: sets the allowed sources for media (such as audio and video) to ‘self’.
In the example below, we have set the default-src directive to ‘self’ in the HTTP header. You can also set other directives in the HTTP header, but make sure they match with the ones you set in the directives object in the helmet.contentSecurityPolicy() middleware.
javascript
app.use((req, res, next) => {
res.setHeader(‘Content-Security-Policy’, “default-src ‘self’;”);
next();
});
OK, Helmet On, Let’s Go!
To sum it up, Helmet.js is a Node.js package that offers middleware capabilities to secure HTTP headers in HTTP responses, including X-XSS-Protection, Strict-Transport-Security, and Content Security Policy (CSP). CSP can prevent code injection and Cross-Site Scripting (XSS) attacks by specifying which external content sources are allowed to load resources onto a web page.
Using Helmet’s CSP capabilities, developers can significantly lower the likelihood of security issues in their online applications and improve their resistance to harmful attacks. Securing HTTP headers with Helmet.js can also increase online applications’ security, optimize HTTP headers, and ensure compliance with various security standards and laws.
Of course, while Helmet.js will offer you extra protection against cyber threats, equally important is creating a company culture where everyone has cybersecurity awareness and uses best practices. CybeReady is an industry leader in cybersecurity awareness training, offering a complete security awareness solution for employees.
Try a free demo of CybeReady and see how they can prepare your organization to deal with potential cyberthreats, because awareness is always the best safety helmet.