For organizations worldwide, safeguarding sensitive information to ensure its confidentiality, integrity, and availability is critical in an era of inevitable information breaches. Employing an Information Security Management System (ISMS) solves many infosec problems, but what’s the best way to set it up to support your organization’s long-term resilience and security strategy?
The solution is compliance with ISO 27001, an international standard outlining the framework for an effective ISMS offering a systematic approach to managing sensitive company information. A recent survey of CIOs showed that 80% plan to increase spending on information security in 2024, showing the vital need for data security practices like ISO 27001.
ISO 27001 ensures organizations implement a diverse array of security controls, spanning organizational, physical, technological, and personnel security measures—including cybersecurity awareness training. Understanding and complying with ISO 27001 is more than an industry requirement. It’s a strategic move towards fortifying your organization’s defenses against evolving cyber threats while providing a more secure operational environment.
What is ISO 27001?
ISO 27001 (ISO/IEC 27001:2022) is an international standard published by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) in 2005, and updated in 2013 and 2022.
ISO 27001 focuses on three key principles of information security: preserving the integrity, confidentiality, and availability of information. It comprehensively addresses data loss prevention and covers more than just IT security. It’s designed to help organizations manage and protect their information assets through an Information Security Management System (ISMS) regardless of their size or sector.
The standard’s robust ISMS framework includes the latest best practices in information security management. It emphasizes a risk management process that requires organizations to identify and treat security risks tailored to their specific needs.
Who is ISO 27001 for?
Compliance with ISO 27001 is vital for organizations that manage significant amounts of data, including sensitive or proprietary information, or those that operate within industries heavily regulated on data protection and privacy.
Organizations that must comply with ISO 27001 typically include those in the financial sector, healthcare, public sector, IT services, and any business that handles customer data on a large scale. Compliance is often driven by regulatory requirements, contractual obligations, or the need to build trust with customers and stakeholders in the security of their data.
Beyond mandatory compliance, ISO 27001 is beneficial for any organization looking to implement a rigorous approach to information security management. This includes startups wanting to establish robust security practices, technology companies looking to protect intellectual property, and multinational corporations needing to manage security across diverse geographical locations and business units.
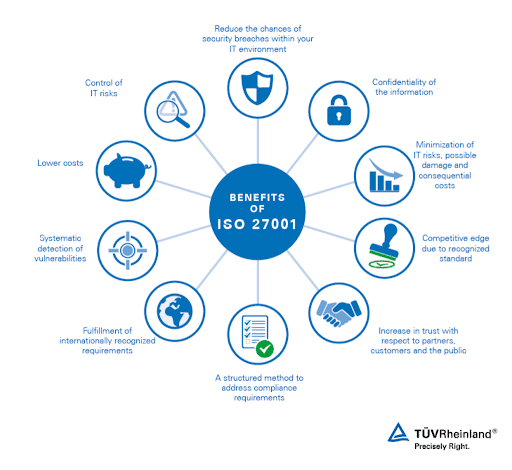
Benefits of ISO 27001 Compliance
ISO 27001 compliance offers many benefits:
- Enhanced Security Posture – Strengthens protection of information assets against cyber threats and breaches.
- Risk Management – Facilitates proactive identification, assessment, and management of information security risks.
- Regulatory Compliance – Helps in meeting legal and regulatory data protection requirements, reducing the risk of penalties.
- Improved Stakeholder Confidence – Boosts trust among customers, stakeholders, and partners by demonstrating a commitment to information security.
- Operational Efficiency – Streamlines processes and promotes a culture of continuous improvement, leading to greater efficiency.
- Competitive Advantage – Positions the organization as a trusted entity in information security, differentiating it in the marketplace.
How does ISO 27001 compliance work?
ISO 27001 is structured into several main clauses that outline the requirements for establishing, implementing, maintaining, and improving an Information Security Management System. Alongside these clauses, there’s Annex A, which provides a detailed list of control objectives and controls that organizations can implement within their ISMS.
Here’s a simplified look at how the ISO 27001 compliance process unfolds across fourteen distinct phases:
- Context Establishment – Understanding the organizational context, stakeholders’ needs and expectations, and the ISMS’s scope.
- Leadership Commitment – Ensuring top management’s involvement in and commitment to the ISMS.
- Planning – Identifying information security risks and opportunities, and establishing clear objectives to address them.
- Support – Allocating the necessary resources, ensuring competence, raising awareness, and documenting information.
- Operation – Planning, implementing, and controlling processes to meet information security requirements.
- Performance Evaluation – Monitoring, measuring, analyzing, and evaluating the ISMS’s performance.
- Improvement – Identifying and making necessary improvements to the ISMS.
- Risk Assessment – Systematically identifying and assessing information security risks.
- Risk Treatment – Implementing the necessary controls to treat identified risks.
- Objective Setting – Defining specific, measurable security objectives.
