By Mike Polatsek, CybeReady Co-Founder and CSO
When a phishing email lands in employees’ inbox, will they take time to review their Awareness Training notes before clicking it?
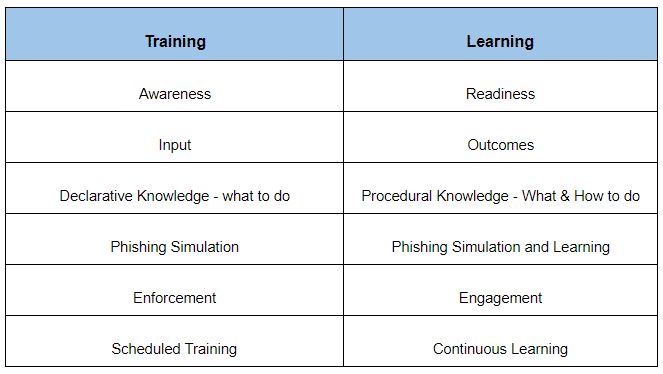
Probably not, which is why traditional awareness training programs offer an ineffective cybersecurity practice. When it comes to teaching employees how to remain vigilant against cybersecurity risks, the difference between declarative (theoretical) knowledge and procedural knowledge is truly critical. Unlike training, learning is a continuous process that relies on procedural knowledge and is measured by behavioral change rather than test results.
Take driving a car, for example. The first step towards obtaining a driver’s license is usually to pass a written test, which requires a certain understanding of the rules and procedures involved in operating a vehicle: when to use a turn signal, how to interpret road signs, etc. This is theoretical knowledge. However, passing the final driver’s test — and becoming a safe driver — requires procedural knowledge that can only be gained from practice and repetition. You’ll need to know, instinctively, how hard to press the brake pedal in order to stop the car on time, or how to respond when your car hits a patch of ice. Without developing real-life skills, will you have the instincts to execute the right move under pressure?
Most cybersecurity training programs are based on declarative knowledge, which relies on memorization. They might explain the theory behind security awareness to employees, but they don’t provide the practice, repetition, feedback and challenge that comes with developing procedural knowledge, and therefore they fail to change employee behavior over time.
We all know that traditional awareness training doesn’t lead to lasting results. Because it’s so important to know the difference between learning and training when choosing a cybersecurity awareness solution for your organization, let’s delve into this topic a little further.
Jump to a section…
- After 20 years, traditional training still falls flat
- Hands-on learning vs. IT security awareness training
- The vision behind CybeReady
After 20 years, traditional training still falls flat
Cybersecurity has gotten extremely sophisticated over the last 20 years, but as technology evolves, so too do threats like phishing scams. The scam emails of today are far harder to detect than those sent by hackers in the 1990s and 2000s, yet they still require split-second responses.
After decades of “training,” why do organizations still fall prey to cyberattacks? Traditional IT security awareness training simply doesn’t account for learning outcomes and fails to move the needle. These programs only provide sporadic engagement, and the lessons therein are usually just theoretical. But even focusing on continuous engagement isn’t enough. You have to train employees’ abilities under pressure to expose them to a variety of scenarios — in what psychologists Irving Janis and Leo Mann, in their 1979 book Decision Making: A Psychological Analysis of Conflict, Choice, and Commitment, describe as “hot conditions.” The key to performance under hot conditions is practicing on a variety of scenarios. This is what transforms procedural knowledge and makes it a habit.
When a phishing email lands in an employee’s inbox, chances are they won’t be taking the time to review their training notes. That kind of thing is for “cold conditions,” when the threat is purely theoretical (like a quiz). In reality, opening an email is a split-second decision — the kind made under fire, in hot conditions. Marines, fighter pilots, and police train for hot conditions, and the same approach better be used when it comes to cybersecurity. In these fields, research shows that the most effective way to ensure learning outcomes is through experience or simulations. That’s why simulations are the cornerstone in the Learning methodology.

Hands-on learning vs. security awareness training
One thing that sets great cybersecurity training solutions apart from average ones is the understanding that true, procedural learning is key to any educational foundation. Training is the input, it provides the educational material. You can memorize cybersecurity tips, but if you don’t practice them, can they really be applied effectively, when it matters most?
Another crucial aspect lies in the use of real-time feedback in a variety of conditions. Nuanced lessons such as those involving cybersecurity are best addressed by feedback that comes immediately after the actual performance. In traditional cybersecurity training, employees are told what to watch out for and how to behave. But the lack of effective feedback means that those lessons don’t tend to stick. With a procedural learning methodology, however, feedback is contextual, relevant and immediate, providing a much deeper level of knowledge and mastery. When an employee makes a mistake during our learning program, he or she is corrected in real-time, before the memory has a chance to dissolve in the mind, and the error is explained in the context of the situation. This helps learners connect the dots much more effectively and better prepares them to change their habits for the next time they’re presented with a similar challenge.
Another core way procedural learning differs from traditional cybersecurity training lies in the way it addresses employee motivation. We see motivation as a personal and dynamically changing phenomenon. Not everyone is self-motivated to strengthen cybersecurity, but they are self motivated to succeed in the face of challenges. The key to maintaining motivation and engagement is in the difficulty level of the challenge: too easy and people won’t feel challenged or proud of their accomplishments, too difficult and they’ll get frustrated. Therefore we strive to strike the right balance in presenting questions that challenge learners without overwhelming them. We do this on an adaptive basis depending on which stage each individual is at, and what they’re ready to learn next. The motivation that stems from this tension between failure and success is a great way to foster engagement with our program and ensure that lessons are internalized and behaviors changed.
To increase motivation, we also utilize an empathetic, positive, and tolerant approach. Instead of forcing employees into a long story about security, we simply provide the triggers. Procedural learning simulations aren’t a chore to get through. They’re quick, painless, and ongoing. There’s tolerance for mistakes, which allows people to analyze their failures and adjust behaviors accordingly.
To summarize, superficial training leads to short term results and doesn’t change behavior. In order to deliver lasting results and develop the right behaviors, cybersecurity learning must help employees identify threats and keep their organizations safe, which is the only true measure of success.
Think back to our driving analogy. Would you let your teenager get behind the wheel unsupervised, after only passing a written test? Of course not. To drive a car safely, they’ll need practice so that they can truly learn how to do it, receive real-time feedback and modify their skills. That’s why new drivers are required to accumulate hours of on-the-road learning in order to acclimate to all kinds of real-world conditions and ‘threats’ like variations in weather, speed limit, and traffic. Our approach to cybersecurity is similar. We provide employees the chance to practice and perfect their skills so that when they encounter an actual phishing email or a cyber scam, they instinctively know how to respond.
Ready to get started with the autonomous cybersecurity learning platform for enterprises? Request a demo to let our experts demonstrate how Cybeready’s solution can help your organization improve employee resilience.