Since 2020 and the start of the Covid-19 pandemic, the FBI has reported a300% increase in cybercrime. Cybersecurity is a priority for most companies across the globe, but effectively protecting your organization against threats is impossible without the necessary data, and that’s where threat intelligence comes in.
Threat intelligence is the information your organization uses to understand the threats that your organization has or will have to handle. Maintaining an adequate threat intelligence feed can help you handle cyberattacks faster by starting you off with the information you need to identify and manage threats.
This article explores what a threat intelligence feed is, its importance and relevance to your organization, and the best ones to monitor in 2023.
What is a Threat Intelligence Feed?
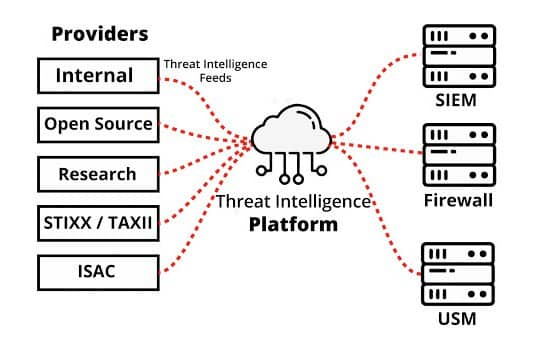
Threat intelligence feeds play an important role in modern cybersecurity tactics and are readily available online. These feeds track and maintain a record of IP addresses and URLs associated with cyber threats such as phishing scams, Trojan attacks, malware, spyware, ransomware, and more. The information these feeds provide can be extremely valuable – if you find the right source. Although many feeds are easily accessible, not all threat intelligence feeds are created equal. Even if, at first glance, it seems like the feed you’re exploring includes a regularly-updated database, it doesn’t guarantee that the information it contains is valuable or even accurate.
4 Types of Threat Intelligence Feeds
There are four primary forms of threat intelligence feeds, each serving a different purpose. While many choose to focus on the first three, each plays a critical role in providing a different type of information.
1. Strategic
Also known as a high-level intelligence feed, strategic threat intelligence feeds give insight into why certain attacks are carried out by threat actors. This feed is less technical and is generally used by C-level personnel to better understand the motives of an attack. External analysts outside the cybersecurity sector will often weigh in to offer a holistic perspective on the attack. Strategic threat intelligence feeds are critical to high-level personnel’s decision-making processes.
2. Tactical
Tactical threat intelligence feeds focus on managing threat actors‘ tactics, techniques, and procedures (TTPs). This feed is often used by Network Operations Center (NOC) andSecurity Operations Center (SOC) employees, IT service managers, and cybersecurity architects. These feeds help analyze the various TTPs attackers use to infiltrate your organization, including human intelligence, cross-industry cybersecurity statistics, data on malware attacks, incident and attack reports, and other data directly related to potential threats. Using this data, personnel can implement complex procedures such as patching system vulnerabilities, adjusting security implements (both hardware and software), and upgrading security strategies.
3. Operational
Operational threat intelligence is information pertaining to specific incoming attacks that can be acted on. By providing information on the identity and capabilities of the threat actor as well as the nature of the attack, a determination can be made of when the attack is expected to target an organization. Executive managers use this intel to build strategies and policies to protect the organization from incoming attacks.
4. Technical
Typically limited to a specific incident of compromise (IoC), a technical threat intelligence feed includes tools, command channels, control channels, IP addresses, phishing email headers, hack checksum of malware, and other technical data. This information provides vital insights into the resources, tools, and other variables a hacker has used. By understanding and properly analyzing this feed, you can act quickly in response to threats.
Threat Intelligence Feed Formats
While no single format is used for threat intelligence feeds, multiple record layouts have been formulated. In addition to the formats discussed below, it is important to know that threat intelligence feeds can also be provided in JSON and CSV formats.
STIX and TAXII
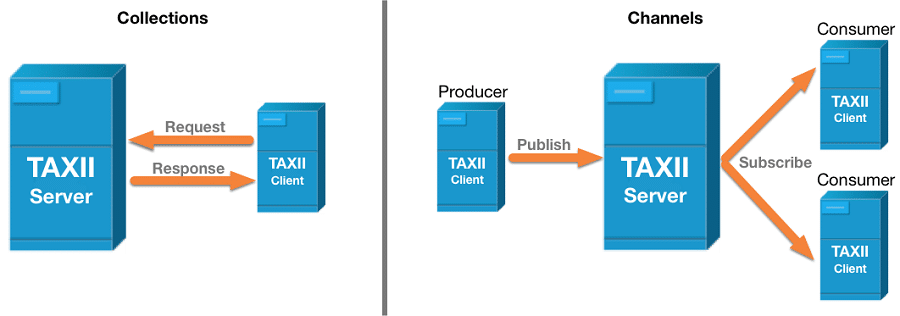
Structured Threat Information Expression (STIX) is a free, open-source project that is likely the best-known format for automatic threat intelligence feeds. Intended to formalize layouts for TTP records that specify actual threat strategies, STIX also includes information on the hacker teams behind the attacks. Trusted Automated eXchange of Intelligence Information (TAXII) provides a framework to organize and distribute STIX-formatted data using administrative protocols.