- Documentation – Maintaining documented information necessary for the effectiveness of the ISMS.
- Competence Development – Ensuring that all individuals involved in the ISMS are competent.
- Communication – Ensuring proper and effective internal and external communication regarding information security.
- Control Implementation and Management – Implementing and managing the controls necessary for risk treatment.
To assist with your compliance efforts and ensure a thorough understanding of each phase, download CybeReady’s free ISO 27001 checklist. It will guide you through the compliance process, ensuring that no critical steps are missed in your organization’s quest to meet the standard’s requirements.
10 Steps to ISO 27001 Compliance
Becoming ISO 27001 compliant involves a structured approach that focuses on establishing and maintaining an ISMS. Here are the ten necessary steps:
1. Understand the Standard
Start by getting a solid grasp of the ISO 27001 standards and what they require. Ensure your team knows the principles and processes inside out, as this will form a strong base for your ISMS. Knowing these standards well will make the rest of the process smoother and ensure you meet international security benchmarks.
2. Conduct a Gap Analysis
Do a gap analysis to see how your current security measures stack up against ISO 27001’s standards. This step will show you where you need to improve, helping you focus your efforts on areas with the most impact.

3. Define the Scope
Clearly spell out what parts of your organization the ISMS will cover. This helps ensure your ISMS is focused and manageable, covering all the important areas without becoming too unwieldy.
4. Establish a Management Framework
Put in place a management framework that will guide the setup, operation, and improvement of your information security. This framework will help you keep everything organized and on track as you work to enhance your organization’s security.
5. Perform Risk Assessments
Run risk assessments to identify and evaluate threats to your information security. Understanding these risks is key to determining which controls are needed to protect your organization.
6. Implement Controls
Apply the necessary controls from Annex A to tackle your identified risks. This step involves using both technical tools and organizational policies to beef up your security.
7. Train Employees
Educate and train your employees about their roles in the ISMS, enhancing the overall organizational security culture and ensuring that employees are aware of, and proactive, in the face of potential security threats.
CybeReady offers regular, up-to-date training sessions that enhance employees’ ability to identify, report, and prevent security incidents, aligning with ISO 27001’s focus on continuous improvement and effective risk management.
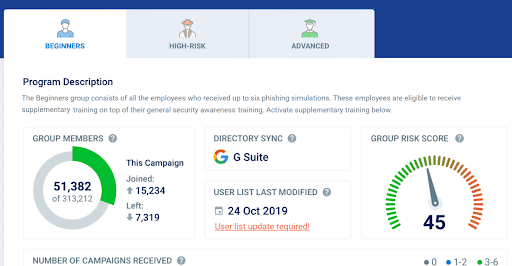
8. Monitor and Review
Keep a close eye on your ISMS and regularly check how well the controls are working. This ongoing review process lets you spot and fix any issues, ensuring your security measures stay effective against evolving threats.
9. Internal Audit
Conduct internal audits to make sure your ISMS matches up to ISO 27001 standards and your own security needs. These audits are crucial for keeping your security practices up to scratch.
10. Certification Audit
Finish up with a certification audit from an accredited certification body. This final review checks that your ISMS is solid and effective, showcasing your dedication to maintaining high security standards.
Cybersecurity Awareness Training and ISO 27001 Compliance
Cybersecurity awareness training is essential for meeting the ISO 27001 mandate under clause 7.2.2, “Awareness.” The clause demands that all personnel be informed about the information security policy, comprehend the consequences of security breaches, and acknowledge their responsibilities toward maintaining security.
Additionally, clause 7.2, “Competence,” ensures that employees can perform their assigned security roles—which implicitly requires appropriate training, education, or experience.
By placing a strong emphasis on educating employees about information security principles, the specific threats to the organization, and their role in safeguarding against these threats, cybersecurity awareness training tackles the risk of breaches caused by human error—one of the most common culprits behind security incidents.
Ultimately, cybersecurity awareness training is a foundational element that significantly enhances an organization’s ISMS.
CybeReady Boosts Your ISO 27001 Compliance Efforts
ISO 27001 sets the global benchmark for an effective Information Security Management System by providing organizations with a rigorous approach to managing sensitive information and mitigating the risk of information breaches. It helps organizations protect their information assets, comply with regulations, and build customer and stakeholder trust.
A crucial component of achieving ISO 27001 compliance is robust cybersecurity awareness training. CybeReady’s training programs are engaging, measurable, and, most importantly, effective. They equip your workforce with the knowledge and skills needed to protect against the ever-changing landscape of cyber threats. In addition, the AuditReady compliance tool helps prepare employees for compliance and provides proof of training.
Contact CybeReady for a free demo to see how we can help your organization boost its ISO 27001 compliance efforts.





![The DORA Compliance Checklist [XLS Download]](https://cybeready.com/wp-content/uploads/Picture1-15.png)











