With Halloween approaching, many are ready for ghosts and costumes. But online, the real threat is from websites masquerading as authentic—but aiming to deceive.
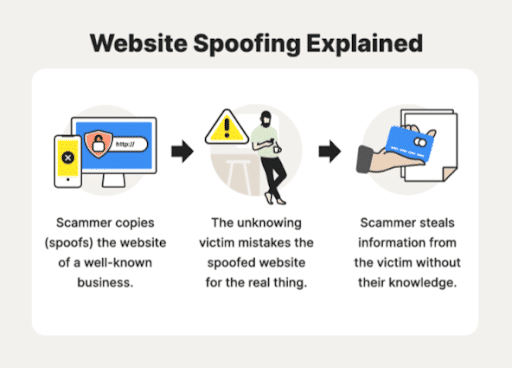
Spoofed websites are insidious duplicates of genuine sites, aiming to trick users into sharing sensitive data or downloading malicious software. They are masterfully disguised as banks, eCommerce platforms, and other trustable entities.
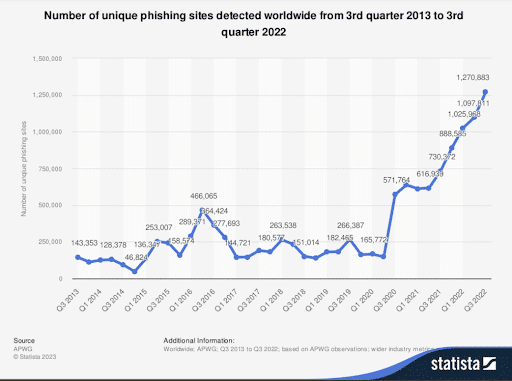
These increasingly prevalent scam websites cost users an astounding $8.8 billion in 2022. Despite cybersecurity training’s evolution, a glaring gap remains: identifying websites in disguise.
The Digital Disguise
The pandemic saw the beginning of a surge in deceptive websites. Shockingly, research indicates that nearly 78% of people have faced brand impersonation scams, meaning in the U.S. alone, a staggering 200 million+ have encountered spoofing.
How are these deceptive doppelgangers crafted? Some methods include:
- Cloning – Exact replicas of legitimate websites aiming to steal credentials
- Mirroring – „Mirrors“ of legit download sites harboring malicious content
- Typosquatting/Domain squatting – Domains mimicking popular websites, often exploiting typographical errors to ensnare unsuspecting users
- Brandjacking – These mimic genuine online retailers, either peddling fake goods or merely pilfering payment data
- Scareware – Sites falsely alarming users about PC infections, pushing fake solutions that are usually malware-laden
Sadly, businesses often remain oblivious to these threats until significant damage ensues—either financially or reputationally.
While software solutions provide ample security against fake websites, most threat intelligence and safe browsing solutions are lacking. That means it’s up to humans to spot these ghouls in the wild—but the problem is, most employees aren’t getting the proper training.
The Monster Mish-Mash
The importance of website spoofing in cybersecurity training can’t be overstated. Yet, it’s not addressed in many cybersecurity training programs due to a monster mish-mash of factors: outdated methodologies, not keeping pace with the threat landscape and resource constraints.
Traditionally, training has centered around foundational cybersecurity aspects, sometimes sidelining emerging threats like spoofing. These programs often view spoofing as more of an end-user problem rather than a grave cybersecurity challenge.
A significant challenge is that website spoofing doesn’t just exploit technical vulnerabilities but also human psychology. Ever-evolving cyber threats make it hard for training regimes to stay updated. Developing in-depth content can strain organizations, leading them to prioritize other areas they consider more urgent.
As ghosts say, „Boooo!“
Who are you gonna call? Spoofbusters
Addressing this training gap is vital in stopping websites in disguise from perpetrating more phishing attacks, malware spread, and data breaches. Training your employees to better identify variations of spoofed websites and their associated email schemes will bolster your defense perimeter and further enhance a culture of cybersecurity awareness.
To help you with this task, here’s a Halloween treat: a list of common scams and actionable strategies to unmask and avoid the fraudsters:
Business Email Compromise
A seemingly legitimate request for a money transfer is sent to employees. Here’s how it works:
- A request is sent from someone you know—but their name is displayed with a different email address.
