Contemporary healthcare organizations are obligated to protect a vast amount of sensitive patient data due to the broad definition of Protected Health Information (PHI) under the Health Insurance Portability and Accountability Act (HIPAA). The proliferation of electronic health records, digital health technologies, and the need for data sharing across a complex web of providers, insurers, and third-party services have significantly increased the amount of health data that must be safeguarded.
This data-rich environment is a magnet for cybercriminals, which is bad news for the cybersecurity of healthcare organizations and their patients. Unfortunately, the healthcare industry continues to set unwelcome records concerning exposed patients’ data. In 2023, a staggering 725 data breaches left over 133 million records exposed. These worrying numbers highlight the critical need for more stringent privacy measures in healthcare.
Fortunately, security guidelines such as HIPAA and the Privacy Act are already in place to safeguard patient information and confidentiality. However, the effectiveness of these regulations relies heavily on the thorough training and proficiency of healthcare professionals and staff who manage patient data daily.
Ultimately, the key to safeguarding patient privacy lies in an ongoing commitment to building a compliant, security-focused culture—and the first step is a robust training strategy.
What is HIPAA and Privacy Act training?
HIPAA and Privacy Act Training provides healthcare workers and associated personnel with detailed guidance on the legal obligations of the Health Insurance Portability and Accountability Act (HIPAA) of 1996 and the Privacy Act of 1974.
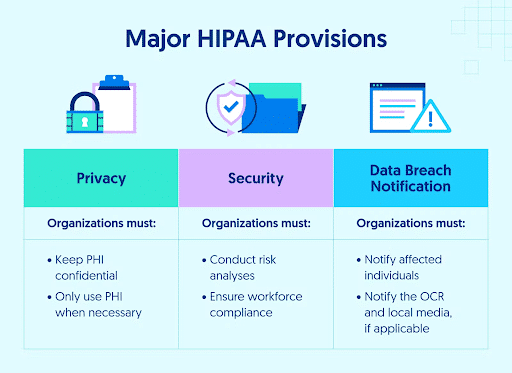
HIPAA training typically zeroes in on the specifics of handling PHI, covering topics such as patient rights, the minimum necessary rule, and the protocols for reporting breaches. This includes coverage of the four HIPAA rules: the Privacy Rule, the Security Rule, the Breach Notification Rule, and the Omnibus Rule.
Privacy Act training extends beyond the healthcare sector to include principles applicable to any personal information handled by federal agencies.
The Department of Health and Human Services (HHS) suggests that HIPAA-related training should occur annually to maintain compliance with changing regulations and evolving cybersecurity threats. While the Privacy Act lacks explicit guidance on training frequency, embracing a yearly schedule for this training helps ensure that healthcare professionals are up-to-date with both regulatory frameworks.
Who needs HIPAA and Privacy Act training?
Under HIPAA, covered entities—including healthcare providers, insurance plans, and healthcare clearinghouses—and any business associates are legally required to provide training to their workforce on the policies and procedures relating to PHI.
Training is mandatory for all healthcare professionals, including doctors, nurses, administrative staff, and anyone who handles patient information.
The Privacy Act applies to federal agencies, setting rules for managing individuals’ personal information. While it directly impacts federal entities, it also requires training for healthcare organizations that interact with or manage government-funded programs.
What are the benefits of HIPAA and Privacy Act Training?
HIPAA and Privacy Act Training brings several practical benefits to healthcare settings:
- Increased HIPAA Compliance – It gets everyone up to speed on the dos and don’ts of patient data, helping avoid legal headaches and fines that come from non-compliance.
- Boosts Patient Confidence – When patients know their data is handled with care, it strengthens their trust in your healthcare services.
- Awareness and Vigilance – Training sharpens the ability of staff to recognize and act on privacy and security risks, reducing the chance of data mishandling.
- Lower Risk of Data Leaks – Armed with the right knowledge, staff can better prevent situations that might lead to data exposure or breaches.
- Culture Shift – Regular training embeds a strong privacy and security mindset among personnel, making it second nature to protect patient information and overall organizational cybersecurity.
What are the 3 core components of HIPAA and Privacy Act Training?
Effective HIPAA and Privacy Act Training focuses on three critical areas to guarantee that healthcare professionals are well-versed in privacy regulation compliance:
- Consent Requirements – Training emphasizes the importance of obtaining patient consent before using or disclosing their Protected Health Information (PHI). It outlines procedures for obtaining consent and explains when consent must be explicit.
- Limited Disclosure Principles – This part of the training teaches professionals to share the least amount of PHI necessary for a specific purpose. It provides guidance on determining what information is “minimum necessary” and the protocols for limiting disclosures.
- Data Storage Best Practices – These practices address secure methods for storing PHI, highlighting encryption, access control, and audit trails. It stresses the importance of both electronic and physical security measures to prevent data breaches and unauthorized access.
By mastering these elements, healthcare entities can foster a culture of security and privacy that allows them to confidently navigate HIPAA regulatory complexities.

