When cybercriminals look at an organization rich in data and digital assets, they see a vault full of treasure—and any one of your employees or authorized users has the potential to provide the key. Whether the goal is to steal data or hold the entire organization hostage to a ransomware attack, it only takes one person falling prey to a phishing attack to open up a catastrophic breach.
Incidents are rising, with credential phishing attacks increasing by 40% over last year. It starts with an official-looking email, from a seemingly trusted software vendor like Microsoft, asking users to click a link and confirm their username and password. The phisher’s odds of success are good: one in three users will make the wrong choice when faced with a phishing attack. Having gained a foothold into the network, the attacker can exploit your data, which nearly always results in significant losses.
Phishing prevention is a critical element of any cybersecurity plan, and just warning users not to click on suspicious-looking links isn’t enough. Sophisticated phishing attacks can sometimes fool even seasoned security experts, and prevention doesn’t end once the malicious link is clicked and the wheels are in motion. To give your organization the best chance at staying secure, follow these ten tips vetted by industry professionals.
Why Preventing Phishing is Critical for Businesses
Cybercriminals know there’s rarely any need to invest in brute force attacks or complex software exploits when tried-and-true deceptive tactics will suffice. Nearly three-quarters of data breaches involve the exploitation of human vulnerabilities, and phishing attacks make it easy to target a large number of users and play the odds that at least one of them will take the bait.
A data breach or ransomware attack can damage organizations’ finances, reputation, and internal morale. Phishing attempts are the most common precursors to these attacks, and every organization needs a phishing protection strategy for dealing with them.
The 4 Layers of Phishing Prevention
Phishing is only the beginning of a multi-step process that ends with a breach. Several things have to work in the phisher’s favor for the attempt to be successful, and organizations have multiple opportunities to detect and thwart an attack that starts with phishing. The optimal defense, therefore, requires a multi-layered approach.
First Layer: Prevent Attackers from Reaching Your Users
Email filters and anti-spoofing tools can reduce the number of phishing emails that make it to users’ inboxes. You can also make it harder for attackers to create convincing spoofs of your organization’s emails by instituting strong information security practices.
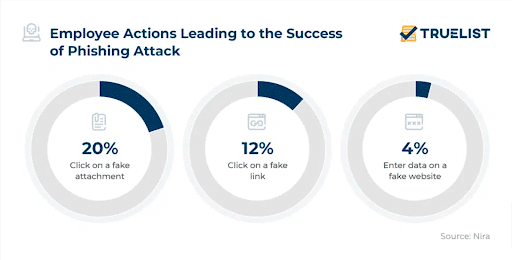
Second Layer: Help Users Identify and Report Phishing Attacks
Phishing communications are designed to be convincingly deceptive. Users within your organization need comprehensive training in identifying generic phishing messages and targeted spear phishing attacks. They also need the support of an organizational culture and procedural framework that makes it easy to report phishing attempts promptly, even if they think they erred in clicking a malicious link. Penalizing phishing victims for coming forward only serves the interests of cybercriminals by delaying your chance to respond.
Third Layer: Protect Your Organization from Successful Phishing Attacks
Not every attack will be detected in time to stop it. Your prevention strategy needs to account for phishing attempts that make it past the first line of defense. Utilize cybersecurity solutions that block malware and unsafe websites, make sure all of your critical applications are patched and updated, configure the administrative controls on your network to prevent regular users from installing new software, and follow best practices for password security and multi-factor authentication.
Fourth Layer: Respond to Incidents Quickly
Develop an incident response plan that ensures that fast and effective actions can be taken as soon as a security incident is detected. By encouraging early reporting, monitoring your network constantly, and maintaining detailed access logs, you stand the best chance of detecting and mitigating a breach in progress and protecting your data before any major losses occur.
10 Phishing Prevention Best Practices
Here are ten different ways that the pros swear by to prevent phishing attacks, covering all four protective layers:
1. Regular Employee Training in Cybersecurity Awareness
The basics of phishing detection may be simple enough to convey, but regular, ongoing training ensures that this essential knowledge will always be fresh in users’ minds. Engaging training platforms like CybeReady can keep your employees dialed into timeless core skills while providing up-to-date education about new threats and evolving cybersecurity practices, leading to effective organizational cyber resilience.
