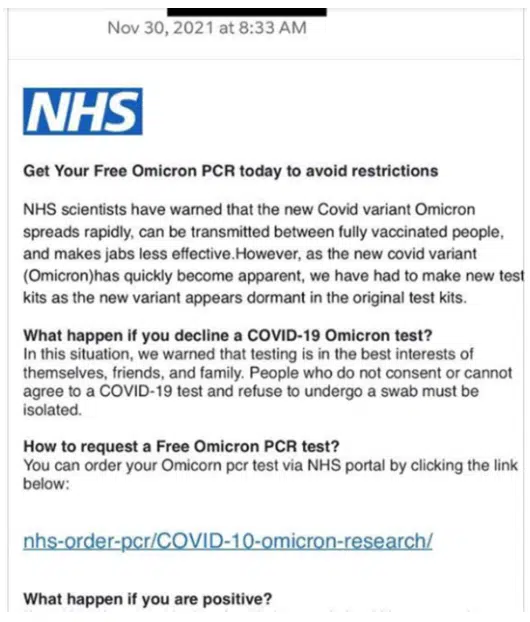
Another variant, another phishing scam. It seems like every time a new COVID-19 strain hits the headlines, a new wave of cyberattacks follows in its wake.
With the Delta variant, it was scams that asked email users to verify their vaccination status, and with Omicron, the media is already reporting phishing scams centered around an “Omicron PCR test”, supposedly from the National Health Service in the UK, but really sent by attackers to gain access to sensitive information.
Why do COVID-19 phishing scams work, and are they part of a larger risk for today’s businesses?
Government-related phishing scams: a growing concern
Phishing scams grew 220% during the peak of the coronavirus last year, but the truth is, COVID-19 is just the latest example in a long string of phishing scams that mimic official government agencies. One of the reasons why scams mentioning the Coronavirus are so effective right now is because they are leveraging a “current event” which tricks the receiver into trusting the correspondence. After all, this email has contextual relevance, so it makes sense that they are receiving it at this time.
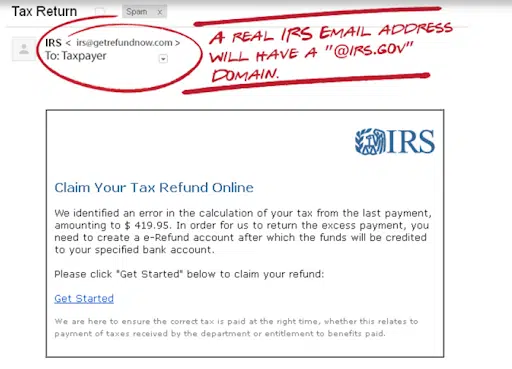
The example above faked correspondence from the National Health Service, but other government entities scammed include the Internal Revenue Service, government welfare funds, census-related frauds, or official organizations such as the World Health Organization. This trend can even include lottery and sweepstake organizations that are not owned by the government but receive government incentives.
If you’re asking yourself, “Why are these types of scams so popular?” you’re asking the wrong question. They’re popular because they work. The real question should be… “Why do they hit the mark?”
1. Governments already handle our sensitive information
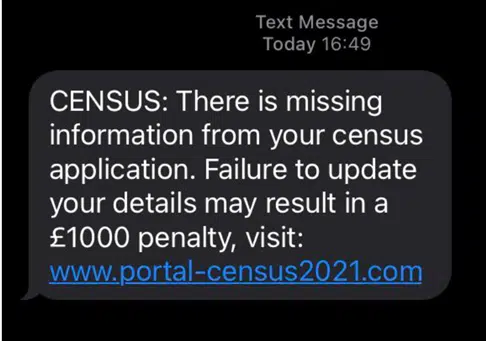
If you see an email or a text message that is allegedly from the Census Bureau, like this example below, similar to those the Leicestershire police warned against in 2020, you’re much more likely to be tricked into entering your sensitive information. The attackers can effectively skip the step where they need to establish trust. In contrast, if an unknown sender or an independent business asks for details such as your mother’s maiden name or your social security number – you’re likely to think twice.
In the US, the Census Bureau has warned that they will only ever use the mail system to collect census information, and so email or text messages are likely to be a scam.
2. The government has legitimate reasons to give us money
3. Correspondence with authority is likely to instill fear

The example scam below preys on a similar kind of fear. The Delaware Division of Revenue has warned against correspondence from a fake tax processing unit that frightens recipients into believing their property will be seized due to unpaid taxes.
When people read a scam that threatens a loss of property, or with COVID-19 scams, tells the reader that they are risking ill health, they are more likely to act impulsively and ignore warning bells. This response is only increased when the communication arrives from a seemingly legitimate source – ie, a governmental agency or authority. When we see authority, people have a tendency to acknowledge it and do what they say, and so in this case we are far more likely to let our guards down and make that wrong click.
What can businesses do to protect employees from government-related scams?
Especially as employees continue to work from home and businesses increasingly rely on BYOD policies, it’s essential to recognize that the company network can be impacted by employee behavior even from their mobile phone or in their free time.
That’s why you need to make sure you’ve alerted your employees to the rise in COVID-related phishing scams and reminded them of best practices like checking the sender’s name for an official .gov domain, looking out for spelling and grammatical errors, or leaving the email and going directly to the government website to check for the right information, even if they feel confident in the correspondence. It’s also smart to ask for a complete separation between an employee’s personal email and their work email, making it less likely they will expect to receive an email from an authority in their work inbox.
Thanks to the combination of trust, fear, and legitimacy, government-related phishing scams are nothing new. When COVID-19 is behind us, the attackers will move on to take advantage of the next headline. Ultimately, protecting your business is about ensuring your employees have the chance to practice safe behavior, with continuous training for cybersecurity awareness as part of their daily work.
Ready to see how CybeReady’s complete security awareness training platform works? Schedule a demo.