OpenIoC
Free to use, OpenIoC is an XML format standard used to communicate IoC data. This system can be difficult to integrate into automated generating and consuming processes due to the three sets of records it produces for each IoC – references, definition, and metadata.
MAEC
Malware Attribute Enumeration and Characterization (MAEC) is a project that uses open source to produce a variety of layouts that can be utilized for sending or extracting threat intelligence about malware. These formats offer languages that extract encoded data in a format that humans can read, encode data for use by tools, and automated tool-to-tool transmission. MAEC can be thought of as a programming language that explains the characteristics and behavior of each part of malware in a package that includes records of different formats.
What to look for in a Threat Intelligence Feed
When assessing threat intelligence feeds, there are a few factors you should take into consideration.
1. Assess what you need intelligence on
Threat intelligence feeds are your first line of defense, so it’s important to determine which threats you want your threat intelligence feed to be looking for. Using too many threat intelligence feeds can weigh down your system, so assessing your company’s specific security needs should be your first step.
2. Ensure your threat intelligence uses AI
While all threat intelligence feeds use some form of AI to perform automatic scans or to detect and analyze IoCs, only some utilize machine learning to generate predictive analytics and actionable insights. Having this intel is crucial to stay ahead of emerging threats.
3. Assess it for customizability
In order for the feed to generate data and insights most relevant to your company, you need a feed you can customize to your company’s particular needs. The type of threat changes based on the organization it’s targeting, so look for a threat intelligence feed that can be customized to your workloads, IT environments, and industry-specific compliance rules.
4. Look for a real-time feed
A real-time feed is a game-changer, allowing you to act quickly in case of an attack. The more time you have to prepare for an attack, the better you can act to prevent it.

5. Are the feeds usable?
Ensure the feeds received are useable for making timely and appropriate decisions. The data provided should be consumable, machine-readable, and actionable.
Top 8 Threat Intelligence Feeds to Monitor in 2023
1. AlientVault
AlienVault offers free access to more than 20 million threat indicators and allows for collaboration with over 200,000 global participants, including private companies, independent security researchers, and government agencies, to inspect emerging threats. Their service offers endpoint security and can be synchronized with other security products using DirectConnect API, SDK, and STIX/TAXII.
2. FBI: InfraGard Portal
The InfraGard Portal by the FBI includes information related to the critical infrastructure of 16 different sectors. With InfraGard, the FBI provides information regarding cyberattacks and threats they are actively tracking but also allows for private and public sector organizations to share security events and other information.
3. Emerging Threats
ProofPoint Emerging Threats provides the historical context of where threats originated, who is behind them, when they attacked, which methods of attack were used, and what attackers are trying to gain access to. They offer on-demand access to historical and current metadata on domains, IPs, and other relevant threat intelligence to help investigate and research incidents.
4. SANS: Internet Storm Center
SANS: Internet Storm Center is a global cooperative cyber threat security monitor and alert system. Their feed features handler diaries on a daily basis that summarize and analyze internet security events and new threats to networks.
5. DAN.me.uk
Dan compiles ten tools that report on domain and IP information. Their service includes the TOR status of IP addresses, DNS blacklists, IP subnets, node lists, and IP address checking for autonomous systems.
6. VirusShare Malware Repository
VirusShare is a repository of malware samples for security researchers, forensic analysts, incident responders, and others to gain access to live malicious code samples.
7. Abuse.ch URLhaus
URLhaus collects, tracks, and shares malware URLs to help network administrators and security analysts protect their customers and networks from cyber threats. Their data can be used for both commercial and non-commercial purposes, and it is possible to request a customized delivery mechanism if their APIs don’t fit your company’s needs.
8. Secure Malware Analytics (formerly ThreatGrid)
Secure Malware Analytics combines threat intelligence and sandboxing to protect organizations from malware. Using a context-rich malware knowledge base, you can analyze what the malware is attempting to do, how large of a threat it poses, and how to set up defenses against it.
| Feed | AI | Customizable | Real-Time | Predictive Analytics |
| AlienVault | ✔ | ✔ | ✔ | ✖ |
| InfraGard | ✖ | ✖ | ✖ | ✖ |
| Emerging Threats | ✔ | ✖ | ✔ | ✖ |
| SANS | ✔ | ✖ | ✔ | ✔ |
| Dan | ✔ | ✖ | ✔ | ✖ |
| VirusShare | ✔ | ✖ | ✔ | ✖ |
| URLhaus | ✖ | ✔ | ✖ | ✖ |
| Secure Malware Analytics | ✔ | ✖ | ✖ | ✔ |
Learn How CybeReady Can Help Your Threat Hunting
Perhaps the most important tool in your defense arsenal is education. By educating yourself and your employees about cybersecurity threats, you will be able to thoroughly analyze your security needs so you can make informed decisions about how to best protect your organization. CybeReady can help with custom and scalable security training for your entire company.
Find out how CybeReady can prevent your company from falling victim to a cyber attack.



