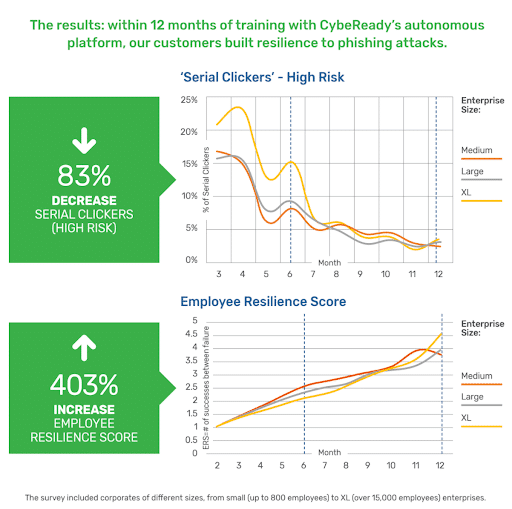
2. Phishing Simulations
Slides, videos, and other forms of passive content aren’t enough if you want users to really understand what phishing looks like and how to respond. CybeReady provides a dynamic phishing simulation tool that allows them to evaluate suspicious messages that land in their inboxes and make real-time decisions about how to react.
3. Take Down Spoofed Websites
Phishing attempts often come paired with a spoofed website designed to keep the ruse going once the user clicks the malicious link. If the website looks perfectly professional and legitimate, it just takes that much longer before the victim realizes something is amiss—and at that point, it’s often too late. Anti-spoofing solutions can help you identify and remove impostor websites before they deceive your users.
4. Authenticate Email Servers
Email authentication protocols like DKIM, DMARC, and SPF can verify that email senders are who they say they are, allowing you to block the forged emails commonly used by phishers. By implementing these protocols at the server level, you can set up automatic filtering for incoming messages that falsely claim to originate from trusted domains.
5. Institute Zero Trust Security
Zero Trust is an approach to cybersecurity based on the idea that digital trust should never be given implicitly. Every access request needs to be authenticated, and data modification rights should only be granted when justified by a legitimate organizational need. Implementing the Zero Trust model means that even if phishers obtain a password and get into your network, they won’t have free reign to view and overwrite all of your data.
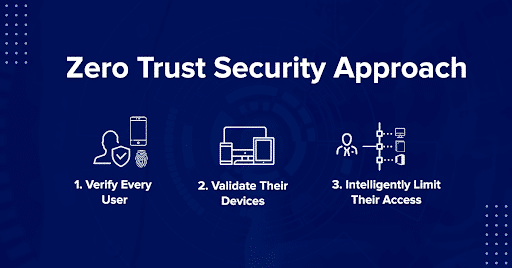
6. Set Up Access Controls
If you’re adopting the Zero Trust approach to cybersecurity, you’ll need a way to exercise fine-grained control over who can access your data. Identity and access management solutions can provide you with these necessary controls, along with monitoring and risk mitigation tools to help you make better decisions about protecting your data should attackers succeed in breaching your first-layer network defenses.
7. Encryption
Encrypting your data, especially sensitive information like passwords and personally identifiable information about employees or customers, can leave cybercriminals who succeed in breaching your network with nothing to show for their efforts. Internet traffic and cloud-stored data should also be secured with encryption, which is essential if remote workers are required to access privileged data and critical systems.
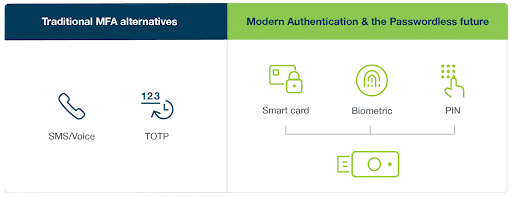
8. Multi-Factor Authentication and Passwordless Technology
Most phishers are laser-focused on obtaining login credentials to get them into the network, but usernames and passwords won’t get them very far if you use multi-factor authentication protocols. These are even more effective when the additional factors are based on passwordless technology that uses trusted devices, biometrics, or other verification methods that can’t be digitally shared or stolen.
9. Anti-Phishing Software Tools
As important as it is to train users to detect the red flags associated with phishing messages, AI-powered software can handle this task with remarkable accuracy. Anti-phishing software tools scan incoming messages for the telltale signs of phishing and will also catch subtle clues that would be easy for human eyes to overlook.
10. Filter Your DNS Traffic
DNS filtering solutions can prevent users from visiting known malicious websites, even if they click a link in a phishing email. These solutions block any access requests that are directed at blacklisted domains. Some DNS filters can proactively evaluate websites for potentially harmful code and add them to their list, even if they haven’t been reported and identified as hubs of cybercriminal activity.
Teach Your Workforce Not to Bite Phishing Lines
Aggressive cybercrime has become a ubiquitous and costly problem, and it frequently starts with phishing messages. These attacks are effective because they bypass automated technological defenses and target an organization’s vulnerable, unpredictable human element.
It’s vital to have a layered strategy that assumes some phishing attacks will succeed, but the best defense is to train your organization to anticipate, recognize, and report phishing attacks in all their forms. By providing personalized training modules and adaptive simulations, CybeReady is one of the most effective ways to make your organization as un-phishable as possible.
Request a demo for a hands-on experience with CybeReady’s engaging, versatile employee cybersecurity awareness training platform.