In this article, we’ll describe CybeReday’s approach to risk group classification, the challenges, and the results compared to other industry practices.
What is a Risk Group?
We see two common types of risk groups in cybersecurity:
- Defined by accessibility to company assets: This type of risk group is based on the level of access an employee has to critical company resources. Employees with access to sensitive information, financial assets, or high-level permissions are considered higher risk because a security breach involving them could have significant consequences. For example, a finance manager with access to company bank accounts or an IT administrator with control over the network infrastructure would fall into this category. The market commonly uses this definition to prioritize security measures around these key individuals.
- Defined by proneness to falling victim to cyber threats: his definition assesses how likely an employee is to engage in risky behaviors, such as clicking on phishing emails or unsafe links. This type of risk group is determined by analyzing an employee’s behavior patterns over time. For instance, an employee who frequently clicks on suspicious links or fails phishing simulations would be classified as a higher risk. This approach helps in identifying individuals who t are vulnerable to cyber threats due to their behavior.
At CybeReady, we focus on the latter definition.
To better understand this risk group classification, let’s consider how we evaluate a basketball player’s performance. A single game where the player scores poorly (point-specific) might not tell the whole story. If the player generally performs well over the season (trend-based), they are considered valuable. However, if the player has had a series of poor performances recently or has been recovering from an injury, these recent changes significantly impact their current evaluation.
Similarly, in cybersecurity learning environments, an employee might occasionally click on a phishing email (point-specific), but it’s their consistent behavior over time (trend-based) that truly matters. If an employee shows a recent pattern of risky behavior or ignores training, these changes should be reflected in their current risk classification.
Measurement Challenges
Determining employees’ phishing risk scores based on their performance in Phishing Simulations can be challenging due to several factors:
1. Behavioral Variability: employees’ behavior can change over time, making it difficult to consistently categorize them. For example, an employee might improve their cybersecurity practices after training but could revert to risky behavior if they become complacent.
2. Data Accuracy: Ensuring the data collected on employee behavior is accurate and comprehensive is crucial. Inaccurate data can lead to misclassification of employees, either underestimating or overestimating their risk levels. Additionally, email metrics can be significantly skewed by automated clicks generated by email security gateways and anti-phishing tools. These automated interactions can inflate click-through rates (CTR) and open rates, leading to misleading insights about user engagement. It is essential to implement filtering mechanisms to distinguish between genuine user interactions and automated clicks to maintain the integrity of email performance metrics.
3. Dynamic Threat Landscape: As cyber threats evolve, the criteria for what constitutes risky behavior must also be adapted. New types of phishing attacks or malware can change what behaviors are considered risky. It’s important to update your simulations and learning content according to your threat intelligence sources.
4. Training Simulation Performance: Relying solely on training simulations to determine phishing risk scores can be problematic. Employees might perform well in simulations but still fall for real phishing attempts due to differences in context and pressure. This highlights the issue of Learning Transfer, where skills learned in a training environment (close transfer) may not fully apply to real-world situations (far transfer). Additionally, simulations might not cover all possible phishing scenarios, leading to an incomplete assessment of an employee’s risk.
CybeReady Unique Measurement Methodology
Our risk calculation methodology looks at various employee behavior factors to determine an employee’s overall risk score.
This includes recent and historical email interactions with different weights based on time from attack and behavioral patterns differentiating consistent from sporadic interaction etc.
employees are then placed into three different risk groups: high, medium, and low based on the probability of them clicking the next simulation.
Below is a comparison table between CybeReady’s risk score calculation approach and the simple Click-Through Rate (CTR) calculation.
This table highlights the key differences between the two approaches, showing how CybeReady’s method is more comprehensive and tailored for cybersecurity, while CTR is a simpler metric used primarily in marketing.
| CybeReady’s Risk Score Calculation | Simple Click-Through Rate | |
| Purpose | To evaluate user vulnerability to phishing attacks and overall expected security behavior. | To measure the effectiveness of online marketing campaigns by tracking the ratio of clicks to views. |
| Factors Considered | User behavior patterns, training performance, historical data. | Number of clicks, number of impressions. |
| Complexity | High – involves multiple data points and historical analysis. | Low – straightforward calculation using basic metrics. |
| Output | Comprehensive risk score indicating potential vulnerabilities. | Percentage representing the click-through rate. |
| Use Case | Enhancing cybersecurity by identifying and mitigating risks within an organization. | Optimizing digital marketing strategies and improving ad performance. |
| Data Requirements | Detailed user interaction data, training results, and historical performance data. | Basic metrics such as clicks and impressions. |
| Calculation Method | Combines various weighted factors to produce a risk score. | Simple division of clicks by impressions, multiplied by 100. |
| Actionable Insights | Provides targeted training and interventions to reduce risk. | Helps refine marketing tactics and improve engagement rates. |
How do we utilize risk groups in our training programs?
CybeReady employs a multi-faceted approach to improve risk scores:
1. Intensive Training: We provide more frequent and targeted training sessions to high-risk employees to improve their response to threats. This can include simulated phishing attacks and more opportunities to interact with learning content that is designed to engage employees and reinforce good practices.
2. Behavioral Analytics: We use advanced analytics and Machine Learning models to monitor employee behavior and identify patterns that indicate vulnerabilities. This allows us to provide personalized training to employees, helping them improve their cybersecurity practices.
3. Gamified Communication: At the end of each learning cycle, we communicate overall performance to employees through a scorecard. This scorecard aggregates data from multiple sources, providing employees with a clear picture of their progress and areas for improvement. This approach helps to enhance employee engagement and performance by making them more aware of their cybersecurity posture.
Our methodology in practice
To demonstrate the logic guiding our methodology, let’s examine the first principle of “Intensive training” by looking at the effect of our training program on an average “High-risk” employee.
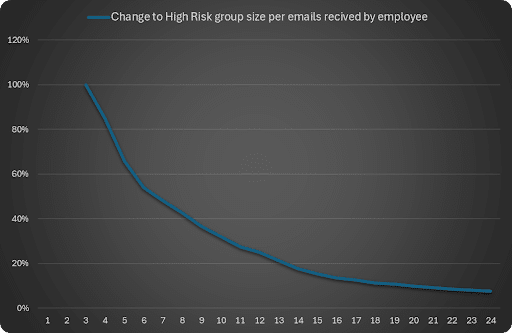
*The data represented above is based on a sample of around 30M sent attacks.
As you can see, with each tailored email sent to employees the size of the High-risk group is diminishing, reaching an average drop of about 80% in group size after 12 sent emails.
A simple example of applying our methodology is allowing a dynamic program to double the frequency of sent emails based on risk groups, by doing so, a company can get 12 emails and a 20% drop mark in half the time it would normally take!
To sum it all up, by utilizing a methodical approach to measuring and applying it to the training process, we help organizations enhance their cybersecurity posture and reduce overall risk.
Our approach ensures that employees are not only aware of the threats they face but are also equipped with the knowledge and skills to protect themselves and their organization.



