What is the HIPAA and Privacy Act training challenge exam?
The HIPAA and Privacy Act Training Challenge Exam typically tests participants on their comprehension and knowledge of HIPAA and the Privacy Act, including how to apply them in practical, real-world situations. It might cover topics such as patient rights, the minimum necessary standard, how to handle and report breaches of PHI, and the responsibilities of covered entities and business associates under these laws.
This exam is often a part of mandatory training for employees in the healthcare sector, including hospitals, clinics, insurance companies, and other entities that handle personal health information.
Suitable for anyone who has completed the required training, the exam demonstrates that an individual has a foundational understanding of HIPAA and Privacy Act requirements, which is crucial for compliance and protecting individuals’ privacy. It also helps pinpoint topics or subject areas that may benefit from additional review.
20 HIPAA and Privacy Act Training Challenge Exam Sample Questions to Help You Prepare
To assist you in preparation for the HIPAA and Privacy Act Training Challenge Exam, we’ve collated a collection of example questions. These are similar to questions you may find on the Challenge Exam and offer an opportunity to self-test your HIPAA and Privacy Act knowledge.
To find the correct answers along with the questions, download the free Excel challenge exam sheet.
Questions:
1.Under what conditions should a person be allowed to approve or refuse the sharing of their Protected Health Information (PHI)?
- When their information is shared with third-party marketers
- Before their information is included in a facility directory
- Prior to sharing PHI that is directly pertinent to an individual’s participation in their care or healthcare payment
- All of the above
2. What truths about the HIPAA Security Rule are acknowledged?
- It mandates encryption for all stored PHI
- It establishes national standards for the protection of ePHI
- It addresses administrative, technical, and physical safeguards
- It applies only to electronic PHI (ePHI)
- All of the above
3. Is it mandatory for a covered entity to have a process for filing complaints?
- True
- False
4. Does the e-Government Act facilitate public access to electronic government services and enhance IT usage within the government?
- True
- False
5. What is the timeframe for reporting a breach to the U.S. Computer Emergency Readiness Team?
- Within 72 hours of discovery
- Within 1 hour of discovery
- Within 24 hours of discovery
- Within 48 hours of discovery
6. Which statements accurately reflect the Privacy Act’s provisions?
- It allows unrestricted sharing of PII with third-party marketers
- It balances individual privacy rights with the government’s information collection needs
- It governs federal agencies’ collection and handling of PII
- It outlines how PII should be used, maintained, and disclosed
- All of the above
7. What are the categories of penalties for violating federal healthcare laws?
- Criminal penalties
- Civil money penalties
- Sanctions
- Warning notices
- All of the above
8. What are the common causes of data breaches?
- Theft and intentional unauthorized access to PHI and PII
- Human error
- Lost or stolen electronic media devices or paper records
- All of the above
9. What are the fundamental goals of information security?
- Confidentiality
- Integrity
- Availability
- Profitability
- All of the above
10. Where can an individual file a complaint if they believe a DoD-covered entity is not complying with HIPAA?
- DHA Privacy Office
- HHS Secretary
- MTF HIPAA Privacy Officer
- Local Police Department
- All of the above

11. Define technical safeguards in the context of HIPAA.
- Physical locks and keys for securing paper records
- Policies and procedures designed to protect ePHI and control access to it
- Training programs for healthcare staff
- All of the above
12. What does a Privacy Impact Assessment (PIA) evaluate?
- Financial impact of implementing IT security measures
- Compliance with privacy laws and policies
- Risks and effects of collecting and disseminating information in identifiable form
- Safeguards and alternative procedures for managing information to reduce privacy vulnerabilities
- All of the above
13. Is the DoD’s definition of a breach wider than what HIPAA defines?
- True
- False
14. What are some best practices for preventing breaches?
- Using strong passwords and changing them regularly
- Accessing the minimum amount of PHI/PII necessary
- Logging off or locking workstations when unattended
- Promptly retrieving documents containing PHI/PII from the printer
- All of the above
15. When is an incidental use or disclosure not considered a HIPAA violation?
- When the covered entity has not implemented the minimum necessary standard
- When the covered entity has implemented appropriate administrative safeguards
- When the disclosure benefits the covered entity financially
- When the covered entity has implemented appropriate physical and technical safeguards
- All of the above
16. Under the Privacy Act, can individuals request changes to their personal records within a system of records?
- True
- False
17. Which office within the HHS (Department of Health and Human Services) is responsible for supervising the security and privacy of patient health information under HIPAA?
- Office for Civil Rights (OCR)
- National Institutes of Health (NIH)
- Centers for Disease Control and Prevention (CDC)
- Food and Drug Administration (FDA)
- All of the above
18. What are physical safeguards in the context of HIPAA?
- Digital encryption and cybersecurity software
- Physical measures and policies to protect electronic systems and their physical environments from various hazards and unauthorized access
- Employee background checks
- Firewalls and antivirus programs
- All of the above
19. Which of the following is considered Protected Health Information (PHI)?
- Individually Identifiable Health Information (IIHI) in employment records by a covered entity in its employer capacity
- Anonymized data used for research
- Information shared within public health records
- Education records covered by FERPA
- All of the above
20. The minimum necessary standard requires that:
- The use, disclosure, and request of PHI be limited to the minimum necessary to accomplish the intended purpose
- It is not applicable when healthcare providers exchange information for patient treatment
- It is not enforced for disclosures to the patient or made with the patient’s authorization
- PHI should always be fully disclosed for any legal request
- All of the above
Simplify Your HIPAA Compliance with CybeReady’s Security Training
Data breaches involving patient information are on the rise. But while HIPAA and the Privacy Act were established precisely to prevent such events, the increasing sophistication of cyber attacks poses a constant challenge to healthcare organizations. The HIPAA and Privacy Act Training Challenge Exam provides a way for the staff of covered entities and business associates to keep their knowledge up-to-date while helping healthcare organizations maintain HIPAA compliance.
CybeReady is leading the charge in transforming organizational security cultures with its comprehensive cybersecurity awareness training platform, designed to meet and exceed HIPAA training requirements. Integrating CybeReady into your training strategy proactively bolsters your organization’s human firewall against data breaches and cyber threats with targeted, impactful learning experiences.
Contact CybeReady today to learn more and try a free demo.

![The Essential HIPAA Compliance Checklist [XLS Download]: 7 Steps to Medical Data Nirvana](https://cybeready.com/wp-content/uploads/Picture18.png)