- The request references real people within your organization.
- The email probably contains a thread, crafted to look like an executive team member has approved the transfer.
- The email will probably ask you to do something within your role.
- You may be asked to go to a website (like a spoofed PayPal) to complete the transfer.
- Always double-check requests with a colleague or manager.
Phishing
Phishing emails impersonating a legitimate person or company attempt to steal your confidential or personal data. Here’s how to detect it:
- Review the sender’s email address (not their display name). Verify that it’s what you expect.
- If a link appears in the email, hover over it to verify that the website is recognized and seems legitimate. Pressing and holding down on the link would reveal the website address on mobile phones. Don’t open the link unless you’re certain it’s legitimate. A phishing email is trying to send you to a spoofed site that may be dangerous.
- Reread the email. Suspicious signs: It’s vague, threatening in tone, or trying to persuade you to take action.
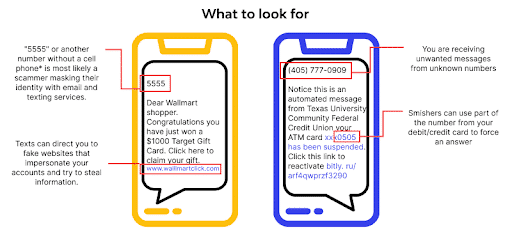
Smishing
Hackers exploit our false confidence in text message security to steal personal information through smishing (SMS + phishing). Here’s how to avoid it:
- Consider text messages with links or requests as unsafe and avoid clicking on or responding to them.
- Be skeptical of urgency. Rewards or scare tactics, like ‚urgent update‘ and ‚limited offer,‘ are common tactics to get you to click faster.
- The best protection is to do nothing. Malicious links can’t harm you if you don’t click on them. Use the „Report and Block“ option and move on.
Social Engineering
This term describes psychological manipulations that coerce people into actions that are essentially bad for them. Social engineering can draw unsuspecting individuals to spoofed websites through phishing emails, smishing, vishing, baiting, and pretexting.
To identify this scam:
- The fraudsters will try to make you believe they have some authority (since people tend to comply with authority).
- They will use vague phrases, letting you ‚connect the dots‘ on your own and raising your confidence.
- Most people want to help others. These fraudsters exploit altruism by pretending to be in dire need.
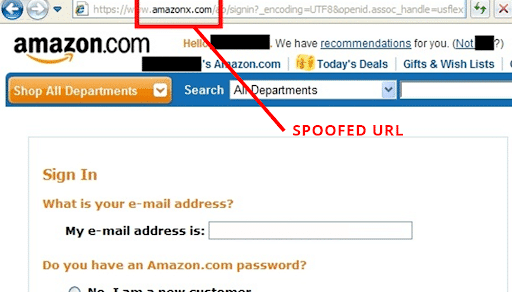
Spoofed Websites
If you find yourself on a website that smells like a stale jack-o’lantern, here’s what to look for to determine if it’s a website in disguise:
- Ensure the website’s URL matches the official site’s domain. Watch out for subtle misspellings or extra characters.
- Secure sites typically start with „https://“ instead of „http://“. However, while HTTPS indicates encrypted data transfer, it doesn’t guarantee the site’s legitimacy.
- Most browsers show a padlock icon next to secure websites. Clicking on this icon can reveal the site’s security details and certificates.
- The site has poor grammar, outdated graphics, or low-resolution images.
- Unexpected pop-up windows are asking for personal information or login details.
- Use domain lookup services like Whois to see when the website was created. New registration dates can be suspicious.
- If you’re still unsure, ask a colleague or your IT department.
I Ain’t Afraid of No Ghost
With these tips, you’re ready to exorcise the ghosts of scam websites in disguise. This Halloween, don’t let a website in disguise inside. Instead, use your cybersecurity awareness culture to keep the tricksters away so you can enjoy your treats without fear.
If your organization needs robust, engaging, and up-to-date employee cybersecurity awareness training that includes phishing simulations and information on detecting spoofed websites, contact CybeReady for more details.



















